- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- RUCKUS Self-Help
- SZ vSZ Admin Logon with Radius and Default Role Ma...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SZ vSZ Admin Logon with Radius and Default Role Mapping Disabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2023 10:43 PM - edited 08-24-2023 11:45 PM
Configuration for SZ administrator log in using Radius Server (without default role mapping )
STEP-1
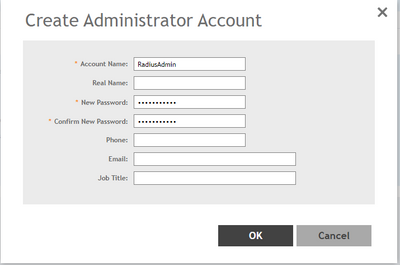
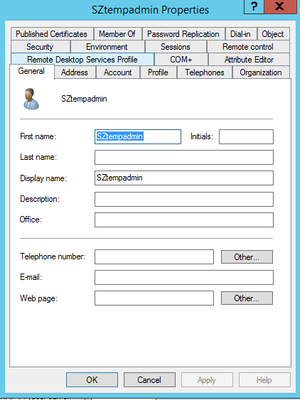
Create the Administrator account in SZ under Administration > Admin & Roles > Administrator > Create
The username will be the Vendor Attribute value (RadiusAdmin) configured in AAA under NPS Policy and the Password is the Shared secret used when adding the radius client
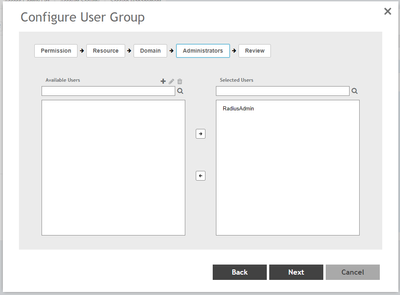
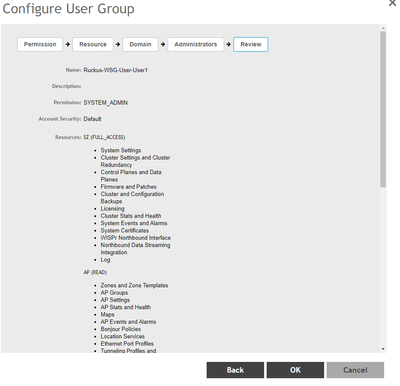
STEP-2
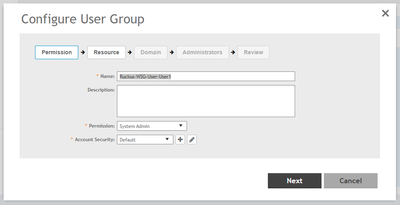
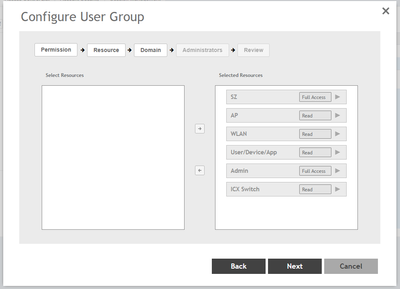
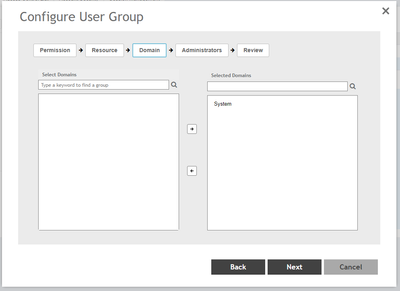
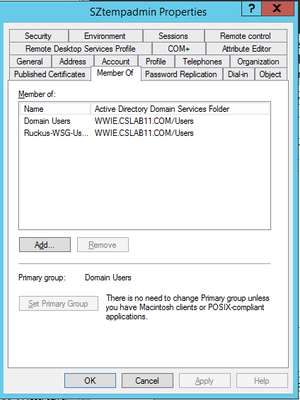
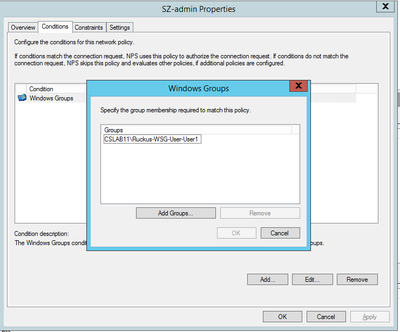
Create a new group in the following format: Ruckus-WSG-User-User1 under Administration > Admin & Roles > Groups > Create > Ruckus-WSG-User-User1
NOTE: Permissions can be set only at the group level and not user basis.
>Now map the RadiusAdmin administrator to the group
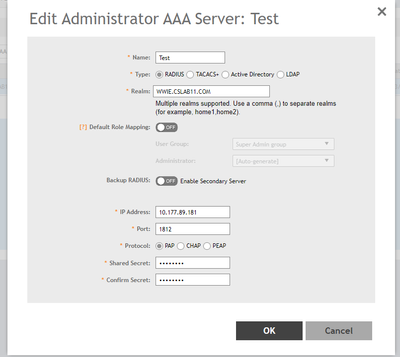
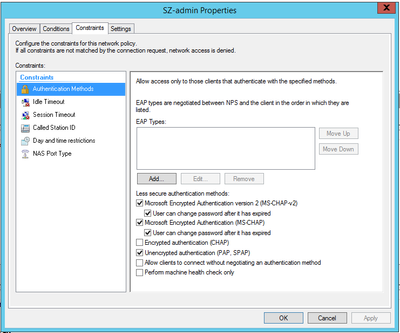
STEP-3: AAA Configuration for RADIUS Type with Default Role Mapping disabled:
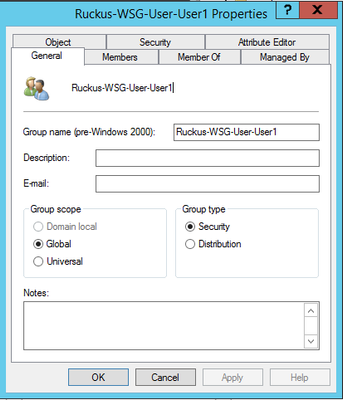
STEP-4: Configuration in AD
Create a User Group in the AD with the Group name: Ruckus-WSG-User-User1
NOTE: The Group name created in the AD must be as same as the Group Name created in vSZ/SZ.
STEP-5: Create a new user in the AD and add it to the above user Group
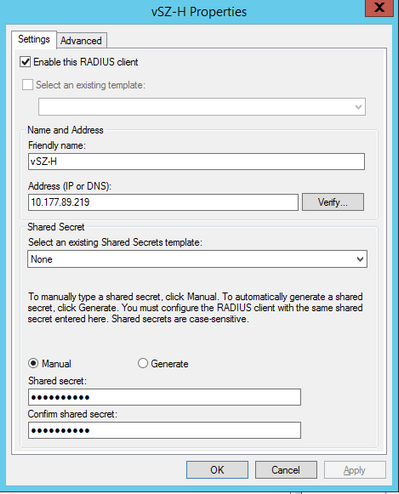
STEP-6: Configuration in NPS
Add vSZ/SZ as the Radius Client in AAA
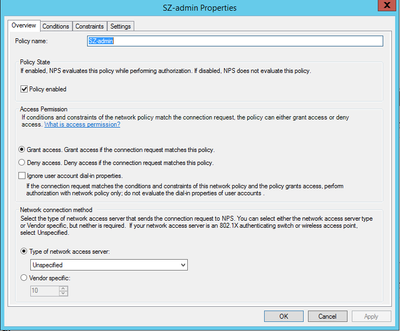
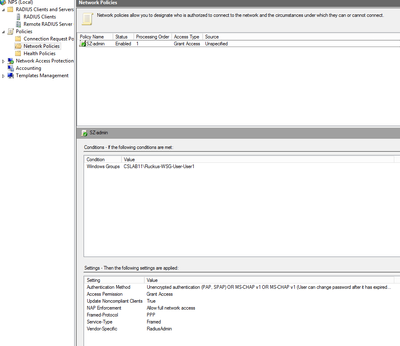
STEP-7: Creating Network Policy
Map the User Group,
>Select the Authentication method,
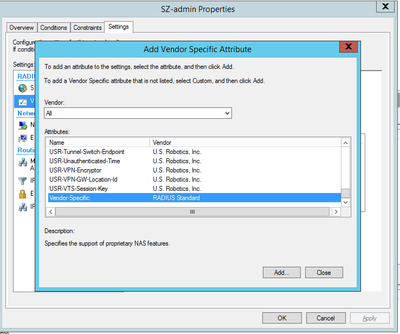
>In Settings, add the below
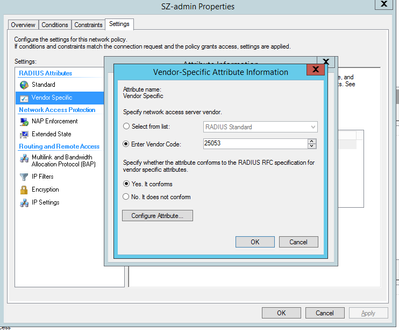
In Vendor-Specific Attribute, add Vendor Code as 25053 & AttributeValue as RadiusAdmin
>Review your NPS policy
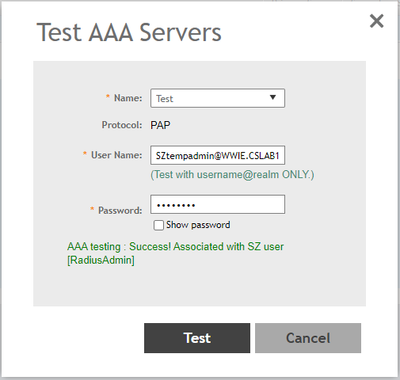
STEP-8: Perform AAA Test from the Controller
STEP-9: Test SZ login and should be allowed access to the Controller
- Labels:
-
RUCKUS Self-Help
-
SmartZone or vSZ
-
AAA
2 -
Access points
48 -
Analytics
3 -
AP Certificate error
1 -
AP Controller Connectivity
5 -
AP Management
8 -
AP migration
1 -
AP reporting
1 -
API
2 -
Authentication Server
2 -
Client Management
1 -
Cloud
20 -
Cloud ICX
1 -
Cloudpath
23 -
Cluster synchronization
1 -
Deployment
2 -
Firmware Recommendation
1 -
Firmware Upgrade
5 -
Guest Access
2 -
ICX
73 -
ICX Switch Management
7 -
Installation
5 -
IoT
1 -
Licensing
1 -
Mobile Apps
2 -
Monitoring
1 -
Poe
2 -
RADIUS
2 -
Ruckus Cloud
1 -
RUCKUS Self-Help
209 -
Security
6 -
SmartZone or vSZ
64 -
Stacking
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
UMM
3 -
Unleashed
15 -
User Management
1 -
Venue Management
1 -
Wired Throughput
2 -
Wireless Throughput
1 -
WLAN Management
5 -
ZoneDirector
15
- « Previous
- Next »