- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- Unleashed
- System L2ACL Issues - R510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2023 08:50 PM
Hi folks--
I'm having issues with my Unleashed R510 and L2ACL. Up until earlier today I had an L2ACL (we'll call it Deny) assigned to a specific SSID. At a particular point I unblocked a device that was going to be used again (that was not on the Deny L2ACL) via the Unleashed app, and then noticed every entry in the Deny L2ACL was now being blocked on each SSID.
I then logged into the web UI to check the config, and removed the ACL within the UI, yet the devices were still being shown as blocked in the client list. I've power-cycled the unit, upgraded and downgraded, seemingly everything but a factory reset.
To the subject, though: After getting a chance to log into the AP via the CLI, I've confirmed that all of the entries in the Deny L2ACL are now in the System L2ACL, and I have not been able to edit the System L2ACL via CLI or otherwise.
Does anyone know how to edit the System L2ACL? Or how to resolve this issue otherwise? (I would obviously prefer not to do a factory reset.)
Solved! Go to Solution.
- Labels:
-
l2acl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:54 PM
Hi @Mouse6213,
If you block a client directly from the web UI under clients, it will become the part of global L2ACL block list and blocked users cannot connect to any SSID. This is as per design.
Try below online doc which has CLI command to unblock a client, see if that helps.
Syamantak Omer
Sr.Staff TSE | CWNA | CCNA | RCWA | RASZA | RICXI
RUCKUS Networks, CommScope!
Follow me on LinkedIn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2023 04:13 PM
Hi folks--
Anyone have any ideas on this? I've asked some folks offline tied to Ruckus/Commscope, and they, too, have been stumped.
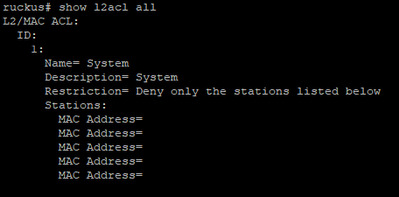
This is what I see via terminal (MAC addresses removed). I still have not found a way to remove items from the L2ACL, which really does strike me as an odd situation to have. Happens with most recent firmware and a step down.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2023 06:30 PM
Hi @Mouse6213
Can you try the below steps from the CLI:
To delete the ACL policy:
ruckus(config)# no l2acl <ACL name>
Example: ruckus(config)# no l2acl ACL
ruckus(config-l2acl)# end
To delete just the MAC entries and not the ACL policy:
ruckus# config
ruckus(config)# l2acl <Enter the L2 MAC ACL name>
ruckus(config-l2acl)# del-mac <MAC> -----> Deletes a MAC address from the L2 ACL.
ruckus(config-l2acl)# end
Let me know if this works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2023 02:47 PM
Hi @sanjay_kumar --
Unfortunately, since these were somehow added to the System L2ACL, I'm not able to update that policy even in privileged.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2023 01:14 AM
Hi @Mouse6213
If you go to Clients Tab >> You can see the list of clients, do you also see the clients here which you can see from the CLI System L2acl?
If yes, you can select it >> Click on More >> Click on Unblock.
This will remove the entry from the System L2acl. I just tried and it worked.
Please check and let me know.
If it is not working, please let me know the exact steps to reproduce the issue so that I can try.
-
200.12.10.5.234
1 -
AP Certificate error
1 -
AP Management
5 -
AP reporting
1 -
authentication fails
1 -
captive portal
1 -
Certificate
1 -
Client Management
1 -
DPSK
1 -
Guest Access
1 -
Guest Pass
1 -
Installation
1 -
IP Multicast
1 -
l2acl
1 -
LACP
1 -
laptop hp probook 430 g8
1 -
Mesh
1 -
Monitoring
1 -
Op
1 -
pfSense
1 -
R310
2 -
R550
1 -
R650
1 -
Security
1 -
Solution Proposed
3 -
SSID
1 -
temporarily blocked
1 -
Unleashed
6 -
User Management
1 -
Web UI
1 -
Wired Throughput
1 -
Wireless Throughput
2 -
WLAN
1 -
WLAN Management
1 -
WPA3
1 -
WPA3-Enterprise
1
- « Previous
- Next »