- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- RUCKUS Self-Help
- How to Install a Certificate on SZ/vSZ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to Install a Certificate on SZ/vSZ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022
11:20 AM
- last edited on
09-21-2022
03:44 AM
by
![]() Anusha_Vemula
Anusha_Vemula
How to Install a Certificate on SZ/vSZ?
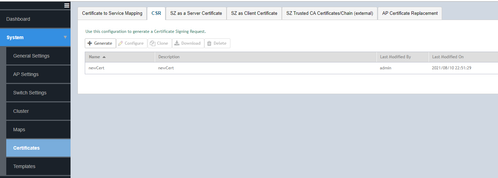
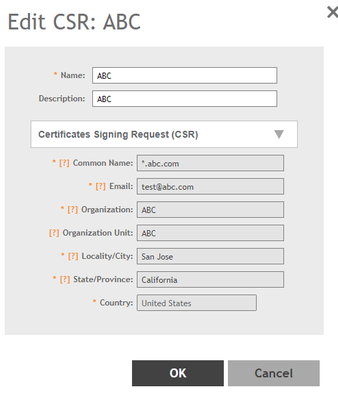
- Generate the CSR from any node, or the same can be generated from a third part device:
System >> Certificates >> CSR >> Generate
- Fill in the details and submit the same to a CA authority
Now, you will be able to see the same CSR in all nodes in the cluster
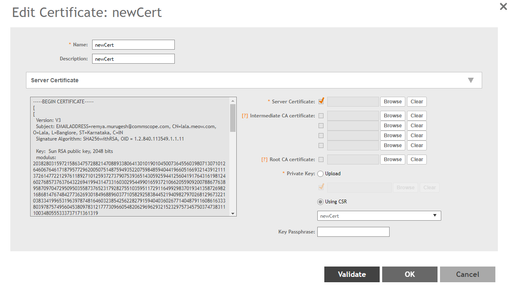
- Once the certificate is received, import the certificate to SZ from System >> Certificates >> SZ as a Server Cert
Browse and select the Server, Intermediate and Root certificates accordingly for the intended certificate
Alternatively, you may chain all the related certificates to a single file in .pem format and map the same against Server Certificate
Chaining order: Server, Intermediate and Root
- Apply Private Key
Select the CSR associated with the certificate for private key
For a third party generated CSR, upload the private key along with the associated certificates
Note: The certificate formats supported are only PEM and CRT
- Click on the Validate certificate and Click OK once the validate summary is displayed
Once the certificate is successfully uploaded, you can again crosscheck the certificate availability on each node in cluster
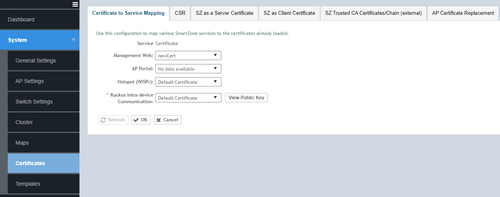
- Then the certificate can be mapped against the preferred services from System >> Certificates >> Certificate to Service Mapping
- Management Web : Used by Web UI and Public API traffic
- AP Portal: Used by Web Auth WLAN and Guest Access WLAN control traffic
- Hostpot Wispr: Used by WISPr WLAN control (Northbound Interface, Captive Portal, and Internal Subscriber Portal) traffic
- Ruckus Intra device: Used by AP control traffic
This will again be synced among the cluster nodes.
Please note that the certificate import would initiate a service restart on the web and subscriber management applications. You can verify the status of the services from SZ CLI:
>en
<enable password>
#show service
Remya Murugesh
Staff Technical Support Engineer
- Labels:
-
RUCKUS Self-Help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2022 10:33 AM
Very useful clarification, documentation isn't describing this important task in detail. I think it is important to mention that certificate should be a wildcard certificate, as the same certificate is used on all vSZ or SZ nodes in a cluster, so it must be valid for multiple FQDNs.
Therefore the cheapest certificate will not do -- except if you can use FQDN for one node as domain.com and for another -- www.domain.com , this will work as by default most certificates include both names. You can import simple one-domain certificate, but than you will be able connect securely to only one node, to the second node you'll need to connect only using IP and will be getting warning in a browser - modern browser don't allow connection by name to site with wrong certificate...
Services restart after certificate change can easy take 30 minutes, so don't be warried that you broke the system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2024 12:21 AM
Do we have to make any DNS entries after uploading the public certificate which is going to be used for guest portal under AP Portal menu mapping?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2024 04:19 AM
Do we have to make any DNS entries after uploading the public certificate which is going to be used for guest portal under AP Portal menu mapping?
-
AAA
2 -
Access points
48 -
Analytics
3 -
AP Certificate error
1 -
AP Controller Connectivity
5 -
AP Management
8 -
AP migration
1 -
AP reporting
1 -
API
2 -
Authentication Server
2 -
Client Management
1 -
Cloud
20 -
Cloud ICX
1 -
Cloudpath
23 -
Cluster synchronization
1 -
Deployment
2 -
Firmware Recommendation
1 -
Firmware Upgrade
5 -
Guest Access
2 -
ICX
73 -
ICX Switch Management
7 -
Installation
5 -
IoT
1 -
Licensing
1 -
Mobile Apps
2 -
Monitoring
1 -
Poe
2 -
RADIUS
2 -
Ruckus Cloud
1 -
RUCKUS Self-Help
209 -
Security
6 -
SmartZone or vSZ
64 -
Stacking
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
UMM
3 -
Unleashed
15 -
User Management
1 -
Venue Management
1 -
Wired Throughput
2 -
Wireless Throughput
1 -
WLAN Management
5 -
ZoneDirector
15
- « Previous
- Next »