This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- ICX Switches
- Re: ICX 7450 stack with ~100 access switches conne...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ICX 7450 stack with ~100 access switches connected and ~250 VLANs
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 03:26 AM
Hello to All,
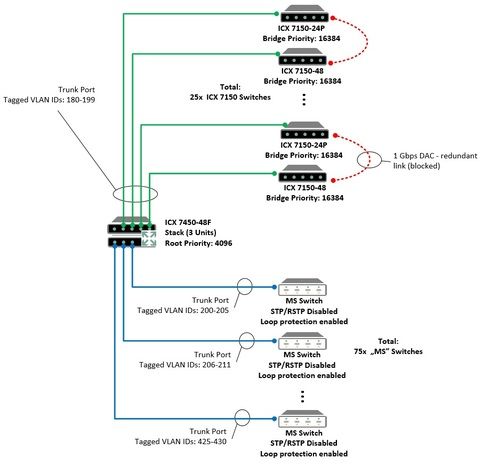
I'm going to design and deploy network infrastructure in huge building based on Brocade ICX switches and other vendor switches (let's say "MS switches"). As I'm new at Brocade, I need to ask for an advice.
The topology will be the star with some redundant links between ICX 7150 (red links in the attached schema).
Core of the network will be the 3-unit stack, consists of ICX 7450-48F switches.
ICX 7150 and "MS switches" (in total, about 100) will act as access switches.
I intend to configure about 250 VLANs on ICX 7450-48F stack, but only a few chosen VLAN IDs will be passed through each trunk port (ranges given in the diagram).
ICX 7450 Stack will be RSTP root with the Root Bridge priority: 4096, ICX 7150 will have Bridge Priority: 16384.
All "MS switches" has RSTP/STP disabled, and only Loop protection enabled.
My questions are:
- Does the ICX 7450 stack handle the calculation of the STP in such large deployment?
- How to properly configure ICX 7450 trunk ports for all "MS Switches" to prevent them from participating in STP topology?
- How to properly configure access ports to prevent from loops on all access switches? Should I use 'stp-bpdu-guard' or 'stp-protect' or something else?
- Should I give up with redundant connections and give up at any kind of STP (clear star topology)?
I'm going to design and deploy network infrastructure in huge building based on Brocade ICX switches and other vendor switches (let's say "MS switches"). As I'm new at Brocade, I need to ask for an advice.
The topology will be the star with some redundant links between ICX 7150 (red links in the attached schema).
Core of the network will be the 3-unit stack, consists of ICX 7450-48F switches.
ICX 7150 and "MS switches" (in total, about 100) will act as access switches.
I intend to configure about 250 VLANs on ICX 7450-48F stack, but only a few chosen VLAN IDs will be passed through each trunk port (ranges given in the diagram).
ICX 7450 Stack will be RSTP root with the Root Bridge priority: 4096, ICX 7150 will have Bridge Priority: 16384.
All "MS switches" has RSTP/STP disabled, and only Loop protection enabled.
My questions are:
- Does the ICX 7450 stack handle the calculation of the STP in such large deployment?
- How to properly configure ICX 7450 trunk ports for all "MS Switches" to prevent them from participating in STP topology?
- How to properly configure access ports to prevent from loops on all access switches? Should I use 'stp-bpdu-guard' or 'stp-protect' or something else?
- Should I give up with redundant connections and give up at any kind of STP (clear star topology)?

4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2018 05:58 AM
According to the information contained in "RSTP scaling recommendations and best practices" document, my proposal of use of R-PVST+ or even RSTP in not good due to the large number of VLANs configured (~250). The only option seems to be MSTP.
Does anybody has a experience with that in such complex deployment?
Does anybody has a experience with that in such complex deployment?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2018 03:27 PM
The switches will support RPVST, but you may see some CPU overhead based on the number of VLANs. Loop-detection would be the correct answer on the MS-Switches to stop a loop from killing the network. I would suggest MSTP for the network and also pose the question on why you want to disable Spanning-tree on the MS-Switches. It would be a better design to choose a version of STP that will go end-to-end in your network. MSTP is supported by most real switch vendors.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2018 12:56 AM
Hi David,
Thank you for your answer. I decided to use MSTP only on Brocade switches (core/access) with stp-bpdu-guard enabled for ports dedicated for MS-Switches. I have also decided to configure errdisable for each port. I would like to avoid recalculation of STP tree each time when all the MS-switches will be restarted.
Do you see any threats related to the lack of MSTP on MS-switches ?
Thank you for your answer. I decided to use MSTP only on Brocade switches (core/access) with stp-bpdu-guard enabled for ports dedicated for MS-Switches. I have also decided to configure errdisable for each port. I would like to avoid recalculation of STP tree each time when all the MS-switches will be restarted.
Do you see any threats related to the lack of MSTP on MS-switches ?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2018 06:50 AM
If you use BPDU-guard on the ports that connect to other switches, the port will be error-disabled. You just need to use the mstp disable ethernet x/x/x command on the ports to the MS-Switches to disable MSTP going to those devices.
Labels
-
7250
1 -
802.3af PoE
1 -
802.3at PoE
1 -
AAA
1 -
ACL
1 -
auto-provision
1 -
auto-provisioning
1 -
Cluster synchronization
1 -
Crypto Keys
1 -
Deployment
1 -
dhcp-66
1 -
fastiron-10
1 -
fastiron-8
1 -
Firmware Upgrade
4 -
ICX
3 -
ICX 7150-C12p
1 -
ICX switch
2 -
ICX Switch Management
9 -
ICX-7150-C12
1 -
ICX-7550
1 -
ICX-8200
1 -
Installation
2 -
not enough electricity
1 -
overlad
1 -
Override PoE Operating Mode
1 -
PD overload
1 -
Poe
2 -
PoE mode.
1 -
power limitations
1 -
Proposed Solution
1 -
RADIUS
1 -
Routing
2 -
RUCKUS Self-Help
2 -
stack
1 -
stack password
1 -
Stacking
1 -
tftp
1 -
Upgrade
1 -
Upgrade path
1 -
We
1 -
zero-touch
1
- « Previous
- Next »

