- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- RUCKUS Self-Help
- Cloudpath: How to replace Radius Certificate on Cl...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cloudpath: How to replace Radius Certificate on Cloudpath if expired
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2023 01:25 PM - edited 12-07-2023 08:56 AM
This article explains how to replace Radius Certificate on Cloudpath if expired.
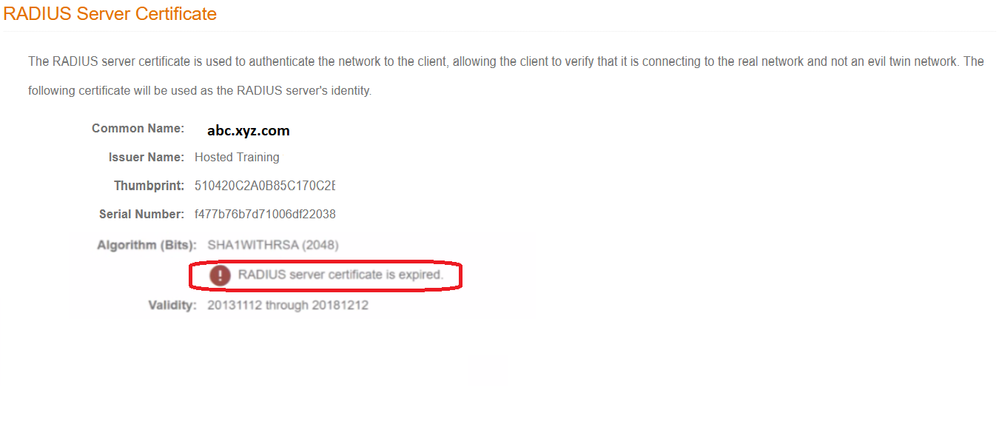
In many occasion you will see Customer has reported an issue with Radius authentication with Cloudpath server, all authentication requests will fail, from Cloudpath point of view you can identify the issue if the radius certificate is expired or not.
For client troubleshooting and pcap one can identify if the radius certificate is not trusted by the client, that also leads to certificate expiry or change in radius certificate.
NOTE:
Do not change the certificate comman name.
If CA is external make sure, the certificate is assigned by same CA.
All existing user authentication will fail in case above is not followed.
Steps to verify on Cloudpath:
- Verify if the Radius certificate is expired.>>>Cloudpath GUI>>>Configuration>>>Radius Server
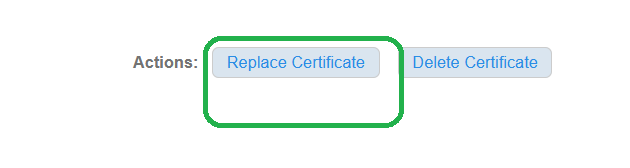
- Scroll down and Click on Actions: Replace Certificate
*********************************************************************************
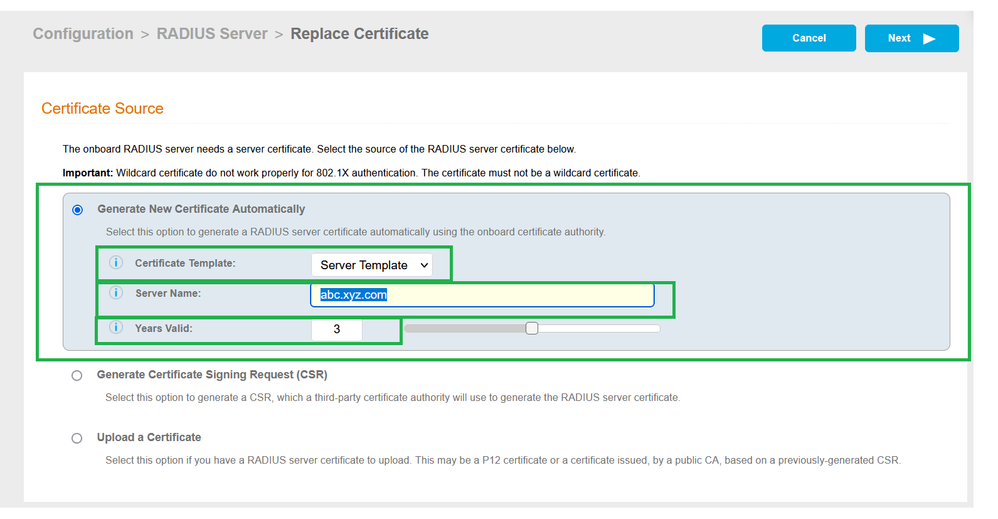
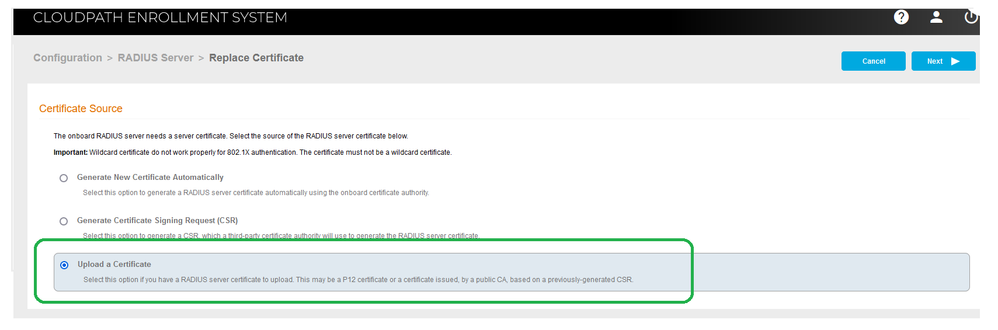
Very Few Customer uses External CA for Radius Certificate, Validate the Root Certificate of the expired Certificate, for External CA the steps are given at the end. - Select Generate New Certificate Automatically, if you have not imported the previous certificate from external CA.
>Certificate Template: will be selected as Server Template.
>Server Name: will be prefilled with the previous name, make sure it stays same as earlier.
>Years Valid: will be prefilled with the 3 Years, can be extended up to 5 Years.
On Success a new certificate will be assigned to the radius server with new validity.
***********************************************************************************
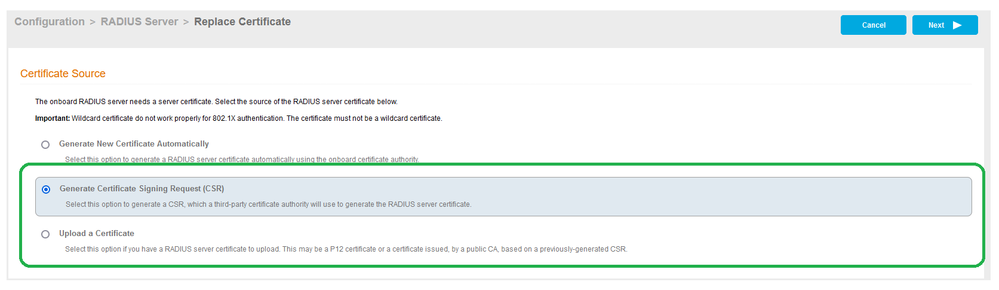
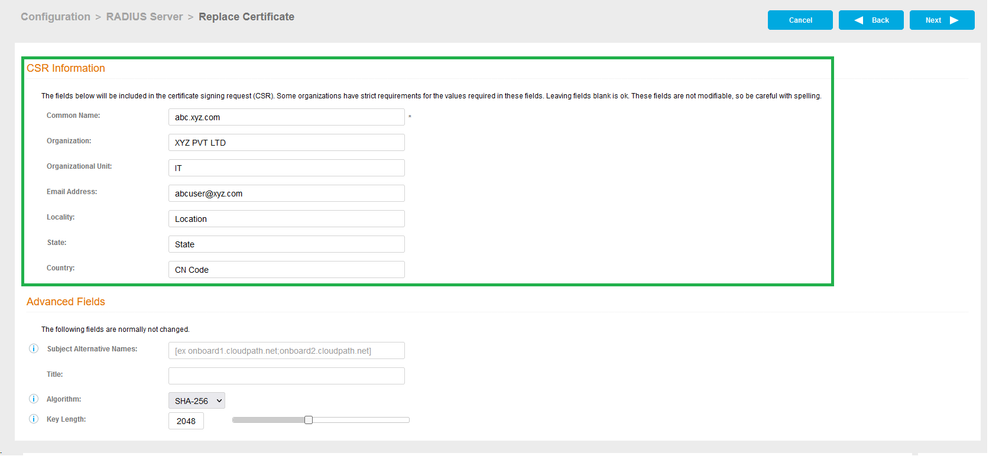
If you are using an external CA for radius certificate instead of Cloudpath Onboard CA use the Option to Generate CSR and Upload a Certificate. - Generate CSR (If Certificate is already there skip this part)
- Fill all the information and Click Next.
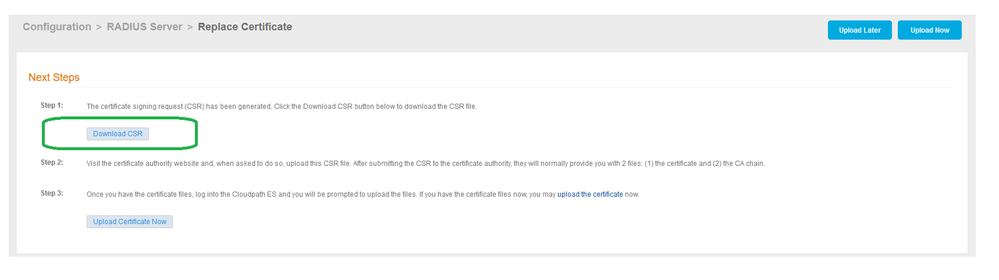
- Click on Download CSR
- Submit CSR to the CA and get a Certificate to upload in the next step.
- Fill in the fields with below details and Click Next.
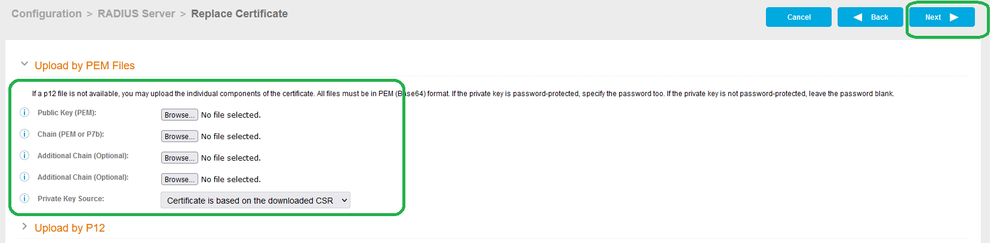
- Public Key (PEM) - Upload web server certificate received by CA in PEM format
- Chain (PEM or p7b) - Upload Root CA in PEM or p7b
- Additional Chain - Upload Intermediate CA in PEM
- Additional Chain - Upload Intermediate CA if chain have more than 3 certificate in PEM.
- Private Key Source - If certificate received was raised with the CSR from Cloudpath, select Certificate is based on CSR.
- Private Key Source - If certificate received was raised without a CSR from Cloudpath, select Upload Private Key.
- Private Key (PEM) - Upload Private key in PEM
- Private Key Password - If private key is password protected, enter password here, if not protected ignore. - Radius Certificate will be renewed.
Staff Technical Support Engineer
CCNA RnS | CCNA Wireless | CWNA | RASZA | Meraki CMNO | RACPA
- Labels:
-
Cloudpath
-
RUCKUS Self-Help
-
AAA
2 -
Access points
48 -
Analytics
3 -
AP Certificate error
1 -
AP Controller Connectivity
5 -
AP Management
8 -
AP migration
1 -
AP reporting
1 -
API
2 -
Authentication Server
2 -
Client Management
1 -
Cloud
20 -
Cloud ICX
1 -
Cloudpath
23 -
Cluster synchronization
1 -
Deployment
2 -
Firmware Recommendation
1 -
Firmware Upgrade
5 -
Guest Access
2 -
ICX
73 -
ICX Switch Management
7 -
Installation
5 -
IoT
1 -
Licensing
1 -
Mobile Apps
2 -
Monitoring
1 -
Poe
2 -
RADIUS
2 -
Ruckus Cloud
1 -
RUCKUS Self-Help
209 -
Security
6 -
SmartZone or vSZ
64 -
Stacking
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
UMM
3 -
Unleashed
15 -
User Management
1 -
Venue Management
1 -
Wired Throughput
2 -
Wireless Throughput
1 -
WLAN Management
5 -
ZoneDirector
15
- « Previous
- Next »