This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- SZ / vSZ
- vSZ-D Tunnelling WLAN with VLAN Tag What i am miss...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
vSZ-D Tunnelling WLAN with VLAN Tag What i am missing
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 02:12 AM
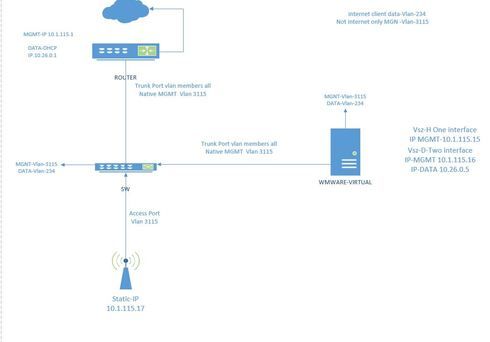
The problem is when i create WLAN and tagged it with DATA VLAN ID 234 , (i used Tunnel WLAN traffic to the controller) my client can't get IP address from DATA VLAN, try it with static IP address assignment, my device still can't ping my DATA VLAN Gateway 10.26.0.1
I look around the configuration and still not working. What i am missing
Vsz-H version 3.5.1.0.862
Vsz-D version 3.5.1.0.862
AP-R700 Router Cisco DHCP-SERVER and Gateway
SW-Juniper
Virtual :
Vsz-D Data interface IP 10.26.0.5
MGMT interface IP 10.1.115.16 Vsz-H
MGMT interface IP 10.1.115.15
AP IP 10.1.115.17
all port Trunk.
My Topology
I look around the configuration and still not working. What i am missing
Vsz-H version 3.5.1.0.862
Vsz-D version 3.5.1.0.862
AP-R700 Router Cisco DHCP-SERVER and Gateway
SW-Juniper
Virtual :
Vsz-D Data interface IP 10.26.0.5
MGMT interface IP 10.1.115.16 Vsz-H
MGMT interface IP 10.1.115.15
AP IP 10.1.115.17
all port Trunk.
My Topology

11 REPLIES 11
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2018 10:58 PM
Hi Rafael,
on the VMware host you can use different port groups depending on your license.
the normal vSwitch can handle:
AND on the PG all security option (promiscuous mode, etc...) must be set to "accept".
Now the vSZ-D part:
On the data interface only the VLAN/IP for the APs to connect to has to be configured. Depending on your configuration you need to specify a VLAN for the interface.
All other VLANs will be configured in the SSID configuration.
cheers,
Harald
on the VMware host you can use different port groups depending on your license.
the normal vSwitch can handle:
- untagged (whatever comes untagged on the physical NIC/s comes untagged to the VM)
- tagged (the network with the selected VLAN Tag comes tagged on the physical NIC/s and will be an access port in the VLAN to the VM; tagged outside of the VM will be turned to access facing the VM)
- 4095 (replication of all VLANs from the physical NIC/s to the VM, untagged will stay untagged, tagged will stay tagged; no selection possible)
- selective VLANs (you can select multiple VLANs to be delivered to the VM, all will be tagged)
AND on the PG all security option (promiscuous mode, etc...) must be set to "accept".
Now the vSZ-D part:
On the data interface only the VLAN/IP for the APs to connect to has to be configured. Depending on your configuration you need to specify a VLAN for the interface.
All other VLANs will be configured in the SSID configuration.
cheers,
Harald
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 01:00 PM
Thank you for you answer Harald !!
I was able to make it work.
Still, I am having trouble with my tunnel ssids that use the captive portal from the controller.
My guess is that my management port is not tagged correctly, because I can't see how from the data interface my unauthenticated wireless traffic will be intercept without my controller being my gateway nor inlane.
Did you have any advice where I should look ? Is there a different configuration in smartzone pertain tunnel traffic that I should do to make the captive portal work ???
I was able to make it work.
Still, I am having trouble with my tunnel ssids that use the captive portal from the controller.
My guess is that my management port is not tagged correctly, because I can't see how from the data interface my unauthenticated wireless traffic will be intercept without my controller being my gateway nor inlane.
Did you have any advice where I should look ? Is there a different configuration in smartzone pertain tunnel traffic that I should do to make the captive portal work ???
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2019 02:02 AM
Hi Rafael,
can you pls send the vlan configuration of the physical switch ports that are connected to the uploads of your vswitch and the configuration of the port groups connected to the management and data interface.
cheers,
Harald
can you pls send the vlan configuration of the physical switch ports that are connected to the uploads of your vswitch and the configuration of the port groups connected to the management and data interface.
cheers,
Harald
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 09:45 AM
Hi harald, sorry, I can't send. This configuration was of a client that I helped. The switches was not my responsibility. I only instructed and let the client investigated and fixed by himself. The last part of the problem was physical switch missing one vlan connect to the vmware server and fault/broken ethernet cable.
You could make the ports vlan trunk all, it should work only need to make sure about the native vlan.
You could make the ports vlan trunk all, it should work only need to make sure about the native vlan.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 11:50 AM
Are you using a vSwitch or a distributed vSwitch?
Labels
-
9210
1 -
AD
1 -
AP Controller Connectivity
1 -
AP Management
2 -
API Help
1 -
Client Management
3 -
er
1 -
Google
1 -
Guest Access
2 -
IP Multicast
1 -
Proposed Solution
3 -
RADIUS
2 -
RUCKUS Self-Help
8 -
SmartZone
4 -
SmartZone or vSZ
6 -
Social Media
1 -
Solution Proposed
3 -
string
1 -
Traffic Management-
1 -
User Management
2 -
vSZ
2 -
Wifi
1 -
WLAN Management
2
- « Previous
- Next »
