- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- Community Services
- Community and Online Support Services
- Re: Advice on how to implement a 12port ICX7150
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 11:05 AM
Hello All,
We are currently working on a way to setup a sort of out-of-band management system in our small environment. Basically a mini PC will be connected to the 12port ICX7150 and the 12port will be connected to other ruckus switches in our other sites. The end goal is that if/when a resource in one of the sites isn't responding we can simply get on the mini pc remotely and then get to the site with the the 12port and its connection to that site's switch and subsequently its resources . The topology is akin to a hub and spoke but instead of all devices being connected to one central device we want the 12port ICX7150 to connect to all the sites we have. The problem is I am unsure of how the configuration on the 12port would be and what configuration would be on the switches on our remote sites as I don't want to cause any loops or broadcast storms I was wondering how I may achieve this goal. I appreciate any help or any advice on the matter.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2023 01:26 AM
Hi JD ,
Thank You For Posting Your Requirement !!!
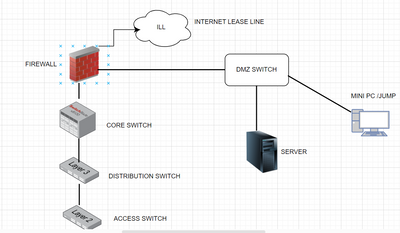
Let us understand you concern with a diagram first !!
If you are planning to have mini pc basically a jump server installed in your infrastructure first .
Then it should be planned in the DMZ zone as mention in the above diagram .
The Firewall should have appropriate policy configuration for this mini server so that only management network should be access from there.
Take SSL VPN connectivity from outside world on your firewall .Initiate a RDP session of your mini pc and start doing your stuff
CONFIGURATION DETAILS ON DMZ SWITCH :
Design A /30 Free Subnet for connectivity to your firewall and dmz switch and assign 1 ip on firewall and other on dmz switch
Configure the management vlan on dmz switch and assign the physical ports to the same vlan.
From each of your infrastructure device take a physical cable and connect its obb port with dmz switch .
Configure the ssh on the switch and default gateway ip as the firewall interface ip
Also assign an acl rule for ssh access so that you can only access via mini pc
CONFIGURATION ON FIREWALL :
Configure the policy from /30 free subnet on port connecting the dmz switch
Create a policy allowing ssl vpn subnet / user to allow mini pc
Create another policy to allow this mini pc to access the required subnet
Note : Above diagram is just a reference diagram not a complete one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 08:23 AM
Setting up a Out of band management system using a 12 port switch where all other swtchs' management interfaces connect back to one of the 12 ports should be fairly easy. with a mini PC on the 12 port unit.
on the 12 port switch :
make sure you have the SPR version of the Image on there.
Licenses should not be an issues as all devices will be a part of the same single vlan.
all you would need to set up is a Vlan : you can create one or you can use the default one the vlan 1
define a SVI/vlan interface for it with an IP address defined on there.
and that should do :
if you choose to use vlan 1 : that will save you the trouble of port association as all ports are untagged to it by default
and post that you once you have the connections set up : all you would need to ensure all are a part of the same network
on the other switches : depending on the code version used you can have either an management interface seperately like in SPR variant where you can access it using interface management 1 command and then set an IP there.
OR in the SPS version set an ip directly on the switch : and use the management port to connect to the 12 port unit.
this should get you started.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 12:14 PM
Hello,
Thank you for the reply! Just so I understand correctly, on the 12 port switch (with the SPR firmware) I would need to set a VLAN up (or use default VLAN 1) and then untag the port where the mini pc is connected on that VLAN, setup up a router-interface on that VLAN and an IP for it. The next part is what I'm a little confused by, so then I would tag the ports on the 12port switch with the VLAN that I made and plug the other switches at the other sites to those ports and make sure that the ports on the switch in the other sites are tagged as well on the same VLAN? Am I understanding that correctly? If so, then would I still be able to get to the devices at the remote sites, even with the different IP address and VLAN? Apologies in advance for the intrusive questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2023 12:15 AM - edited 02-17-2023 12:22 AM
no if you use the default vlan : vlan 1 on the 12 port switch and the management port on the other switches : you would not need to tag : as for the default vlan all ports are untagged and the management port on a given unit works as untagged only, hence that should make it easier.
you can create a vlan and then do untag of all ports to the new vlan that should also work well.
if you use tagging as you mentioned, it would be In band Management network, where a subnet that is a part of the network that you have is used for management, here in this usually as its part of the network and not isolated like OOBM : you can access even with different ips.
in these kinds of set up, usually where the intervlan routing or routing takes place : ACLS are put in that help avoid cross subnet access locking it down to one subnet only.
and it can be a bit detail oriented [ not rocket science ... but can be a bit tricky ]
hence your approach of OOBM with either a new vlan or default vlan on the 12 port switch with all ports untagged and using mgmt interface on the other switches, should be easier.
not to forget the definition of subnet for that [ assigning of IPs on the 12 port one and on management interfaces ].
No worries, I'm glad we could help out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 09:42 AM
Adding to the thread . Please check the below quick start up guide for initial steps on working with the switch. I hope this helps.
Quick start guide :
Below link has details with accessing support and software details.
https://docs.commscope.com/bundle/icx-quickstart/page/GUID-9E975253-3763-4EB0-A0C4-37D4A0AA2DBA.html
Refer Layer 2 switching guide for all details on vlan config and spanning tree details
Thanks
-
Access points
1 -
administration
1 -
AP Management
1 -
API Help
1 -
Code Flash Free Space = 0
1 -
community
2 -
ios
1 -
mac
1 -
port-fast
1 -
portfast
1 -
R500
1 -
R750
1 -
Ruckus
2 -
spanning-tree
1 -
spanningtree
1 -
top contributors
1 -
ubuntu
1 -
Unleashed
2
- « Previous
- Next »