This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- ZD
- Re: disconnects and latency
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
disconnects and latency
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2015 09:27 AM
I'm getting short disconnects or maybe traffic issues. The most notable symptom is a hesitation in an RDP (Term Serv) session. It's long enough for the user to notice and miss a keystroke or mouse click, but too short for the session to fail. This happens in multiple locations, multiple APs, from multiple laptops and thin clients.
A quick continuous ping test to the device shows the latency jumping from 1ms to 1500ms for one ping every miniute, and keeps repeting. This may be nothing.
I'm also seeing a couple entries on the syslog that I'd really like to know what is causing them.
" Jun 19 06:51:53 AP-09 user.info kernel: >>>>>> ar5416GetNf: Failed to read CCA reg"
Call this AP-1 and it repetes every 8 minutes.
On another AP, we'll call it AP-2
"Jun 18 12:44:01 AP-07 daemon.warn Eved: STA-DISASSOC-REASON,nimac=78:4b:87:6f:73:94,func=ieee80211_send_mgmt,line=3700,hint=send station disassociate,rx_rssi=41,ack_rssi=0,reason=0,freq=2462,chan=11,stats=(67,4482,73,5464)"
"Jun 18 12:44:07 AP-07 user.notice root: APMGR-Out-Of-Run-State: ------ Sole Run debug info - Start -----"
Followed by debug and restart information. This repetes but not often and I don't a specific pattern, at least not yet.
If anyone has any ideas I'd really appreciate the help.
The problem may have been around for a long time. I've gone over the config way too many times and had an outside Ruckus partner look it over, so I don't think its a config issue. This is also across 2 firmware version, currently at 9.7.0.0.220 and I don't want to update because of the changes to WPA.
Thanks
A quick continuous ping test to the device shows the latency jumping from 1ms to 1500ms for one ping every miniute, and keeps repeting. This may be nothing.
I'm also seeing a couple entries on the syslog that I'd really like to know what is causing them.
" Jun 19 06:51:53 AP-09 user.info kernel: >>>>>> ar5416GetNf: Failed to read CCA reg"
Call this AP-1 and it repetes every 8 minutes.
On another AP, we'll call it AP-2
"Jun 18 12:44:01 AP-07 daemon.warn Eved: STA-DISASSOC-REASON,nimac=78:4b:87:6f:73:94,func=ieee80211_send_mgmt,line=3700,hint=send station disassociate,rx_rssi=41,ack_rssi=0,reason=0,freq=2462,chan=11,stats=(67,4482,73,5464)"
"Jun 18 12:44:07 AP-07 user.notice root: APMGR-Out-Of-Run-State: ------ Sole Run debug info - Start -----"
Followed by debug and restart information. This repetes but not often and I don't a specific pattern, at least not yet.
If anyone has any ideas I'd really appreciate the help.
The problem may have been around for a long time. I've gone over the config way too many times and had an outside Ruckus partner look it over, so I don't think its a config issue. This is also across 2 firmware version, currently at 9.7.0.0.220 and I don't want to update because of the changes to WPA.
Thanks
10 REPLIES 10
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 09:54 AM
Hi Randall,
Assuming you use a PSK method on your scanners, you don't need to use the CLI to reconfigure WLAN options.
From your ZD WebUI, Configure/WLANs page, Edit your present WLAN used by scanner clients. We *typically*
suggest a PSK authentication using WPA2 Method, and AES Algorithm. However, to try and troubleshoot your issues
after upgrade, you can try changing these to WPA-Mixed Method, with Auto (TKIP) Algorithm. Here are screen shots.
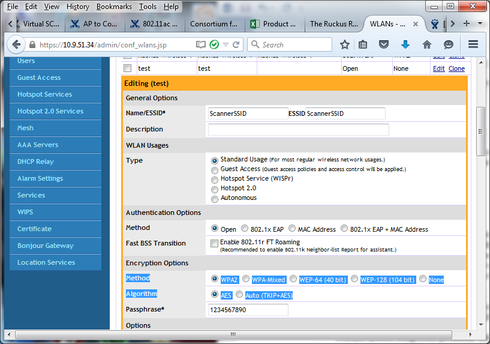
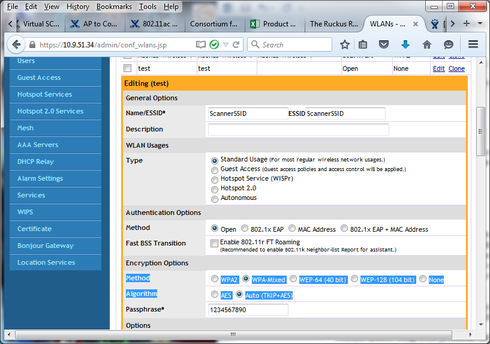
Assuming you use a PSK method on your scanners, you don't need to use the CLI to reconfigure WLAN options.
From your ZD WebUI, Configure/WLANs page, Edit your present WLAN used by scanner clients. We *typically*
suggest a PSK authentication using WPA2 Method, and AES Algorithm. However, to try and troubleshoot your issues
after upgrade, you can try changing these to WPA-Mixed Method, with Auto (TKIP) Algorithm. Here are screen shots.


Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 10:16 AM
You're missing a very important point. This is not a theoretical discussion of what happens if I upgrade to 9.8. I DID upgrade and it wouldn't work and I opened a case with Ruckus which was escalated to "engineering". While waiting for their response I downgraded so my system would be usable. When they got back to me they said I could enable the WPA/TKIP for each SSID via the command line. I didn't try upgrading AGAIN to 9.8 and making the CLI change because I can't afford to take the scanners off-line again.
As for what is RECOMMENDED, it's irrelevant since my scanners do not support WPA2
Now if there is some kind of document fix for the problem in 9.8 that's different story. Send me a link to the information and I'll see what can be done.
As for what is RECOMMENDED, it's irrelevant since my scanners do not support WPA2
Now if there is some kind of document fix for the problem in 9.8 that's different story. Send me a link to the information and I'll see what can be done.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 11:42 AM
The real question is what type of authentication does your (mfgr?) scanner have configured?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 11:52 AM
encryp is WPA/TKIP auth is none.
And until we role-out new ones that's the way its going to stay. Ya I know..
And until we role-out new ones that's the way its going to stay. Ya I know..
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 02:47 PM
Hi Randall,
We have a couple knowledge base articles related to working with barcode
readers and handheld scanners. I have a feeling your scanners might only
support 802.11b/g too, if they don't have WPA2. I'm glad they work on your
previous version, and that you have a backup configuration on that release
when you rolled back.
If you have a dedicated WLAN for scanners is helpful, so you can apply
changes just to that WLAN, but it might take some testing after upgrading to
9.8 again (weekend?) to test Let me give you these.
KBA-3278: How to enable TKIP on ZD 9.8+
https://support.ruckuswireless.com/answers/000003278
This may be the article you were referred to before, providing CLI commands after the suggestions I offered. It does require an SSH login to your ZD to run the CLI command under config mode, and will override WebUI settings in the future, but will setup WPA1/TKIP, that should be compatible with your age scanner product.
I want to add the WLAN config command "no ofdm-only" to insure 802.11b only
clients should be able to connect. I tested the command syntax on my ZD.
ruckus# config
You have all rights in this mode.
ruckus(config)# wlan ScannerSSID
The WLAN service 'ScannerSSID' has been loaded. To save the WLAN service, type 'end' or 'exit'.
ruckus(config-wlan)# no ofdm-only
The mgmt-tx-rate will be set to the same value as bss-minrate due to ofdm-only change.
The command was executed successfully. To save the changes, type 'end' or 'exit'.
ruckus(config-wlan)#
ruckus(config-wlan)# open wpa passphrase 1234567890 algorithm TKIP
The command was executed successfully. To save the changes, type 'end' or 'exit'.
ruckus(config-wlan)#
ruckus(config-wlan)# exit
The WLAN service 'ScannerSSID' has been updated and saved.
Your changes have been saved.
ruckus(config)# exit
Your changes have been saved.
ruckus#
KBA-1765: Barcode readers and Handheld scanner issue
https://support.ruckuswireless.com/answers/000001765
Has a .pdf with advice on alternative test with an Open Auth test (would require changing a scanner) if the WPA/TKIP only configuration didn't work.
If a scanner can connect to Open Auth, can it connect if you hide the SSID?
Yes or no, if you need to use Open for the scanners, you can apply an L2
MAC filter ACL, to only allow scanner connections, as a possible alternative?
Forum community members may have some inputs too, otherwise I hope
this is helpful.
(if the last article doesn't appear yet, I just did an edit, so it might be a few min)
We have a couple knowledge base articles related to working with barcode
readers and handheld scanners. I have a feeling your scanners might only
support 802.11b/g too, if they don't have WPA2. I'm glad they work on your
previous version, and that you have a backup configuration on that release
when you rolled back.
If you have a dedicated WLAN for scanners is helpful, so you can apply
changes just to that WLAN, but it might take some testing after upgrading to
9.8 again (weekend?) to test Let me give you these.
KBA-3278: How to enable TKIP on ZD 9.8+
https://support.ruckuswireless.com/answers/000003278
This may be the article you were referred to before, providing CLI commands after the suggestions I offered. It does require an SSH login to your ZD to run the CLI command under config mode, and will override WebUI settings in the future, but will setup WPA1/TKIP, that should be compatible with your age scanner product.
I want to add the WLAN config command "no ofdm-only" to insure 802.11b only
clients should be able to connect. I tested the command syntax on my ZD.
ruckus# config
You have all rights in this mode.
ruckus(config)# wlan ScannerSSID
The WLAN service 'ScannerSSID' has been loaded. To save the WLAN service, type 'end' or 'exit'.
ruckus(config-wlan)# no ofdm-only
The mgmt-tx-rate will be set to the same value as bss-minrate due to ofdm-only change.
The command was executed successfully. To save the changes, type 'end' or 'exit'.
ruckus(config-wlan)#
ruckus(config-wlan)# open wpa passphrase 1234567890 algorithm TKIP
The command was executed successfully. To save the changes, type 'end' or 'exit'.
ruckus(config-wlan)#
ruckus(config-wlan)# exit
The WLAN service 'ScannerSSID' has been updated and saved.
Your changes have been saved.
ruckus(config)# exit
Your changes have been saved.
ruckus#
KBA-1765: Barcode readers and Handheld scanner issue
https://support.ruckuswireless.com/answers/000001765
Has a .pdf with advice on alternative test with an Open Auth test (would require changing a scanner) if the WPA/TKIP only configuration didn't work.
If a scanner can connect to Open Auth, can it connect if you hide the SSID?
Yes or no, if you need to use Open for the scanners, you can apply an L2
MAC filter ACL, to only allow scanner connections, as a possible alternative?
Forum community members may have some inputs too, otherwise I hope
this is helpful.
(if the last article doesn't appear yet, I just did an edit, so it might be a few min)
Labels
-
DHCP
1 -
IP lease
1 -
license snmp
1 -
Proposed Solution
1 -
Ruckus
1 -
server
1 -
VLAN
1 -
wap
1 -
zone director
1 -
ZoneDirector
1

