- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- Cloudpath
- Re: cloudpath property management user traffic pro...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2021 01:12 AM
Hello,
Is there any way to select different user traffic profiles (smartzone) when creating users based on cloudpath property management system?
Thanks.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2021 08:06 AM
Hi Norbert,
Yes, you can use the Policy engine in Cloudpath to return a different user-role to SmartZone. You can use the UNIT name as the DPSK reference name in a policy. Using that policy, you can provide different Filter ID’s back to SmartZone.
I have a guide here, that will show an example of providing a Bronze level of service to users (25 Mbps up and down) vs Gold level of service (100 Mbps up and down) to users, but the user roles can be defined however you need to in SmartZone.
Let us use an example of a Bronze vs Gold service.
Overview:
In Cloudpath we will create units and pre-pend that unit with a service level bronze vs gold.
In Cloudpath we will create a policy that returns the Ruckus-User-Group as "bronze" to SmartZone and likewise for "Gold"
In SmartZone we will create two Traffic Profiles; Bronze giving 25 Mbps up and 25 Mbps down, and Gold giving 100 Mbps up and 100 Mbps down.
Cloudpath; create a bronze and a gold unit.
- Click on Managed Access | Property Management
- Click on the property that you want to change a unit to
- Click on Units Tab
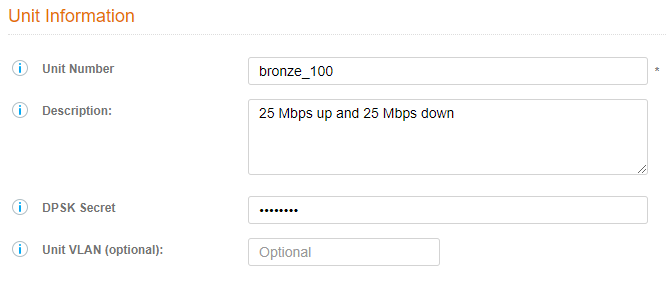
- Create a Unit; pre-pend the word “bronze” in the unit number:
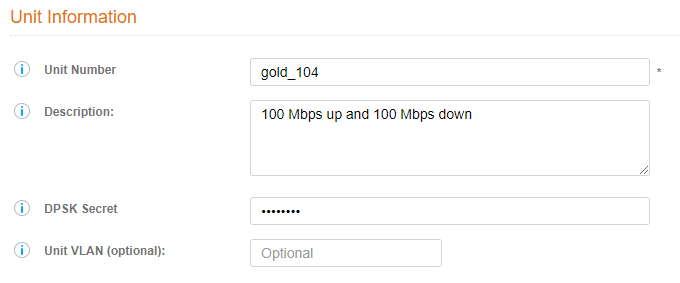
- Do the same for a “gold” unit:
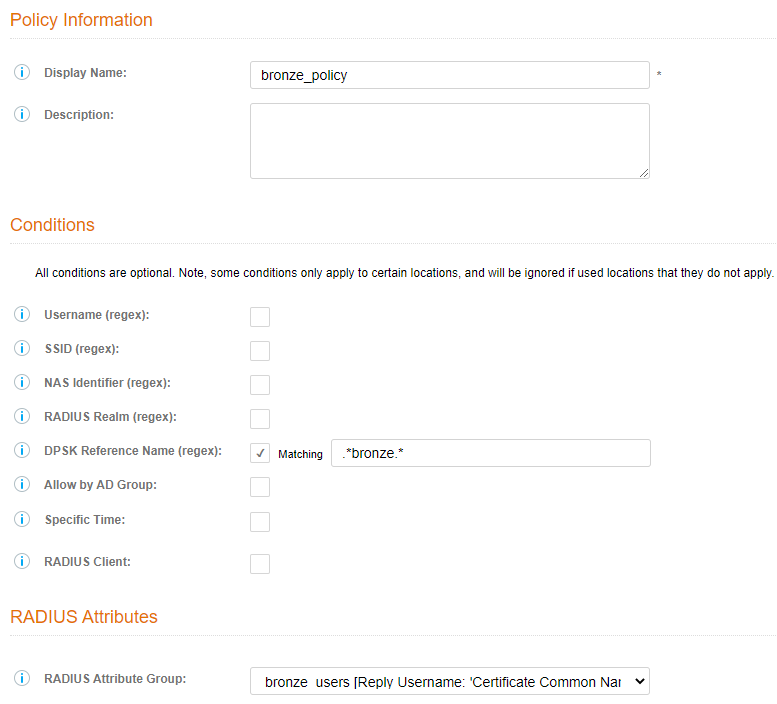
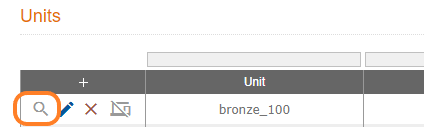
If you look at the bronze unit, you can see that the DPSK reference name is named as <property_name>_<unit number>. We can use this value to build a RADIUS DPSK policy on:
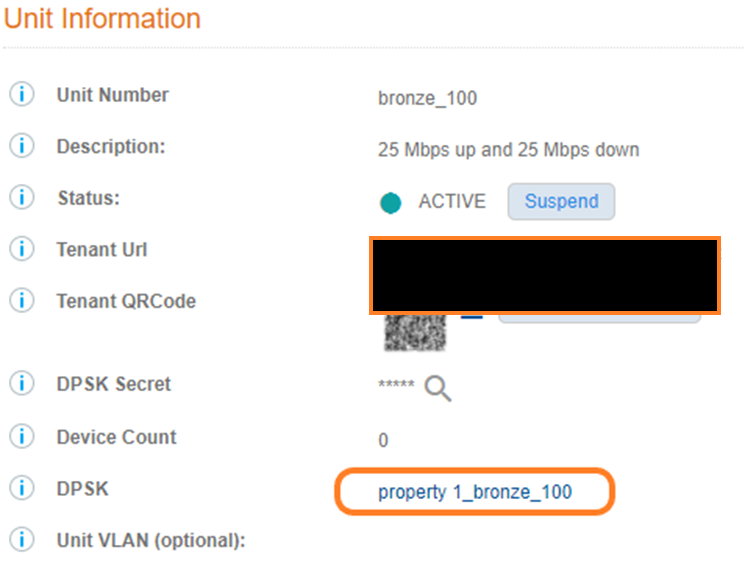
In Cloudpath, let’s create 2 RADIUS policies to return the user-role to SmartZone
- Click on Configuration | Policies
- Click the RADIUS Attribute Groups Tab
- Click on Add RADIUS Attribute Group
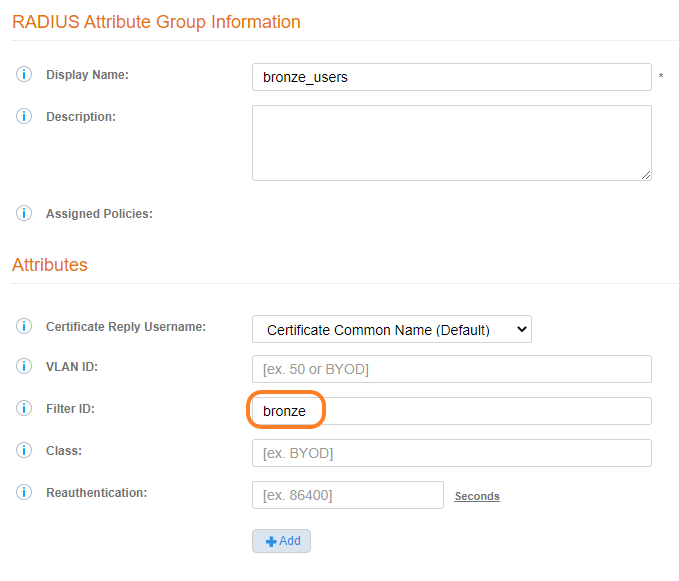
- Create a attribute group that returns the “Filter ID” as “bronze”
- Click on Save
- Let’s do another policy for “gold”, so click on “Add RADIUS Attribute Group” again
- Create a gold attribute group that returns the “Filter ID” as “gold”
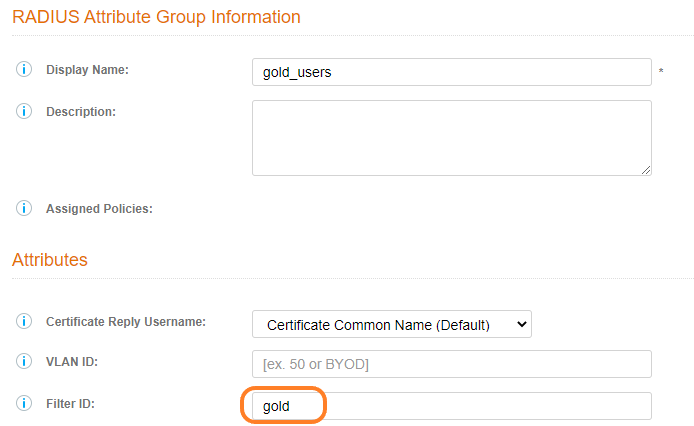
- Click on Save
- Click the Policies Tab | Add Policy

- Create a “bronze_policy” that returns the Bronze Attribute group that you just created. We are going to use the DPSK reference name for the Unit (remember, we pre-pended the word “bronze” to it):
- Make sure that you have a “.*” at the beginning and end, which means, match anything, then the word bronze, and match anything after that. This is REGEX, and I typically use a few different sites to test these things.
- Make sure that you select the correct RADIUS attribute group you just created for BRONZE
- Click on Save.
NOTE:
To test REGEX, I like to use “https://regex101.com”; this can help with syntax, example; lets make sure the regex I wrote will catch the DPSK reference name of the bronze unit and not the gold unit:
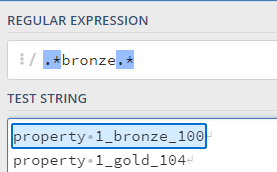
We can see that the REGEX will only match the first entry.
- Lets do a policy for “gold” users
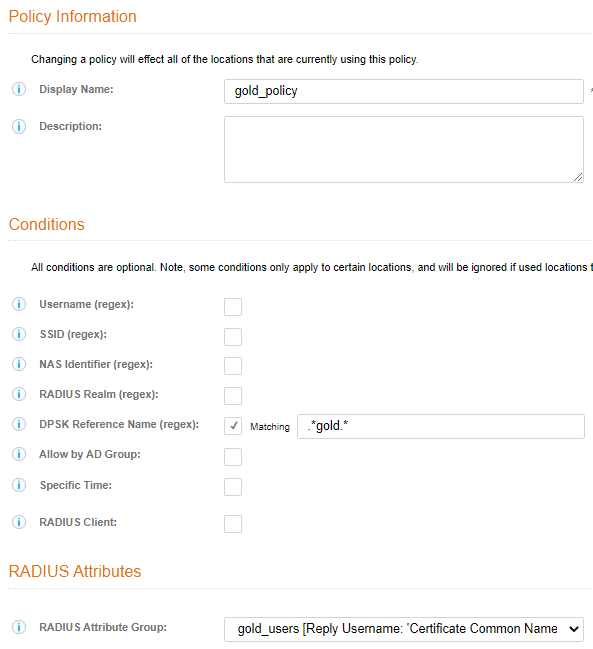
- Click on Save
- You should have 2 policies now:
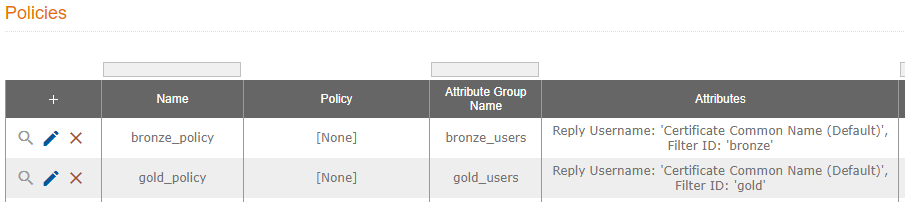
- Let’s apply the policies to your DPSK pools, click on Configuration | DPSK Pools
- Click the wrench beside you DPSK pool for the unit
- Click the RADIUS Policies tab
- Click on “+ Assign Policy” button
- Select the Bronze Policy and click on Save
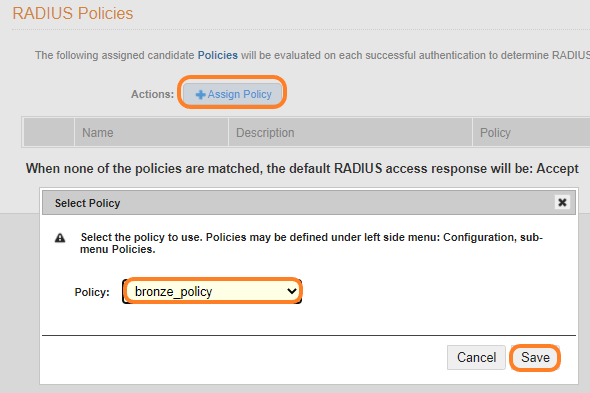
- Do the same for the gold policy
- You should have 2 policies now
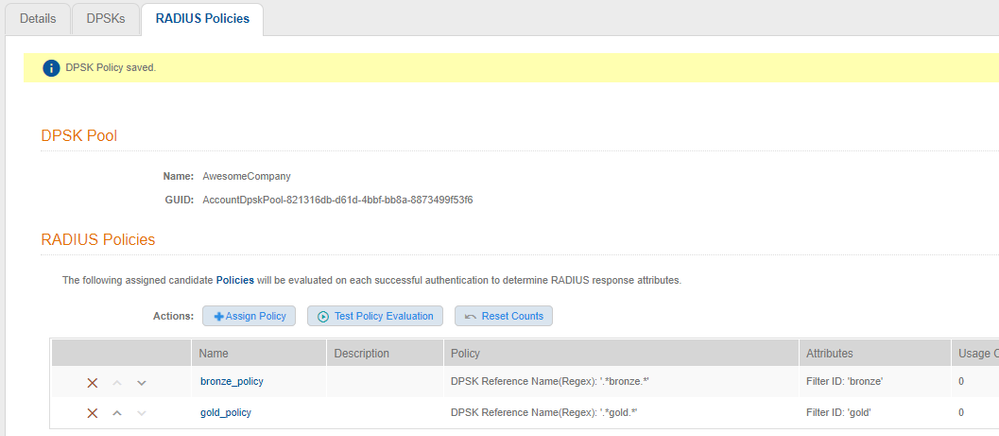
SmartZone:
Now that Cloudpath is setup with policies to return a different Filter ID to SmartZone, SmartZone has to be configured to take that value and apply it to a user role.
- In SmartZone, edit the Cloudpath Authentication Server
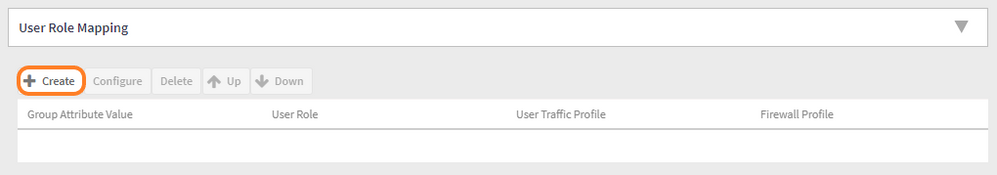
- Scroll to the bottom of the Cloudpath Authentication server window to “User Role Mapping”
- Click on the Create button
- The Group Attribute Value MUST match the Filter ID returned from Cloudpath (“bronze”):
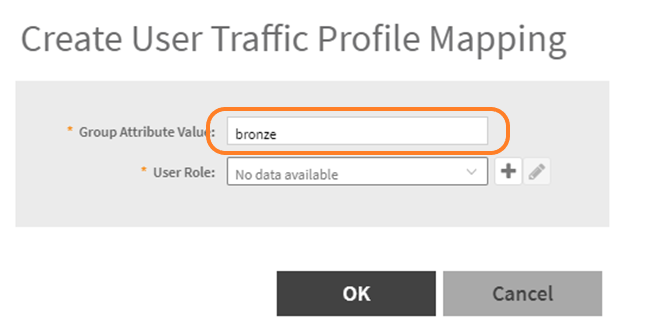
- Click on the + button to setup your parameters for the user.
- We are going to add a role name of “bronze_units” and add a firewall profile for 25 Mbps service
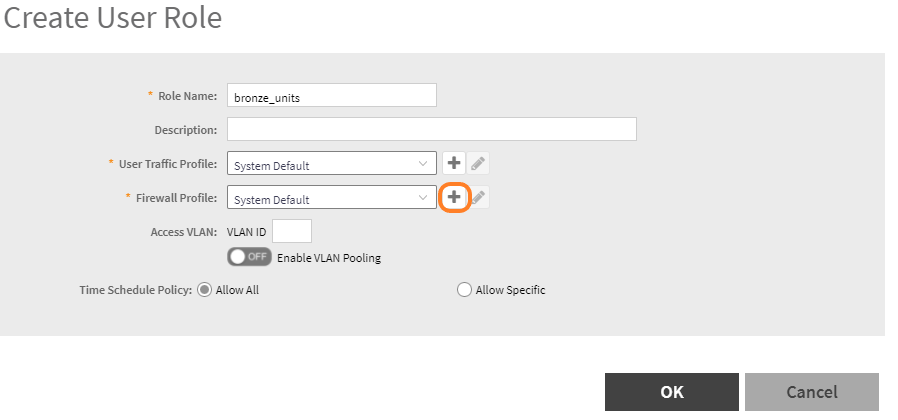
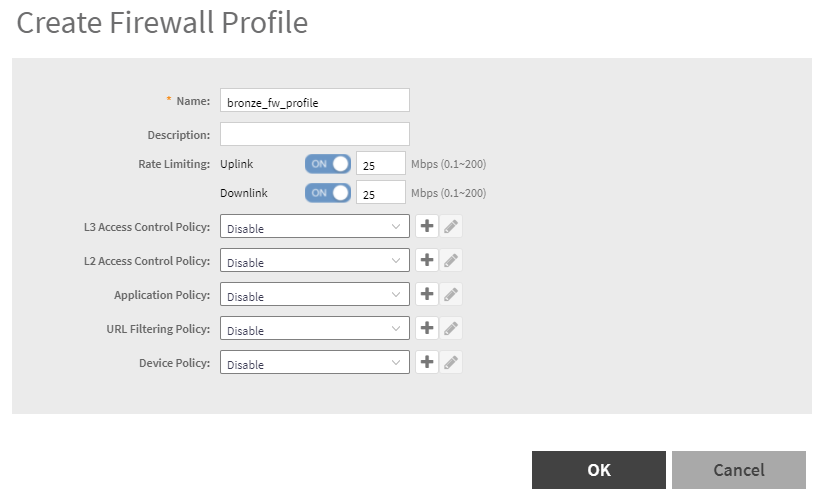
- Click on OK
- Click on OK
- Click on OK to return to the user Role Mapping screen
- Create another one for “gold” with 100 Mbps FW traffic profile
- Group attribute Value needs to match the “Filter ID” returned from Cloudpath, in our case “gold”
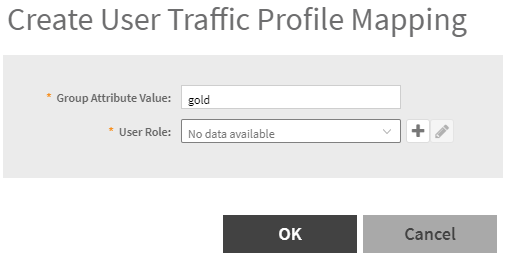
- Create a User Role and a FW profile like we did for bronze, but for 100 Mbps service
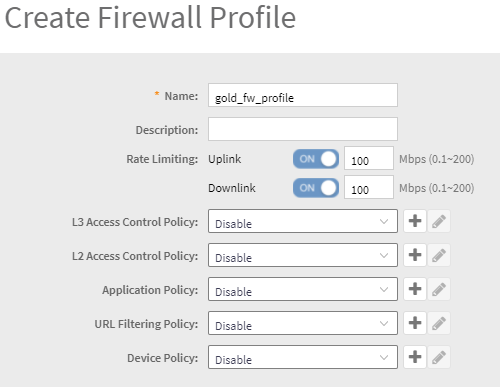
- Click on OK
- Click on OK
- Click on OK
- You should have two user-role mappings
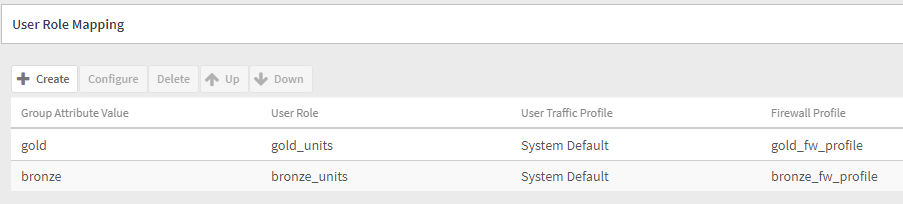
- Click on OK to close the Cloudpath Authentication Server.
Testing!
You can test this using the CCD of SmartZone:
- Example of a “bronze” unit returned Filter ID attribute:
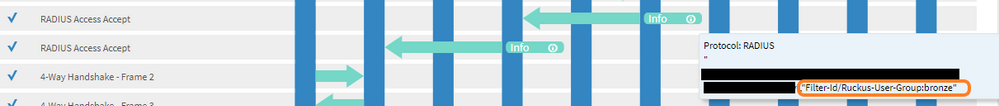
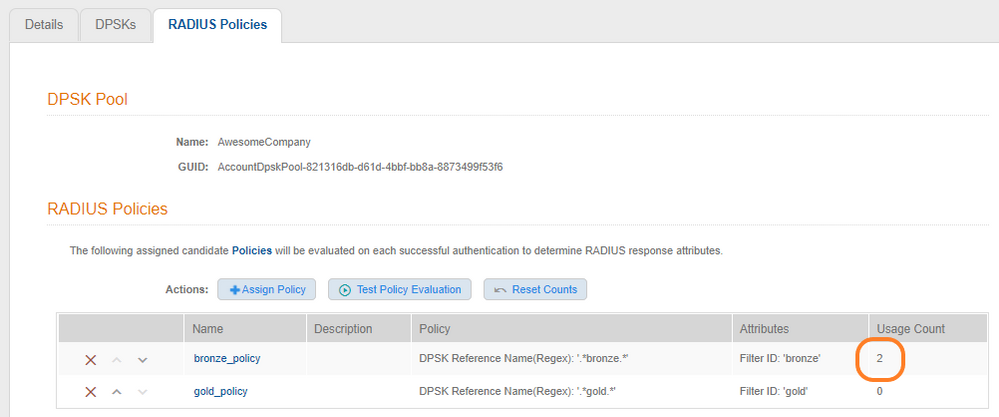
You can see the radius policy being hit in Cloudpath:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2021 08:06 AM
Hi Norbert,
Yes, you can use the Policy engine in Cloudpath to return a different user-role to SmartZone. You can use the UNIT name as the DPSK reference name in a policy. Using that policy, you can provide different Filter ID’s back to SmartZone.
I have a guide here, that will show an example of providing a Bronze level of service to users (25 Mbps up and down) vs Gold level of service (100 Mbps up and down) to users, but the user roles can be defined however you need to in SmartZone.
Let us use an example of a Bronze vs Gold service.
Overview:
In Cloudpath we will create units and pre-pend that unit with a service level bronze vs gold.
In Cloudpath we will create a policy that returns the Ruckus-User-Group as "bronze" to SmartZone and likewise for "Gold"
In SmartZone we will create two Traffic Profiles; Bronze giving 25 Mbps up and 25 Mbps down, and Gold giving 100 Mbps up and 100 Mbps down.
Cloudpath; create a bronze and a gold unit.
- Click on Managed Access | Property Management
- Click on the property that you want to change a unit to
- Click on Units Tab
- Create a Unit; pre-pend the word “bronze” in the unit number:

- Do the same for a “gold” unit:

If you look at the bronze unit, you can see that the DPSK reference name is named as <property_name>_<unit number>. We can use this value to build a RADIUS DPSK policy on:


In Cloudpath, let’s create 2 RADIUS policies to return the user-role to SmartZone
- Click on Configuration | Policies
- Click the RADIUS Attribute Groups Tab

- Click on Add RADIUS Attribute Group

- Create a attribute group that returns the “Filter ID” as “bronze”

- Click on Save
- Let’s do another policy for “gold”, so click on “Add RADIUS Attribute Group” again
- Create a gold attribute group that returns the “Filter ID” as “gold”

- Click on Save
- Click the Policies Tab | Add Policy

- Create a “bronze_policy” that returns the Bronze Attribute group that you just created. We are going to use the DPSK reference name for the Unit (remember, we pre-pended the word “bronze” to it):
- Make sure that you have a “.*” at the beginning and end, which means, match anything, then the word bronze, and match anything after that. This is REGEX, and I typically use a few different sites to test these things.
- Make sure that you select the correct RADIUS attribute group you just created for BRONZE
- Click on Save.
NOTE:
To test REGEX, I like to use “https://regex101.com”; this can help with syntax, example; lets make sure the regex I wrote will catch the DPSK reference name of the bronze unit and not the gold unit:

We can see that the REGEX will only match the first entry.
- Lets do a policy for “gold” users

- Click on Save
- You should have 2 policies now:

- Let’s apply the policies to your DPSK pools, click on Configuration | DPSK Pools
- Click the wrench beside you DPSK pool for the unit
- Click the RADIUS Policies tab
- Click on “+ Assign Policy” button
- Select the Bronze Policy and click on Save

- Do the same for the gold policy
- You should have 2 policies now

SmartZone:
Now that Cloudpath is setup with policies to return a different Filter ID to SmartZone, SmartZone has to be configured to take that value and apply it to a user role.
- In SmartZone, edit the Cloudpath Authentication Server
- Scroll to the bottom of the Cloudpath Authentication server window to “User Role Mapping”
- Click on the Create button

- The Group Attribute Value MUST match the Filter ID returned from Cloudpath (“bronze”):

- Click on the + button to setup your parameters for the user.
- We are going to add a role name of “bronze_units” and add a firewall profile for 25 Mbps service


- Click on OK
- Click on OK
- Click on OK to return to the user Role Mapping screen
- Create another one for “gold” with 100 Mbps FW traffic profile
- Group attribute Value needs to match the “Filter ID” returned from Cloudpath, in our case “gold”

- Create a User Role and a FW profile like we did for bronze, but for 100 Mbps service

- Click on OK
- Click on OK
- Click on OK
- You should have two user-role mappings

- Click on OK to close the Cloudpath Authentication Server.
Testing!
You can test this using the CCD of SmartZone:
- Example of a “bronze” unit returned Filter ID attribute:

You can see the radius policy being hit in Cloudpath:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2021 12:12 PM
Hello Christopher,
Thank you for your reply and detailed guide.
I did actually manage to create a similar solution. But I put all the units in the regex as a list, like this:
\b(?:unit1|unit2|unit3|unit4)\b
This will of course become an operational nightmare since you have to move users in and out of the different list when they change there subscription (could possible automate this with API). I was afraid that your solution would make a new DPSK for the tenant so they would need to change password (or change it back in the tenant portal). But i noticed that the DPSK also change name when you change unit name. So I prefer your solution. Thanks.