This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- Community Services
- Community and Online Support Services
- Re: Architecture Question/Help
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Architecture Question/Help
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2013 07:23 AM
Hi All,
First time posting here. We have recently deployed a Zone Director 1100 and several zf7363 APs in our main office. So far the response has been great and everything is working smoothly. Eventually we would like to deploy APs in our branch offices as well and hopefully still use the Zone Director in our main office as the controller.
The challenge I am facing is that the ZD and APs all are totally isolated from our corporate LAN/WAN. They sit behind their own firewall and only provide internet access to our users. All of the APs to be deployed at the branch offices would be arranged in a like topology. When we spec'd the system we did not take this isolation into account unfortunately. Without the remote APs being able to communicate to the Zone Director over the corporate WAN I'm not exactly sure of the best path forward.
Would the recommended approach/design be to put the Zone Director and APs into a DMZ and then talking back and forth over the public internet? I'm not sure what sort of in/out traffic the zone director uses to communicate to the APs and what ports are in use.
I'm hoping there is a more simple approach that will allow the APs to operate autonomously but still be managed centrally. I've read a bit about the Flex Master platform which sounds like it might suit our needs but could be way overkill since we are only going to have about 25-30 APs total throughout our company.
Any advice or input is appreciated.
First time posting here. We have recently deployed a Zone Director 1100 and several zf7363 APs in our main office. So far the response has been great and everything is working smoothly. Eventually we would like to deploy APs in our branch offices as well and hopefully still use the Zone Director in our main office as the controller.
The challenge I am facing is that the ZD and APs all are totally isolated from our corporate LAN/WAN. They sit behind their own firewall and only provide internet access to our users. All of the APs to be deployed at the branch offices would be arranged in a like topology. When we spec'd the system we did not take this isolation into account unfortunately. Without the remote APs being able to communicate to the Zone Director over the corporate WAN I'm not exactly sure of the best path forward.
Would the recommended approach/design be to put the Zone Director and APs into a DMZ and then talking back and forth over the public internet? I'm not sure what sort of in/out traffic the zone director uses to communicate to the APs and what ports are in use.
I'm hoping there is a more simple approach that will allow the APs to operate autonomously but still be managed centrally. I've read a bit about the Flex Master platform which sounds like it might suit our needs but could be way overkill since we are only going to have about 25-30 APs total throughout our company.
Any advice or input is appreciated.
5 REPLIES 5
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2013 08:02 AM
Hi Bradford,
You could potentially do a VPN tunnel through your corporate WAN. Unless you are in turn tunneling all of the AP traffic back to the controller (which is fairly rare), the traffic through the WAN would be minimal. Watch for MTU issues.
Here's a KB article (that is a little rough..) detailing port requirements for various deployments. https://support.ruckuswireless.com/an...
You could potentially do a VPN tunnel through your corporate WAN. Unless you are in turn tunneling all of the AP traffic back to the controller (which is fairly rare), the traffic through the WAN would be minimal. Watch for MTU issues.
Here's a KB article (that is a little rough..) detailing port requirements for various deployments. https://support.ruckuswireless.com/an...
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2013 08:41 AM
Thanks Keith.
Per our security policy wireless has to remain completely isolated from the corporate WAN unfortunately. I could do site to site VPN tunnels from the Wireless network FWs but was hoping to avoid this layer of complexity.
I'm sort of curious how FlexMaster could fit into this since in the product description I've read
"Now, Ruckus Wi-Fi systems can be securely controlled, monitored, and upgraded from anywhere in the world, over the Internet or a private IP network — with FlexMaster. It’ a complete management platform for building and managing Enterprise and Carrier-Grade Wi-Fi Service Infrastructures."
I'm guessing the FlexMaster box would have to sit in a DMZ to manage wireless networks over the internet, but what about the APs?
Sorry if I'm not being clear. I can knock up a diagram if that would help
Per our security policy wireless has to remain completely isolated from the corporate WAN unfortunately. I could do site to site VPN tunnels from the Wireless network FWs but was hoping to avoid this layer of complexity.
I'm sort of curious how FlexMaster could fit into this since in the product description I've read
"Now, Ruckus Wi-Fi systems can be securely controlled, monitored, and upgraded from anywhere in the world, over the Internet or a private IP network — with FlexMaster. It’ a complete management platform for building and managing Enterprise and Carrier-Grade Wi-Fi Service Infrastructures."
I'm guessing the FlexMaster box would have to sit in a DMZ to manage wireless networks over the internet, but what about the APs?
Sorry if I'm not being clear. I can knock up a diagram if that would help
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2013 02:14 PM
FlexMaster does have it's own tunneling capability which is what's being referred to above. And it can support the following:
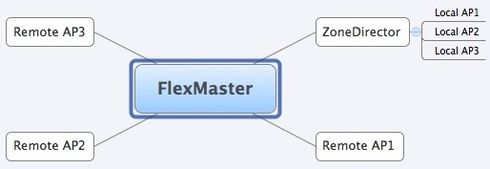
Which is I think close to what you are looking for. You can download it from our website, and it comes with a 10 client license (ZD is one client) for evaluation purposes. Hint - after installation drop iptables and make sure :80 and :443 are open

Which is I think close to what you are looking for. You can download it from our website, and it comes with a 10 client license (ZD is one client) for evaluation purposes. Hint - after installation drop iptables and make sure :80 and :443 are open
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2014 06:03 AM
Hi,
I want to make comment that ZD requires as much licenses from Flexmaster, as APs it can manage (ZD license size), even if there is ust one AP. So Zd1106 uses 6 Flexmaster licences, not 1, and, for example, ZD1112 need 12 licenses.
So you can connect only ZD1106 to Flexmaster with evaluation license.
Also there is no much sense to manage ZD by Flexmaster in you case, as it is on your site and there is much more management features in ZD (and you need access to it anyway).
It is possible to install ZD in DMZ, open proper ports, and install APs on remote sites after Firewall, making address translation for neccessary ports, without VPN.
It will work (if delays on WAN are less than 50-100-msec), but it is not what you usually want to do. Vpn is more safe, but it adds delays, so requirement to WAN become even higher. If delays are too big, clients can time-out autentication and fail to connect.
Unfortunately, you can't expect to have centralized management and no communication between sites, it is unrealistic wish.
Some other vendors (Aruba, for example) which mainly use only tunneled connection for APs, support architecture when AP itself creates Ipsec tunnel to controller over Internet, which is really handy for remote brunches. But it's not required really often, or Ruckus would implemented it too.
Hope it helps,
Eizens
I want to make comment that ZD requires as much licenses from Flexmaster, as APs it can manage (ZD license size), even if there is ust one AP. So Zd1106 uses 6 Flexmaster licences, not 1, and, for example, ZD1112 need 12 licenses.
So you can connect only ZD1106 to Flexmaster with evaluation license.
Also there is no much sense to manage ZD by Flexmaster in you case, as it is on your site and there is much more management features in ZD (and you need access to it anyway).
It is possible to install ZD in DMZ, open proper ports, and install APs on remote sites after Firewall, making address translation for neccessary ports, without VPN.
It will work (if delays on WAN are less than 50-100-msec), but it is not what you usually want to do. Vpn is more safe, but it adds delays, so requirement to WAN become even higher. If delays are too big, clients can time-out autentication and fail to connect.
Unfortunately, you can't expect to have centralized management and no communication between sites, it is unrealistic wish.
Some other vendors (Aruba, for example) which mainly use only tunneled connection for APs, support architecture when AP itself creates Ipsec tunnel to controller over Internet, which is really handy for remote brunches. But it's not required really often, or Ruckus would implemented it too.
Hope it helps,
Eizens
Labels
-
Access points
1 -
administration
1 -
AP Management
1 -
API Help
1 -
Code Flash Free Space = 0
1 -
community
2 -
ios
1 -
mac
1 -
port-fast
1 -
portfast
1 -
R500
1 -
R750
1 -
Ruckus
2 -
spanning-tree
1 -
spanningtree
1 -
top contributors
1 -
ubuntu
1 -
Unleashed
2
- « Previous
- Next »

