- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Lennar Support
- RUCKUS Support for Lennar Homes
- Re: AP R510 can't connect to ICX7150 "ICX Switch i...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AP R510 can't connect to ICX7150 "ICX Switch is Connecting"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2023 11:47 PM
I have one ICX7150 and two R510 AP .
ICX7150 - FW Version:09.0.10dT211 (SPS09010d.bin)
R510 - FW version: 200.13.6.1.319
R510 can't connect to the ICX switch and shows "ICX Switch is Connecting". It used to work with the old FW release, what is going on ? SSH is enabled, I can manually SSH to the Switch or AP
I saw a lot of other questions about the same topic but nothing there helped
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 08:29 PM
Hi Vásquez_Fer
No luck. After creating an RSA key along with the original ec384 key .. ssh is showing the following
client_input_hostkeys: received duplicated ssh-rsa host key
Anyway, here is the show logging saying that the SSH access is rejected
SSH@ICX7150-C12-SWITCH(config)#show logging
Syslog logging: enabled ( 0 messages dropped, 0 flushes, 0 overruns)
Buffer logging: level ACDMEINW, 150 messages logged
level code: A=alert C=critical D=debugging M=emergency E=error
I=informational N=notification W=warning
Static Log Buffer:
Oct 06 19:00:15:I:System: Stack unit 1 POE PS 1, Internal Power supply with 124000 mwatts capacity is up
Dynamic Log Buffer (4000 lines):
Oct 06 12:37:22:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:36:53:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:36:25:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:35:56:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:35:28:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:34:59:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:34:03:I:Security: Web login by super from src IP 192.168.1.48
Oct 06 12:34:03:I:Security: Web login by super from src IP 192.168.1.48
Oct 06 12:33:59:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:33:41:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:33:22:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:33:08:I:Security: ssh login by super from src IP 192.168.1.48 from src MAC a483.e7c4.9475 to PRIVILEGED EXEC mode
Oct 06 12:33:04:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:32:50:I:Security: ssh login by super from src IP 192.168.1.48 from src MAC a483.e7c4.9475 to USER EXEC mode
Oct 06 12:32:45:N:sshd: SSH access by user super from src 192.168.1.3 rejected, 0 attempt(s)
Oct 06 12:32:43:I:sshd: Failed publickey for super from 192.168.1.48 port 51190 ssh2
--More--, next page: Space, next line: Return key, quit: Control-c
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 07:39 AM - edited 02-02-2023 07:53 AM
Hi @ohabib
Hope you are doing well !
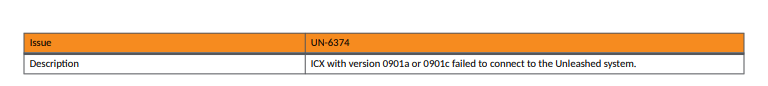
Checking the RUCKUS data it appears that there is an ongoing issue from the unleashed side with this issue that should be fixed in future versions.
What I recommend is to be on the recommended version on Switch based on the support portal.
Best Regards
Fernando Vasquez
-
Access point
3 -
Access points
5 -
all lights blinking after reset icx 7150 switch
1 -
Amber
1 -
Amber System
2 -
AP
1 -
Boot mode
1 -
bootloader
1 -
cli
1 -
Compatibility
1 -
Console
1 -
console access
1 -
dns
1 -
eero
2 -
eps
1 -
Frontier
1 -
Green Power
2 -
Hard reset
1 -
Heartbeat
1 -
Heartbeat loss recurring
2 -
Help
2 -
Help Needed
2 -
i Al
1 -
ICX
2 -
ICX 7150-C12p
7 -
ICX switch
4 -
ICX Switch Disconnected
1 -
ICX Switch Management
2 -
ICX-7150-C12
2 -
ICX-7150-C12P
1 -
Important Announcement
1 -
Installation
1 -
Internet Issue
2 -
Ive been
1 -
Lennar
3 -
Lennar Home
2 -
Lennar homes
25 -
Management Port
1 -
New
1 -
No POE
2 -
No power via Ethernet
1 -
password
1 -
Please
1 -
Poe
1 -
Poe not working
1 -
Power Outage
1 -
Power Outtage
1 -
Proposed Solution
1 -
R510
2 -
r510 no power
2 -
REBOOT
1 -
Recovery
1 -
Red LED
1 -
Remote access
1 -
Reset ICX username password
1 -
Return
1 -
RMA
3 -
Ruckus
2 -
Ruckus ICX 7150-C12P
4 -
RUCKUS Self-Help
1 -
RUKUS 7150 c12p
1 -
Setup
1 -
Software Recovery
1 -
Solution Proposed
1 -
Solution Proposed warranty
1 -
SPR
1 -
SSH
1 -
Switch
1 -
Telnet
1 -
Unleashed
3 -
Unresolved Issue
1 -
Upgrade
3 -
Upgrading R510
1 -
User Management
1 -
username
1 -
VPN streaming fail proxy not working Amazon prime video
1 -
Wifi
1 -
Wifi6
1 -
Wireless
3
- « Previous
- Next »