- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- SZ / vSZ
- Re: [CVE-2021-44228] Apache Log4j2 RCE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
[CVE-2021-44228] Apache Log4j2 RCE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2021 05:51 PM
Hello.
Our customer is running a Ruckus SmartZone (sz-100) controller.
The version of the controller is 5.1.1.0.598.
The customer asked if the SmartZone has the following this security vulnerabilities.
** Vulnerability: [CVE-2021-44228] Apache Log4j2 RCE
Thank you for your valuable answers to the above questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 06:03 PM
@allan_grohe hi Allan
The advisory seems to be only available in text format (and not pdf) and ALL text advisories return an error and do not load. Other vulns have a pdf version and we can access that but the text version just errors out
Also, given the criticality of the incident it would be good for the advisory to be available without a support account.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 06:17 PM
The text format is working well and we are working on pdf part too, meanwhile please find below content from our official response :
What is the issue?
A vulnerability was found in the Apache Log4j logging library from version 2.0 to 2.14.1. Products utilizing this library are susceptible to remote code execution vulnerability, where a remote attacker can leverage this vulnerability to gain full control of the impacted device.
For more details about this vulnerability, please see https://nvd.nist.gov/vuln/detail/CVE-2021-44228.
What action should I take?
RUCKUS is releasing the fix for these vulnerability through a software update. Since it is a critical issue, all affected customers are strongly encouraged to apply the fix once available.
In case of any questions contact RUCKUS TAC through regular means as described at https://support.ruckuswireless.com/contact-us and refer to this document to validate this entitlement.
Are there any workarounds available?
No
What is the impact on Ruckus products?
The following products are not vulnerable: All Access Points, ZoneDirector, Unleashed, ICX Switches, SPoT/vSPoT, and RUCKUS Cloud.
The following products are under assessment: Cloudpath, IoT, MobileApps, RUCKUS Analytics, and SCI.
The following table describes the vulnerable products, software versions, and the recommended actions.
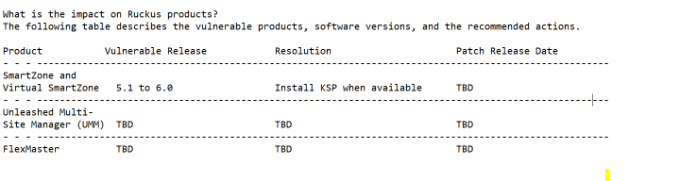
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 07:38 PM
Thanks for the text. Download is working now. Is there an ETA on the patch?
Is it possible to exploit this from the customer side (i.e. though a radius request, wispr login in proxy mode or similar?) Is there any partial mitigation (for example blocking access to the API / port 8443?)
Is there a way te check if a system was infected, and, if so, can it be cleaned in any way? Or is a clean reinstall the only option ?
It's quite worrying and the advisory is extremely thin on details when compared to other advisories / alerts from other vendors
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 07:53 PM
We are waiting for more details/patch ETA (which should be soon) and engineering is working on solution(ksp) as we speak.
The exploit uses JNDI (Java Naming and Directory Interface), this causes the logging library to create an outbound connection to an LDAP server.Until patch is available from engineering firewalling can be used as protection from this attack:
Restrict inbound network access to SmartZone Services (Including the admin interface)
Restrict outbound connections from the SmartZone to the internet and other networks
As this attack requires an outbound connection from the SZ, if the SZ can not get out to the attacker the attack is mitigated.Limit any access from any unauthorized endpoints.
Note : Customer's running on vSZ code 3.6.2 do not have this vulnerability impact and hence do not need any ksp or solutions.
Best Regards
Vineet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 10:28 PM
@diego_garcia_del_rio You should expect this to be triggered from everything which produces a log line. This could be simply be the username of a client trying to authenticate or a SSID of a Rogue AP.
-
9210
1 -
AD
1 -
AP Controller Connectivity
2 -
AP Management
5 -
AP reporting
1 -
API Help
1 -
Client Management
4 -
er
1 -
Google
1 -
Guest Access
3 -
ICX Switch Management
1 -
IP Multicast
1 -
Proposed Solution
3 -
RADIUS
2 -
RUCKUS Self-Help
8 -
SmartZone
4 -
SmartZone or vSZ
6 -
Social Media
1 -
Solution Proposed
3 -
string
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
User Management
2 -
vSZ
2 -
Wifi
1 -
WLAN Management
2
- « Previous
- Next »

