- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- RUCKUS Self-Help
- Re: Cloudpath Enrollment System SCEP integration w...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cloudpath Enrollment System SCEP integration with JAMF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2023 03:43 PM - edited 04-27-2023 03:18 PM
This article explains setting up a Cloudpath Enrollment System SCEP integration with JAMF for Apple device management.
Table of Contents
- Cloudpath Configuration
- JAMF Configuration
>CONFIGURATION PROFILE
>SCEP SETTING
>CERTIFICATE SETTING
>NETWORK SETTING
NOTE: JAMF User and user group mapping has not been covered in this module.
Cloudpath Configuration
Create a SCEP Key
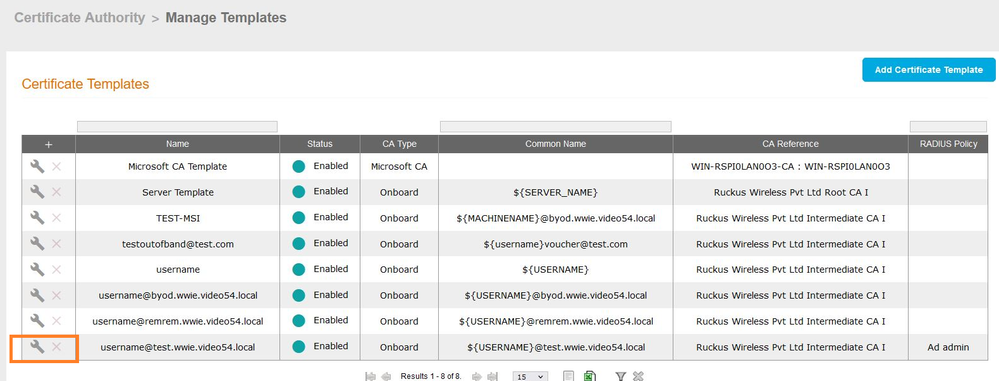
In the Cloudpath admin user interface, go to Certificate Authority>>> Manage Templates, then select the Certificate Template that will be used to issue the user/device certificates to the JAMF managed devices. Click on the “Manage” icon for the certificate template.
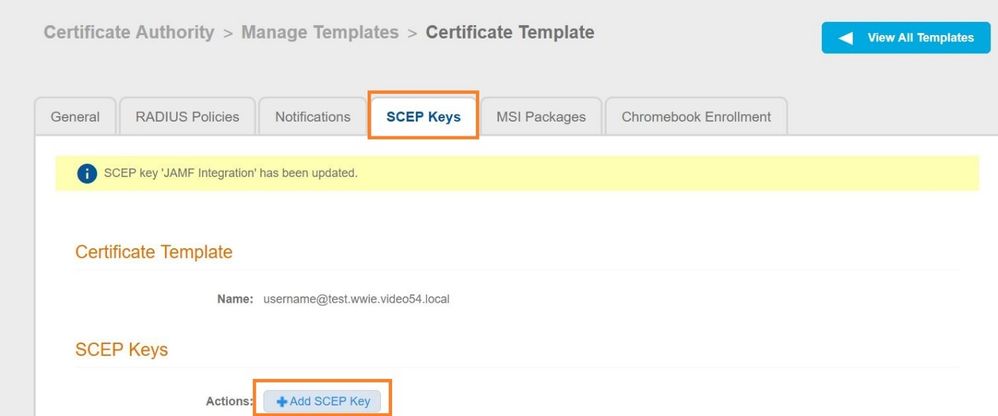
Select the SCEP Keys tab and under SCEP Keys , click on the “Add SCEP Key” button.
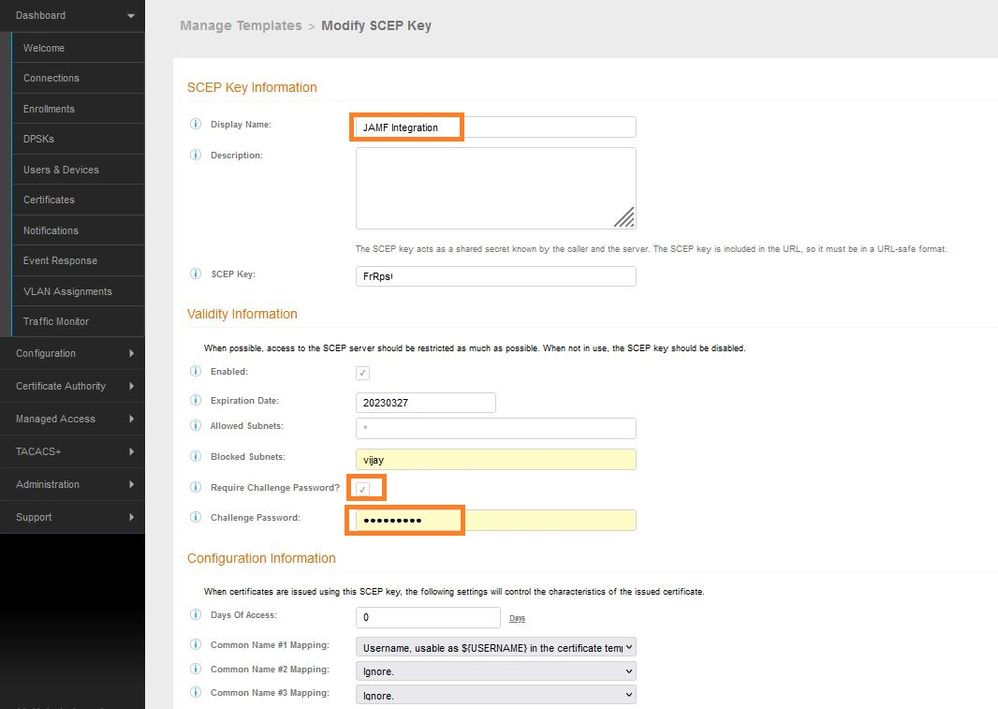
In the “Create SCEP Key” page, set a display name and description for the SCEP key. Set an expiration date if required. Select “Require Challenge Password” and enter password. Leave the Configuration Information section at the default settings. Click Save.
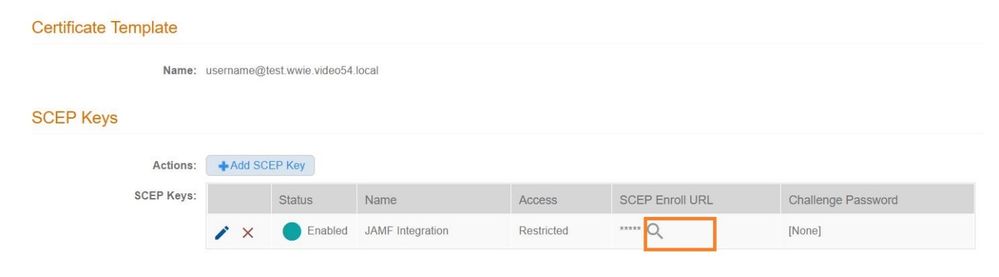
Back in the SCEP Keys tab of the certificate template, click on the “Show” icon under SCEP Enroll URL column.
This will reveal the full SCEP Key URL. Copy the full SCEP Enroll URL to a text editor (Notepad) for later use.
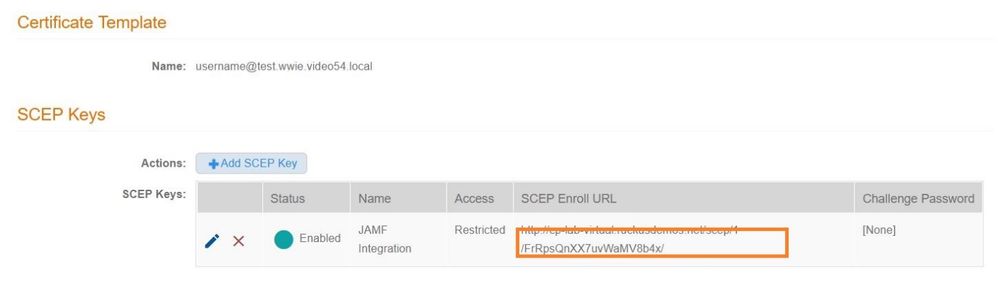
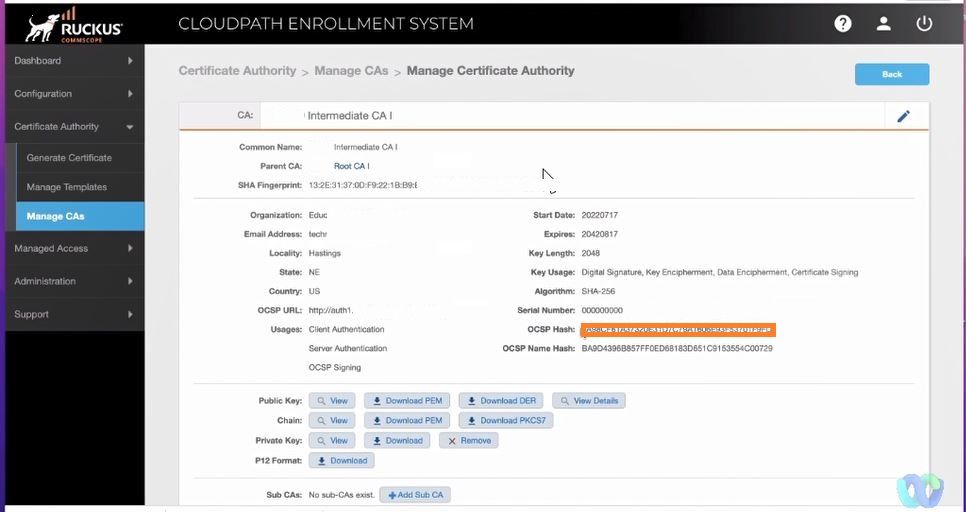
The Root CA will be used in a later step to create a Trusted Certificate profile in JAMF.
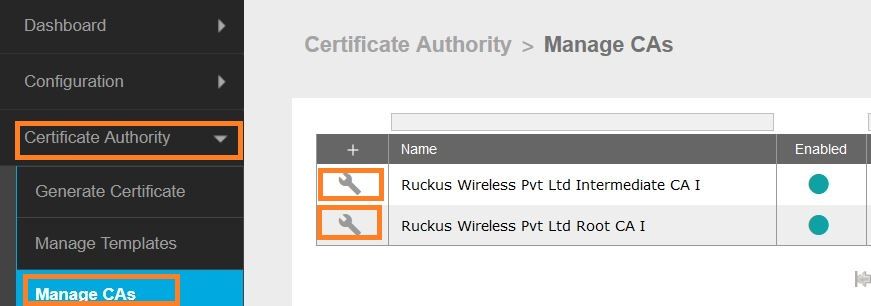
To export the CA certificate, go to Certificate Authority>>>Manage CAs. Expand the Root section.
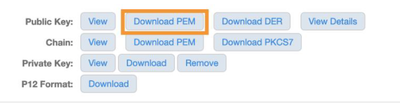
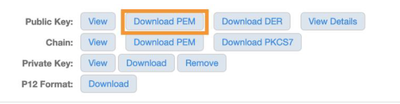
In the Public Key section, click on the “Download PEM” button. This will download a Base64 encoded DER file.
Perform the same steps for the Intermediate CA certificate
Get OCSP hash from Intermediate CA, it will be used in JAMF config later.
JAMF Configuration
CONFIGURATION PROFILES
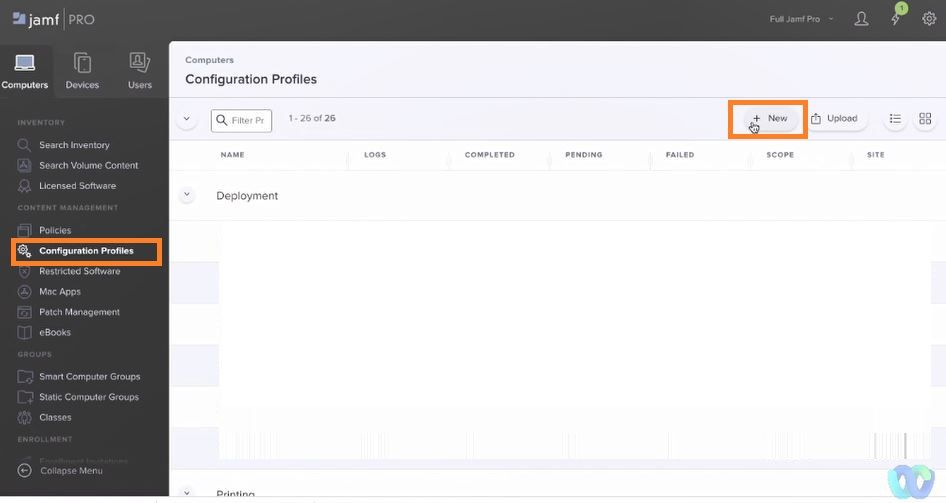
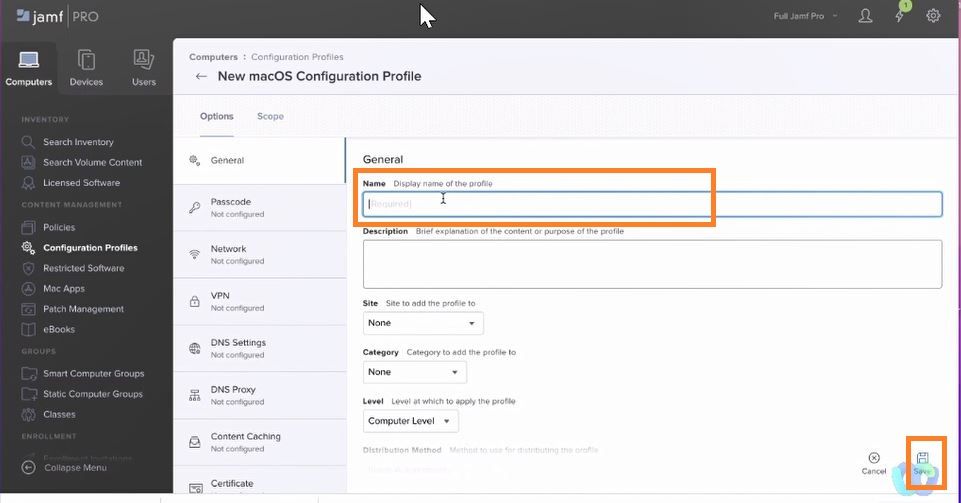
Login into JAMF select Configuration Profiles>>>>New
Name: Name the profile and Save.
SCEP SETTING
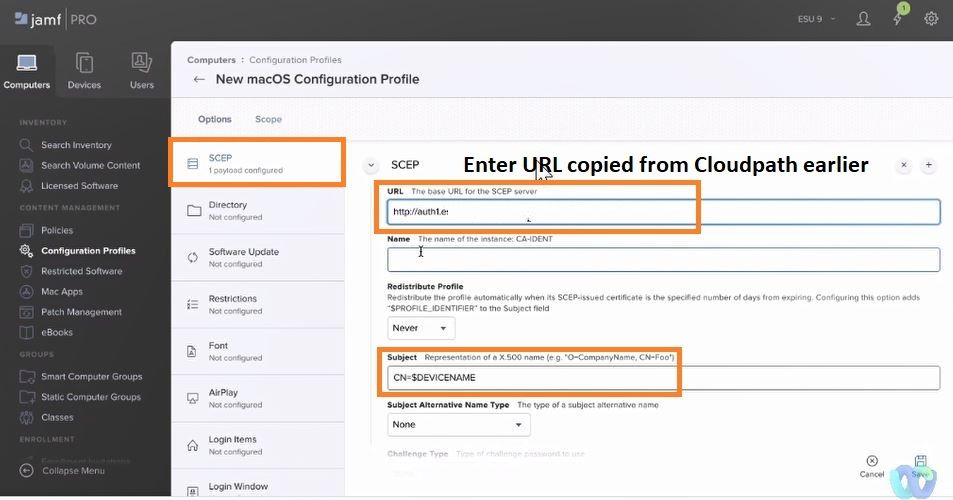
SCEP>>>Configure SCEP.
URL: SCEP url copied earlier from Cloudpath SCEP profile created earlier.
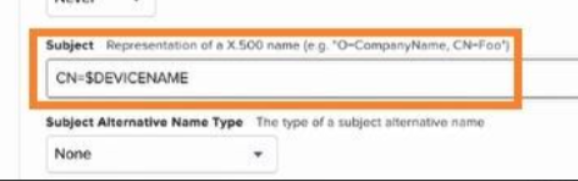
Subject: CN=$DEVICENAME for IOS
Subject: CN=$COMPUTERNAME for OSX
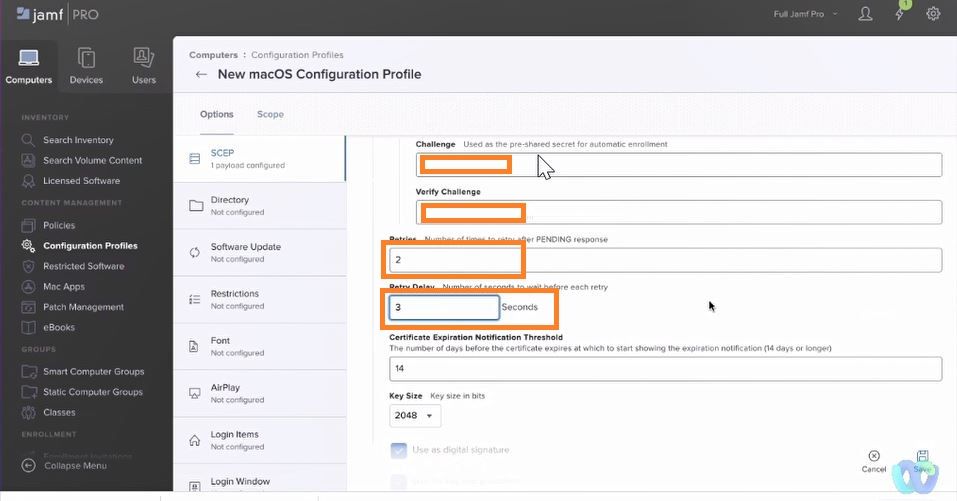
Challenge and Verify Challenge: From Cloudpath SCEP Profile
Retires: 2
Retry Delay: 3
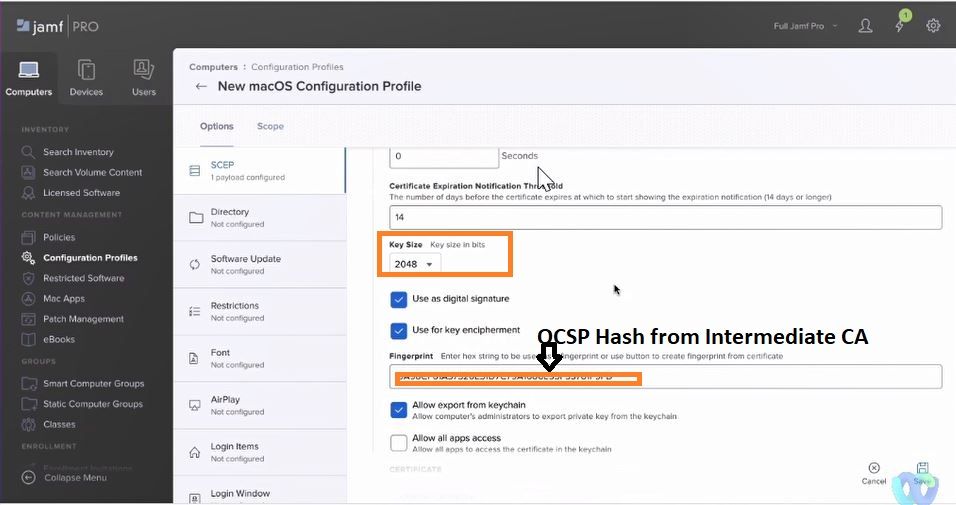
Key Size: 2048
Fingerprint: OCSP Hash from Cloudpath Intermediate CA
CERTIFICATE SETTING
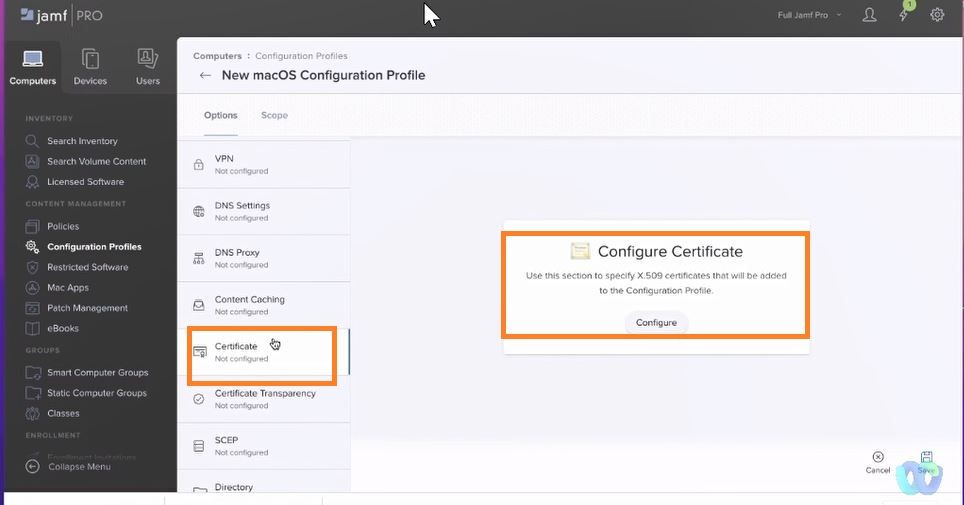
Select Certificate>>>Configure Certificate
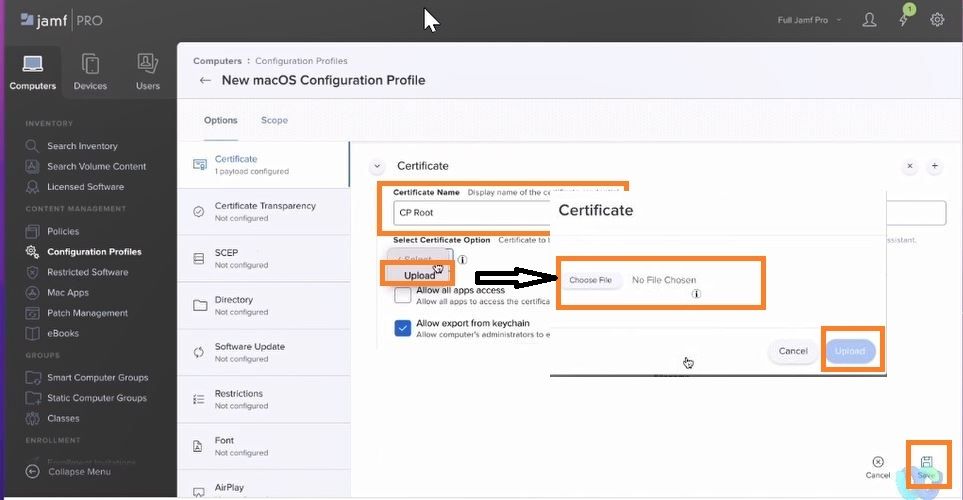
Import Root CA
Upload Root cert downloaded earlier from Cloudpath.
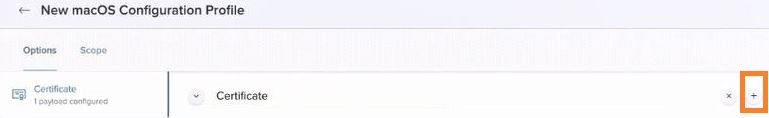
Click on + to add more cert.
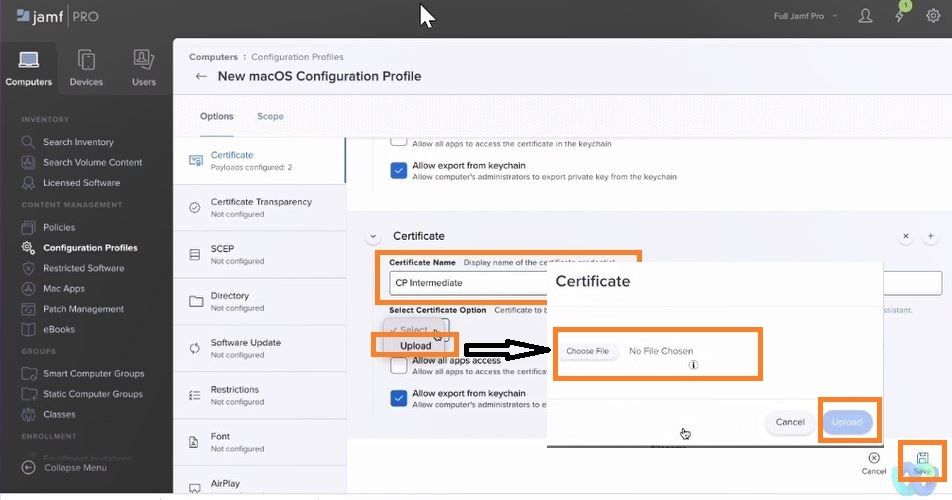
Import Intermediate CA
Upload Intermediate cert downloaded earlier from Cloudpath.
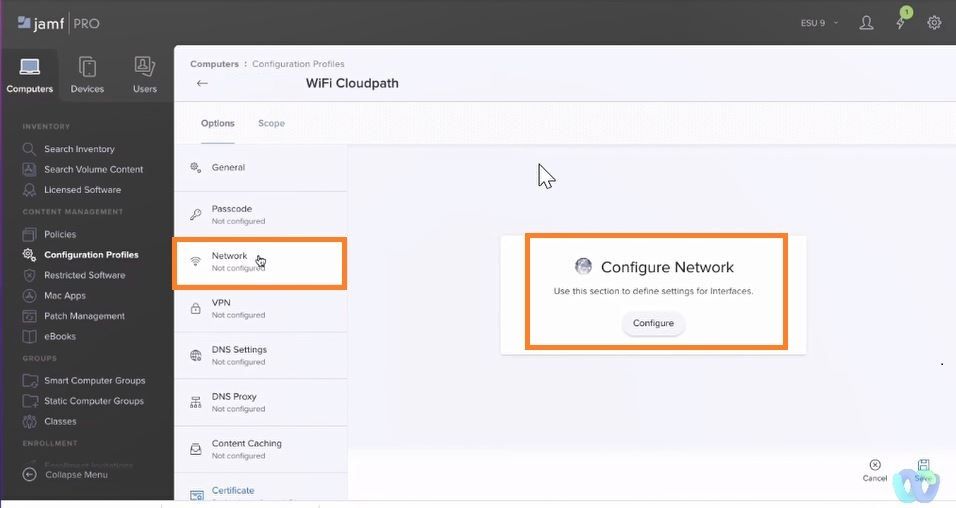
NETWORK SETTING
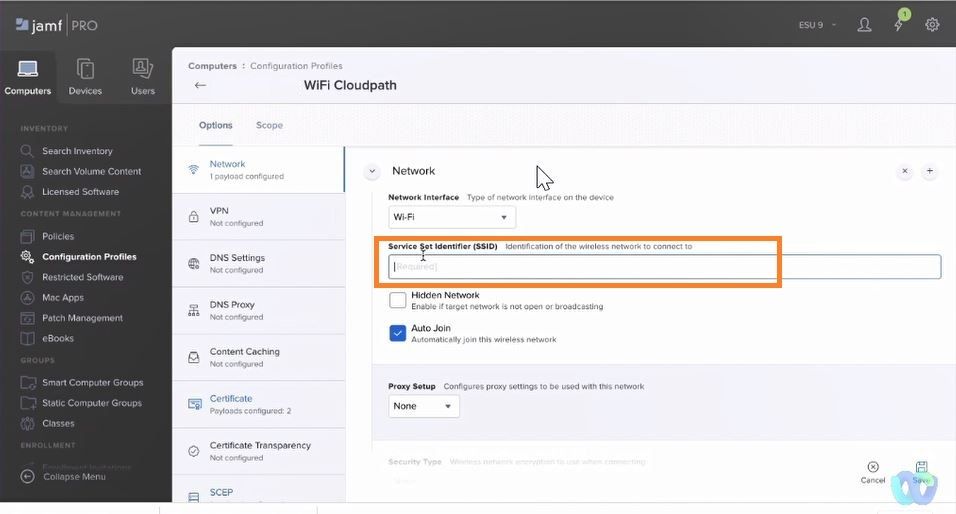
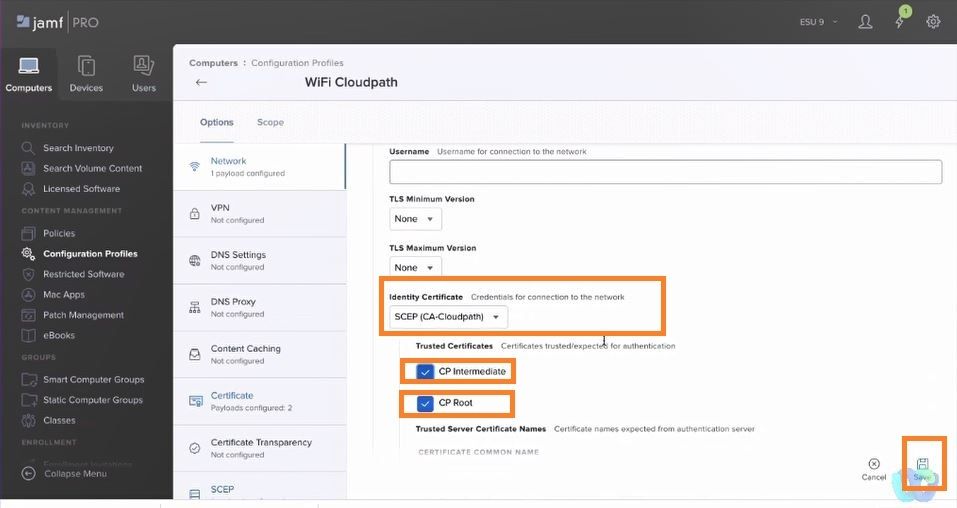
Network >>>Configure Network>>>Configure
Service Set Identifier(SSID😞 Name of the SSID
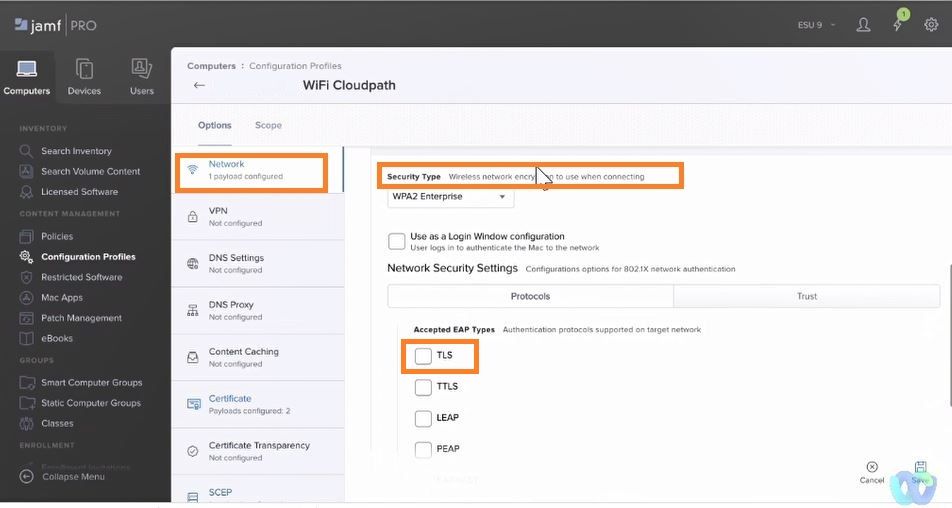
Security Type: WPA2 Enterprise
Accepted EAP Types: TLS
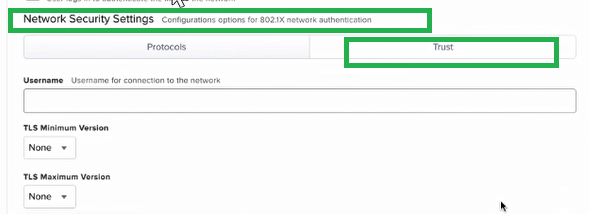
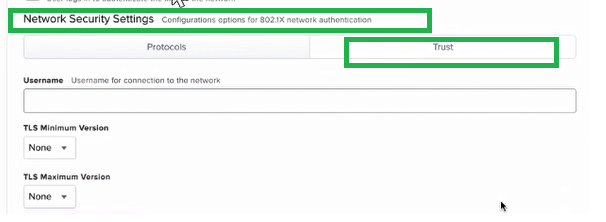
Select TRUST tab as shown in this screenshot.
Identity Certificate: Select SCEP profile created earlier.
Trusted Certificates: Select Root CA and Intermediate CA.
Staff Technical Support Engineer
CCNA RnS | CCNA Wireless | CWNA | RASZA | Meraki CMNO | RACPA
- Labels:
-
Cloudpath
-
RUCKUS Self-Help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 09:54 PM
Hi Vijay,
Currently we do not see the option for the trusted certificates box on our jamf pro upon doing the instructions on the last image. We are currently using Jamf Pro version 10.42.1-t1667311080. Will this affect the expected output?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 09:47 AM
Hi @froi_borja_ama,
I have added 1 more screenshot before the last image, hope that will help.
Staff Technical Support Engineer
CCNA RnS | CCNA Wireless | CWNA | RASZA | Meraki CMNO | RACPA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2023 09:12 PM
Hi Vijay
For the CN, can we use other format that gets the username instead of the text $DEVICENAME. Please see screenshot below for reference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2023 09:13 AM
Hi @froi_borja_ama,
I have not tested with username, but for cert assignment with username, I assume changing this setting in JAMF to CN=$USERNAME should work.
Let me know if it works.
Staff Technical Support Engineer
CCNA RnS | CCNA Wireless | CWNA | RASZA | Meraki CMNO | RACPA
-
AAA
2 -
Access points
48 -
Analytics
3 -
AP Certificate error
1 -
AP Controller Connectivity
5 -
AP Management
8 -
AP migration
1 -
AP reporting
1 -
API
2 -
Authentication Server
2 -
Client Management
1 -
Cloud
20 -
Cloud ICX
1 -
Cloudpath
23 -
Cluster synchronization
1 -
Deployment
2 -
Firmware Recommendation
1 -
Firmware Upgrade
5 -
Guest Access
2 -
ICX
73 -
ICX Switch Management
7 -
Installation
5 -
IoT
1 -
Licensing
1 -
Mobile Apps
2 -
Monitoring
1 -
Poe
2 -
RADIUS
2 -
Ruckus Cloud
1 -
RUCKUS Self-Help
209 -
Security
6 -
SmartZone or vSZ
64 -
Stacking
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
UMM
3 -
Unleashed
15 -
User Management
1 -
Venue Management
1 -
Wired Throughput
2 -
Wireless Throughput
1 -
WLAN Management
5 -
ZoneDirector
15
- « Previous
- Next »