This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- SZ / vSZ
- Re: VSZ - Active Directory and Default Group Attri...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VSZ - Active Directory and Default Group Attribute Value
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2016 03:59 AM
Hello,
I am just wondering if anyone has got their VSZ setup with a WLAN that users log into the web authentication using accounts from Active Directory.
I had this set up p[perfectly with the ZoneDirector but can't seem to get it to work with the VSZ.
The Admin Guide i have says I can set the default Group Attribute Value when configuring the Roles, but that option is not there. The option is there how ever when I configure a Proxy AAA, but when testing, the results return Primary server success but do not list the group (which I've read it should). When logging into the WLAN I can an Invalid username or password message.
Has anyone got this kind of setup working. I have a case open, just looking to see if people have the same issue.
Thanks.
I am just wondering if anyone has got their VSZ setup with a WLAN that users log into the web authentication using accounts from Active Directory.
I had this set up p[perfectly with the ZoneDirector but can't seem to get it to work with the VSZ.
The Admin Guide i have says I can set the default Group Attribute Value when configuring the Roles, but that option is not there. The option is there how ever when I configure a Proxy AAA, but when testing, the results return Primary server success but do not list the group (which I've read it should). When logging into the WLAN I can an Invalid username or password message.
Has anyone got this kind of setup working. I have a case open, just looking to see if people have the same issue.
Thanks.
26 REPLIES 26
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2018 04:00 PM
For some reasson the version 3.5.1.0.862, VSZ High is not letting us use proxy mode, does somebody knows if this mode works in this version ? im thinking that maybe I need an upgrade to fix some bug, have of you went through this problem? when I changed the mode to none proxy I started receving erros and logs from the AP, but I wasnt able to receive logs from the cVSZ controller in proxy mode.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 03:05 AM
We have been in the fortunate situation where we have a ZD1200 on loan from our suppliers when we bough the vSZ license. 2 Years on as we are still no where near to using the vSZ for what i want to do with it however it feels like we have some software that promissed to deliver but it simply doesn't, the vSZ is now running 5.1.
I was told years ago that the vSZ and the ZD software would alost be exactly the same however this isn't the case. It seems that the ZD software is more feature rich than the vSZ by a country mile.
It would seem that Ruckus have finally brough in the Active Directory Group lookup as shown here from my vSZ-H setup:
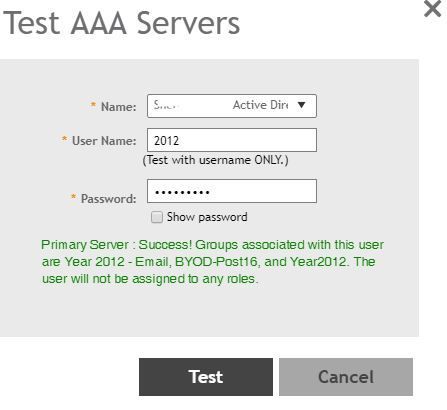
however they haven't yet implimented the ROLES side so this user who is a test user in our AD is in the correct AD Group, however they aren't limited to join a specific SSID.
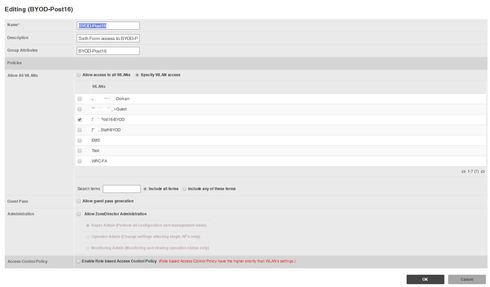
Here is what i am using now in the ZD1200 and would have hoped to have seen the same in the vSZ but this isn't the case:
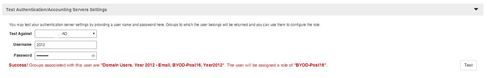
What the above 2 images from my ZD1200 are showing is, picture 1 is showing the ZD querying our AD to find what group memberships user 2012 is part of.
Picture 2 is showing the options under ROLES so that if the GROUP ATTRIBUTES field matches those that the user is part of in AD, the user is able to access that SSID.
This feature is missing from the vSZ and cannot be found!
I guess this is what others are waiting for and using RADIUS Authentication is not an option. We do Radius Accounting via our Smoothwall on the ZD1200.
Also what is missing on the vSZ, is the ability to have HOTSPOT (WSPr) set and to authenticate via Active Directory.
I was told years ago that the vSZ and the ZD software would alost be exactly the same however this isn't the case. It seems that the ZD software is more feature rich than the vSZ by a country mile.
It would seem that Ruckus have finally brough in the Active Directory Group lookup as shown here from my vSZ-H setup:

however they haven't yet implimented the ROLES side so this user who is a test user in our AD is in the correct AD Group, however they aren't limited to join a specific SSID.
Here is what i am using now in the ZD1200 and would have hoped to have seen the same in the vSZ but this isn't the case:


What the above 2 images from my ZD1200 are showing is, picture 1 is showing the ZD querying our AD to find what group memberships user 2012 is part of.
Picture 2 is showing the options under ROLES so that if the GROUP ATTRIBUTES field matches those that the user is part of in AD, the user is able to access that SSID.
This feature is missing from the vSZ and cannot be found!
I guess this is what others are waiting for and using RADIUS Authentication is not an option. We do Radius Accounting via our Smoothwall on the ZD1200.
Also what is missing on the vSZ, is the ability to have HOTSPOT (WSPr) set and to authenticate via Active Directory.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2019 05:03 PM
I'm doing vSZ And have run into this problem, moving from ZD3050 and realize.the feature are just there in vSZ, disappointing. Also web authentication doeant seem to work, having to do hotspot Wispr. Not impressed so far, so disappointed. I did some trouble shooting before my planned deployment next week, I discovered when doing AD auth, if a user is in one group it's fine, but if it multiple groups it's only the first queried group that works, and it's in alpha order.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2019 11:58 PM
I got round the problem in the end. BYOD WLAN setup as 802.1x EAP and the authentication server set as our RADIUS server (Smoothwall). In the smoothwall box is now where we can limit the access to users that are a member of a certain AD group. Any users that we then want to have BYOD access we can add to a named security group and they can authenticate with their AD username and password.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2019 09:22 AM
Dave, how did you go about doing this? We are trying to do something similar using Windows NPS and are striking out. I have a AAA (RADIUS) server setup (our NPS) and I configured a specific WLAN for a NAS-ID. I enabled Web Auth and tied the Web Auth portal to the WLAN. The page comes up but no user can authenticate, period. If I change the portal to HotSpot WISPr, authentication works just fine...I'm not sure what the issue is here.
Labels
-
9210
1 -
AD
1 -
AP Controller Connectivity
2 -
AP Management
5 -
AP reporting
1 -
API Help
1 -
Client Management
4 -
er
1 -
Google
1 -
Guest Access
3 -
ICX Switch Management
1 -
IP Multicast
1 -
Proposed Solution
3 -
RADIUS
2 -
RUCKUS Self-Help
8 -
SmartZone
4 -
SmartZone or vSZ
6 -
Social Media
1 -
Solution Proposed
3 -
string
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
User Management
2 -
vSZ
2 -
Wifi
1 -
WLAN Management
2
- « Previous
- Next »

