This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- SZ / vSZ
- Re: Zone Director and NPS/Radius for Admin authent...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Zone Director and NPS/Radius for Admin authentication
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2019 08:26 AM
I am trying to find documentation on how to properly configure Windows(2016) Server with AD/NPS/Radius to authenticate administrators on our ZD (and eventually SZ) controllers. We are NOT looking to authenticate WiFi users.
Are there any special attributes we need to add? Assuming Service-Type:Login and removing any Framed statements(PPP) Anything else?
Are there any special attributes we need to add? Assuming Service-Type:Login and removing any Framed statements(PPP) Anything else?
15 REPLIES 15
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 06:57 AM
ok i got that if you want to delete it
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 07:48 AM
Dave Bauman, you do ideally need an internal AD CA that issues certificates to your NPS servers and probably your workstations and DCs too. and the CA is in Trusted Root Certificate Authority on the connecting workstations ( which an AD CA Cert is automatically added to by AD to all domain joined workstations.)
to issue to workstations...
GPO Computer Config > Policies >Windows Settings> Security Settings > Public Key Policies/Automatic Certificate Request Settings > Automatic Certificate Request > Computer...
to issue to workstations...
GPO Computer Config > Policies >Windows Settings> Security Settings > Public Key Policies/Automatic Certificate Request Settings > Automatic Certificate Request > Computer...
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 07:52 AM
We don't really use AD for workstations or at all at this time. We have a lot of gear in the field and are moving away from a single admin login/password as it has become unmanageable. The only purpose for AD/Radius at this time is to authenticate our admins in the field.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 07:58 AM
fair enough i do use 802.1X for BYOD but the devices complain about the cert and windows PCs wont even connect unless you put the Root ADCA in the trusted root or use a publicly trusted cert (but not a wildcard) but then it complains about the name miss match... but it does work.... just a bit clunky on first connect.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 08:39 AM
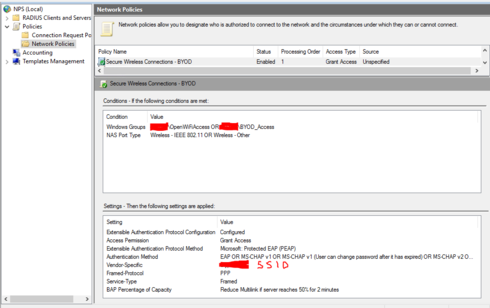
thats my byod radius setup... not perfect but does work i don't think the vendor specific bit isnt needed i think that was me trying to use one NPS server for both computer auth and byod user auth in the end i split them

Labels
-
9210
1 -
AD
1 -
AP Controller Connectivity
2 -
AP Management
5 -
AP reporting
1 -
API Help
1 -
Client Management
4 -
er
1 -
Google
1 -
Guest Access
3 -
ICX Switch Management
1 -
IP Multicast
1 -
Proposed Solution
3 -
RADIUS
2 -
RUCKUS Self-Help
8 -
SmartZone
4 -
SmartZone or vSZ
6 -
Social Media
1 -
Solution Proposed
3 -
string
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
User Management
2 -
vSZ
2 -
Wifi
1 -
WLAN Management
2
- « Previous
- Next »

