This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- SZ / vSZ
- Re: VSZ - AWS - Multiple Interfaces
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VSZ - AWS - Multiple Interfaces
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 10:36 AM
Hi,
has anyone successfully created a vSZ instance in AWS using multiple interfaces for the different control planes ? (Management/AP Control/Cluster) like is possible on a traditional hypervisor setup?
The Ruckus vSZ AWS documentation does not mention this and from my own testing so far, vSZ does not detect when the instance has multiple interfaces (unlike on normal hypervisor platforms)
Ruckus support seem to think there should be no limitation, which I disagree with based on my own testing and I have fed this back to them.
Ive raised this with our SE and internal discussions seem to suggest that this isnt possible in AWS however Ive not had 100% clarification on this so far and I dont think anyone (at least that Ive spoken to) knows for sure.
Thought id post on here incase anyone else in the community has managed to get this working in AWS? (specifically using multiple vNICs - single interface works fine)
This seems like quite a big drawback on Ruckus's part and absolutely should be possible if they wish to support it being ran on cloud infrastructure like AWS.
Thanks
has anyone successfully created a vSZ instance in AWS using multiple interfaces for the different control planes ? (Management/AP Control/Cluster) like is possible on a traditional hypervisor setup?
The Ruckus vSZ AWS documentation does not mention this and from my own testing so far, vSZ does not detect when the instance has multiple interfaces (unlike on normal hypervisor platforms)
Ruckus support seem to think there should be no limitation, which I disagree with based on my own testing and I have fed this back to them.
Ive raised this with our SE and internal discussions seem to suggest that this isnt possible in AWS however Ive not had 100% clarification on this so far and I dont think anyone (at least that Ive spoken to) knows for sure.
Thought id post on here incase anyone else in the community has managed to get this working in AWS? (specifically using multiple vNICs - single interface works fine)
This seems like quite a big drawback on Ruckus's part and absolutely should be possible if they wish to support it being ran on cloud infrastructure like AWS.
Thanks
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 10:48 AM
Howdy! I have three in AWS, even with close to 1k APs and several hundred switches have we never come close to maxing out a single interface. We have several Radius servers, Cloudpath, Twillo, Hotspot services and DPSK running in and out of the cluster. For me, I've never even once thought about this or experienced this particular setup as an issue
Our VZ AWS cluster works similarly to our multi-interface VZ clusters we host in our data center.
I'll have to run some reports and see what the actual values are.
Our VZ AWS cluster works similarly to our multi-interface VZ clusters we host in our data center.
I'll have to run some reports and see what the actual values are.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 10:57 AM
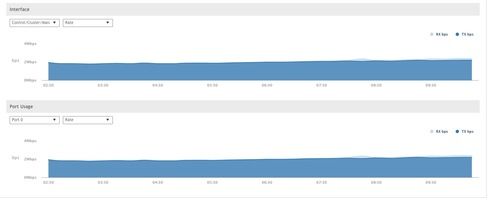
Just checked the interface on a single one of my AWS instances (which looks to be hosting 130 APs) looks to be consuming +- 2mbps sustained over the last 24 hours. System>Cluster>

Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 11:03 AM
Hi Andrew,
yeah I could likely get it working with a single interface however this is mainly from a logical perspective rather than a capacity perspective, being restricted to a single interface heavily limits the flexibility of running vsz in the cloud.
Ive got around 50 ZD5K's worth of APs that I want to shift into AWS VSZ clusters. Separating out the planes to different interfaces means I could apply for example different security groups to the different planes, with for example the management plane accessible in a separate VPC which has multiple VPN endpoints back into our core network and completely segregated from the AP control plane which would be public facing so that our APs can talk back to it.
Also means I dont need to use a public IP address for every node in the cluster. I could put a network load balancer infront of the cluster with a single public IP on there and use that as the NAT control IP for every node in the custer.
Its workable using a single interface, but doesnt scale particularly well.
Cheers,
Jamie
yeah I could likely get it working with a single interface however this is mainly from a logical perspective rather than a capacity perspective, being restricted to a single interface heavily limits the flexibility of running vsz in the cloud.
Ive got around 50 ZD5K's worth of APs that I want to shift into AWS VSZ clusters. Separating out the planes to different interfaces means I could apply for example different security groups to the different planes, with for example the management plane accessible in a separate VPC which has multiple VPN endpoints back into our core network and completely segregated from the AP control plane which would be public facing so that our APs can talk back to it.
Also means I dont need to use a public IP address for every node in the cluster. I could put a network load balancer infront of the cluster with a single public IP on there and use that as the NAT control IP for every node in the custer.
Its workable using a single interface, but doesnt scale particularly well.
Cheers,
Jamie
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 11:08 AM
Sounds compelling.
Best of luck to you!
Best of luck to you!
Labels
-
9210
1 -
AD
1 -
AP Controller Connectivity
2 -
AP Management
5 -
AP reporting
1 -
API Help
1 -
Client Management
4 -
er
1 -
Google
1 -
Guest Access
3 -
ICX Switch Management
1 -
IP Multicast
1 -
Proposed Solution
3 -
RADIUS
2 -
RUCKUS Self-Help
8 -
SmartZone
4 -
SmartZone or vSZ
6 -
Social Media
1 -
Solution Proposed
3 -
string
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
User Management
2 -
vSZ
2 -
Wifi
1 -
WLAN Management
2
- « Previous
- Next »

