- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- RUCKUS Self-Help
- How to upload certificate on SmartZone Controllers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to upload certificate on SmartZone Controllers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2022
08:39 PM
- last edited on
09-21-2022
04:28 AM
by
![]() Anusha_Vemula
Anusha_Vemula
We have often come across a situation where we had to upload the wildcard certificate on the SmartZone controller. The reason, we do not want to get:
- Certificate error while accessing the management GUI of controller
- Certificate error while accessing the Captive Portal/Hotspot page on a WLAN
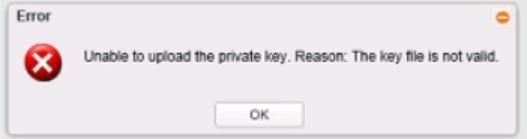
However, we run into issues while uploading the certificate on the controller like:
Hence, I will be guiding you with the step-by-step procedure of correctly uploading a certificate on the controller. In this guide, I will be talking about the steps of how to upload an SSL certificate and Wildcard certificate.
Following are some key points regarding the certificate:
- Usually, an SSL certificate is generated using CSR (Certificate Signing Request) from the controller. Sometimes, it will be generated using CSR from an external server.
- The wildcard certificate is always generated using CSR (Certificate Signing Request) from an external server. Below is the link which lists out the server from which you could generate CSR.
https://comodosslstore.com/resources/how-to-generate-a-csr-for-a-wildcard-ssl-certificate/
- The private key is a separate file that's used in the encryption/decryption of data sent between your server and the connecting clients. Hence, would need a private key file along with the certificate bundle if the CSR is generated from the external server.
- If the certificate is generated using CSR from the controller, then we do not need a separate private key file as it will be internally present on the controller’s certificate directory.
Once the certificate is signed by a valid Certificate Authority like GoDaddy, Comodo, Verisign, Digicert, etc. you will receive a certificate bundle in .pfx format, for example:
And if it is an SSL certificate it would look like below:
STEPS TO UPLOAD THE WILDCARD FILE:
The easier way to extract the server certificate and private key from .pfx format bundle is to use the Open SSL tool. Below is the link to download the OpenSSL tool:
https://www.openssl.org/source/
Place the pfx file into the OpenSSL's bin folder, and run the cmd using admin rights. example: cd CC:\OpenSSL-Win32\bin
Now run the below commands:
openssl pkcs12 -in WildCardCert.pfx -clcerts -nokeys -out Certificate.cer
openssl pkcs12 -in WildCardCert.pfx -nocerts -nodes -out private.key
NOTE:
1. Here is the certificate extension we are keeping as .cer and private key extension as .key format.
2. In the above, "WildCardCert.pfx" is the pfx cert you have with you. "Certificate.cer" is the file name for the cert exerted from pfx to .cer. And "private.key" is the private key.
3. It will ask for a password after each command to decrypt the certificate and private key. This password you would have created while generating the certificate. If no password was created and even if it prompts for a password, then just hit enter.
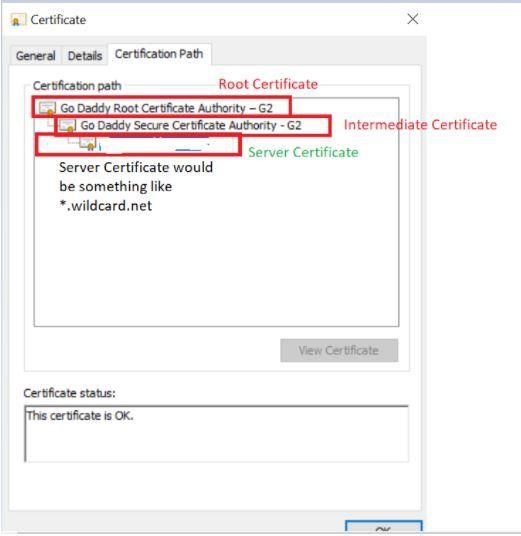
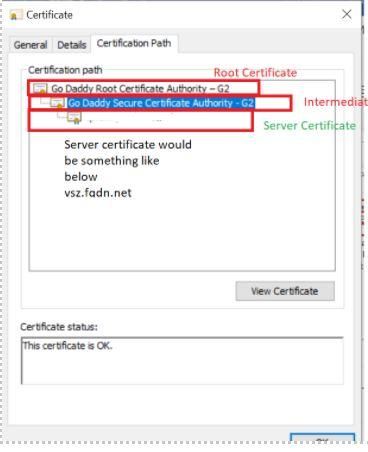
Once you have the cert in .cer format, open the WildCardCert.cer file and it will look like below:
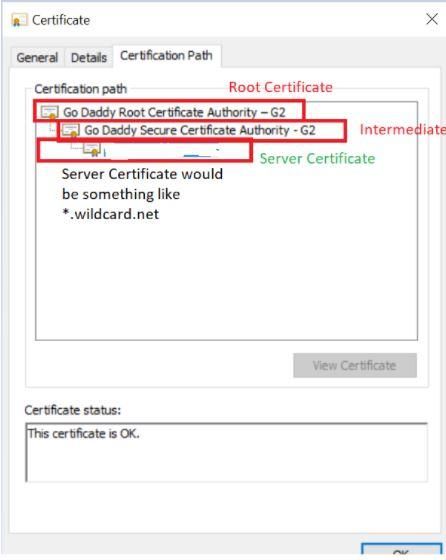
You must extract the server, root, and intermediate certificate as shown above and import them all to vSZ in the correct sequence. For this task, you can use a windows machine.
To extract the Server Certificate, follow the below steps:
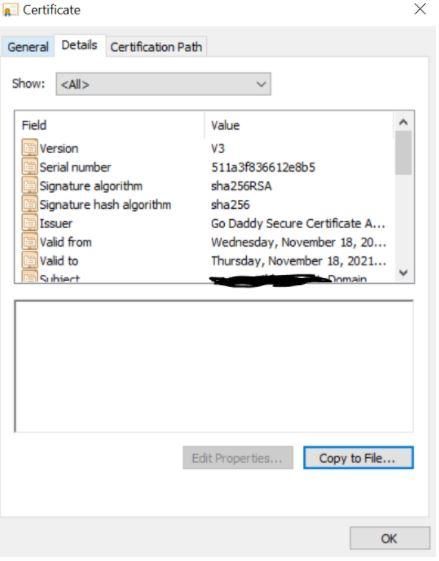
Open the Server Certificate file WildCardCert.cer. Navigate to Details and click on “Copy to File”
Click on Next.
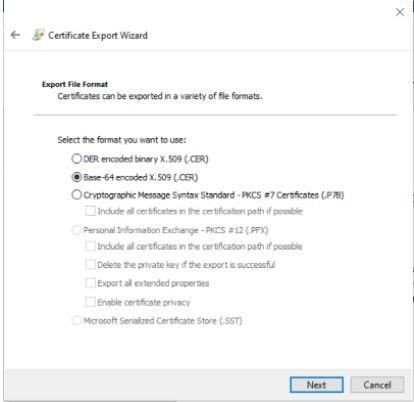
Select Base-64 encoding (.CER) and click on Next.
Browse, where you want to save the file and click on Next.
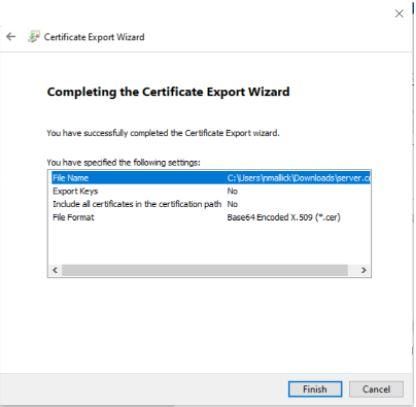
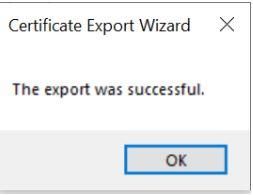
Click on “Finish” and it would show “The export was successful”
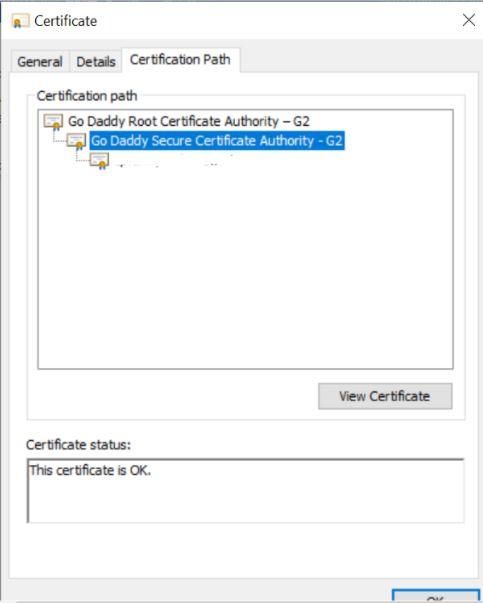
Then, follow the below steps to export the intermediate cert:
Click on Intermediate Certificate and then click on View Certificate
Click on Copy to File and follow the same steps as you followed for the Server certificate.
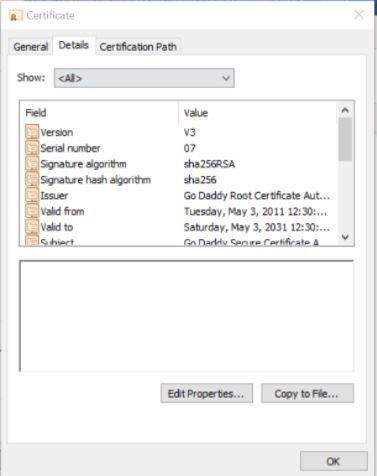
Follow the same steps to extract the Root Certificate. Make sure all the certificates that we are extracting should be exported with the Base encoding of 64.
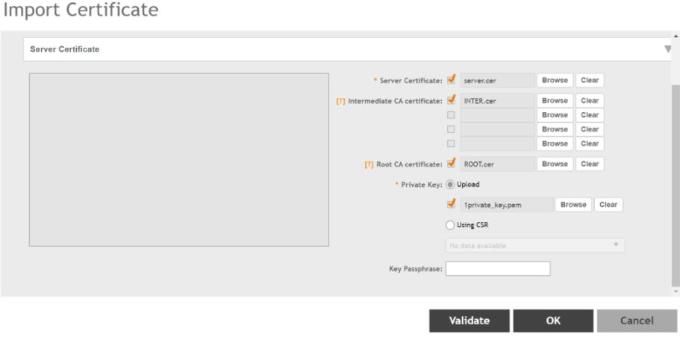
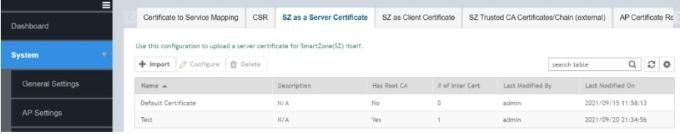
After you have all the certs (server, intermediate, and root). Then, navigate to the Controller’s System > Certificate > SZ as a server certificate > Import the respective files.
Upload the private.key and make sure NOT to use the key encryption password, as during the initial Open SSL commands you used the password to decrypt the certificate and key.
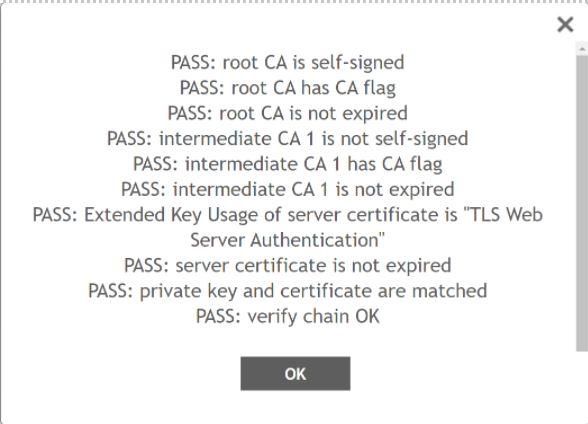
Then, click on Validate, it would show like below if the private key and certificates are correct and matching.
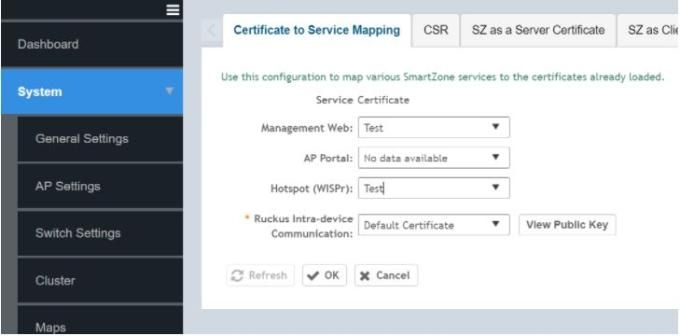
Map the “Test” certificate to the respective service:
NOTE: Once you click on OK, the controller services would be impacted for 30 minutes. Hence, it is always good to perform this activity during maintenance hours. Also, collect cluster backup prior to applying the certificate in the service. In case anything goes haywire, then we can revert to the previous configuration by restoring the backup.
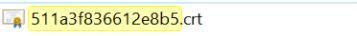
STEPS TO UPLOAD THE SSL CERTIFICATE:
Once you open the file 511a3f836612e8b5.crt
It would show up like below:
Then follow the same steps as shown above to extract the server, root, and intermediate certificate. This time while uploading the SSL certificate on the controller you will need to add the Key passphrase if you have one. If not, you can keep it blank. Once the certificate is validated, apply it to the respective service.
- Labels:
-
RUCKUS Self-Help
-
AAA
2 -
Access points
48 -
Analytics
3 -
AP Certificate error
1 -
AP Controller Connectivity
5 -
AP Management
8 -
AP migration
1 -
AP reporting
1 -
API
2 -
Authentication Server
2 -
Client Management
1 -
Cloud
20 -
Cloud ICX
1 -
Cloudpath
23 -
Cluster synchronization
1 -
Deployment
2 -
Firmware Recommendation
1 -
Firmware Upgrade
5 -
Guest Access
2 -
ICX
73 -
ICX Switch Management
7 -
Installation
5 -
IoT
1 -
Licensing
1 -
Mobile Apps
2 -
Monitoring
1 -
Poe
2 -
RADIUS
2 -
Ruckus Cloud
1 -
RUCKUS Self-Help
209 -
Security
6 -
SmartZone or vSZ
64 -
Stacking
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
UMM
3 -
Unleashed
15 -
User Management
1 -
Venue Management
1 -
Wired Throughput
2 -
Wireless Throughput
1 -
WLAN Management
5 -
ZoneDirector
15
- « Previous
- Next »