This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- Access Points
- Re: Isolating guest traffic
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Isolating guest traffic
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2014 06:23 AM
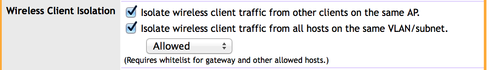
I have enabled a guest SSID on my network and I have selected isolated wireless client traffic from other clients on the same AP and isolated wireless client traffic from all hosts on the same VLAN/subnet. I added my printer to the white list, however guests trying to connect do not get an IP address and cannot connect to internet. So what I tried was adding the IP and MAC addresses of my AP's and router to the whitelist, and traffic is isolated from all other users, except they can see the access points and router. Is this normal behavior? Is full client isolation not possible?
My current software version is 9.7.0.0 build 220
My current software version is 9.7.0.0 build 220

4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2014 01:37 PM
Hi,
In my opinion you shouldn't need to whitelist the addresses of your AP's assuming that your router is also DHCP server or forwarder.
If you want to allow guests to use the WLAN it is strongly advised to put them in a separate VLAN. If your printer supports bonjour, you could then allow your guests to use the printer by configuring a bonjour gateway.
Regards,
Bas
In my opinion you shouldn't need to whitelist the addresses of your AP's assuming that your router is also DHCP server or forwarder.
If you want to allow guests to use the WLAN it is strongly advised to put them in a separate VLAN. If your printer supports bonjour, you could then allow your guests to use the printer by configuring a bonjour gateway.
Regards,
Bas
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2014 02:18 PM
Thanks for the reply. I've tried tagging the guest network with a different VLAN tag id, which does not seem to work. I am not well versed on VLAN. Do you have instructions?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2014 04:05 AM
Did you ever resolve guest printing? If so, how?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2014 02:27 PM
If you can provide me more info on your setup i could try to point you in the right direction.
Is your network vlan-aware?
What kind of equipment are you using? (brand and type of switch)
What kind of firewall/router are you using?
Before you want to set up a new VLAN you (at least) need:
- the VLAN to be configured on all switch ports where AP's are connected UNLESS you are tunnelling all traffic to the ZD. The latter is probably easier to configure and maintain as then you only need to configure the VLAN on the ZD interface.
- The VLAN to be terminated on a firewall/router
- A DHCP scope to be active on the VLAN
Is your network vlan-aware?
What kind of equipment are you using? (brand and type of switch)
What kind of firewall/router are you using?
Before you want to set up a new VLAN you (at least) need:
- the VLAN to be configured on all switch ports where AP's are connected UNLESS you are tunnelling all traffic to the ZD. The latter is probably easier to configure and maintain as then you only need to configure the VLAN on the ZD interface.
- The VLAN to be terminated on a firewall/router
- A DHCP scope to be active on the VLAN
Labels
-
Access points
1 -
AP Controller Connectivity
2 -
AP Management
6 -
AP migration
1 -
Authentication Server
1 -
cli
1 -
Client Management
1 -
Firmware Upgrade
2 -
Guest Pass
1 -
I live in
1 -
Installation
3 -
IP Multicast
1 -
mounting
1 -
Poe
3 -
Proposed Solution
2 -
R320 SLOW SPEED
1 -
R550
1 -
R610
1 -
R650
2 -
R750
2 -
Ruckus
1 -
Security
1 -
SmartZone
1 -
Solution Proposed
2 -
SSH
1 -
T710
1 -
Unleashed
1 -
User Management
1 -
Wireless Throughput
1 -
WLAN Management
1 -
ZoneDirector
1
- « Previous
- Next »

