This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- ZD
- Re: Ruckus and Palo Alto User-ID on Guest Network ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ruckus and Palo Alto User-ID on Guest Network (two different network addresses)
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2014 08:02 AM
Hi
We have a Ruckus zonedirector 1100 and a Palo Alto firewall.
We have 3 wi-fi networks set up. In simple terms, one internal, two on a different network.
The zone director has a 10.35.x.x address, the other networks have a 172.16.x.x address. One of the network's requires the user's to log in via there active directory credentials, and i am trying to set up the palo alto to monitor this network so i can see who has done what.
I’m assuming that I connect the palo alto to the ruckus syslog somehow, but I can’t work out how to monitor the 172.16 network.
The internal network is monitoring fine (but then again it should, as it's on the same network and part of the active directory network), but the guest network i can't seem to monitor.
Can anyone point me in the right direction please.
If you need any further information regarding my set up, please let me know
Thanks
Tony
We have a Ruckus zonedirector 1100 and a Palo Alto firewall.
We have 3 wi-fi networks set up. In simple terms, one internal, two on a different network.
The zone director has a 10.35.x.x address, the other networks have a 172.16.x.x address. One of the network's requires the user's to log in via there active directory credentials, and i am trying to set up the palo alto to monitor this network so i can see who has done what.
I’m assuming that I connect the palo alto to the ruckus syslog somehow, but I can’t work out how to monitor the 172.16 network.
The internal network is monitoring fine (but then again it should, as it's on the same network and part of the active directory network), but the guest network i can't seem to monitor.
Can anyone point me in the right direction please.
If you need any further information regarding my set up, please let me know
Thanks
Tony
16 REPLIES 16
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2014 04:31 AM
Hi
Thanks for your replies.
The Palo Alto can see the ruckus, and when I go to monitor tab on the firewall, it can see all the IP addresses on the 172.16 network, I just need to try and link it to the actual users that are logged in.
The Ruckus goes to my core switch, which is then connected to the Palo Alto.
we have set up on interface 4 on the palo alto (which is the internal link) a 4.99 for the vlan so the traffic goes through (see image as I don't think this makes a lot of sense)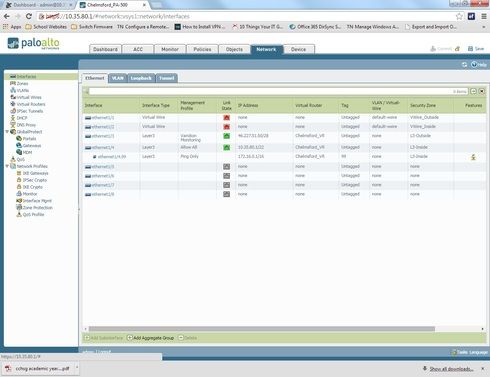
Other than the guest network, nothing else is on the network. The AD server that the ruckus uses is on the 10.35 network, and I can see that the ruckus identifies the user accounts ok etc, I'm just trying to find a way for the firewall to see it, so the same filtering rules can apply.
Thanks
Thanks for your replies.
The Palo Alto can see the ruckus, and when I go to monitor tab on the firewall, it can see all the IP addresses on the 172.16 network, I just need to try and link it to the actual users that are logged in.
The Ruckus goes to my core switch, which is then connected to the Palo Alto.
we have set up on interface 4 on the palo alto (which is the internal link) a 4.99 for the vlan so the traffic goes through (see image as I don't think this makes a lot of sense)

Other than the guest network, nothing else is on the network. The AD server that the ruckus uses is on the 10.35 network, and I can see that the ruckus identifies the user accounts ok etc, I'm just trying to find a way for the firewall to see it, so the same filtering rules can apply.
Thanks
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2014 04:32 AM
and I should add I have opened a call with Palo Alto as well on this matter, to see if they can assist me.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2014 04:05 PM
We are also interested in this. We may have to switch away from Ruckus if we can't get our Palo Alto to work well with it and identify our users.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2014 11:20 AM
First of all, are you using the 9.8+ version, right?
Why don't you install the PA User-ID agent in your Active Directory server?
We are fully integrated here with ZoneDirector 3000 version 9.8.2 and PA 5020 using PANOS 6.0.4.
Our most used WLAN is working with 802.1x auth (Radius), so we forward the ZD SYSLOG to a Windows Machine that is running the PA User ID Agent to collect the login information. It was really simple to configure with some simple Regex.
Other WLANs that uses WPA2/PSK but the users must use their AD login to authenticate on our Domain machines, we get the user authentication through the PA UserID agent running on our AD server. The same for our wired network.
You need to configure all of your agents on the PA FW as well.
If you wanna simply forward the syslog from ZD to PA, you need to enable "User-ID Syslog Listener-SSL,User-ID,User-ID Syslog Listener-UDP" on the management interface of your PAN FW. And then forward your syslog to the Management interface (IP) on PA.
Cheers.
Why don't you install the PA User-ID agent in your Active Directory server?
We are fully integrated here with ZoneDirector 3000 version 9.8.2 and PA 5020 using PANOS 6.0.4.
Our most used WLAN is working with 802.1x auth (Radius), so we forward the ZD SYSLOG to a Windows Machine that is running the PA User ID Agent to collect the login information. It was really simple to configure with some simple Regex.
Other WLANs that uses WPA2/PSK but the users must use their AD login to authenticate on our Domain machines, we get the user authentication through the PA UserID agent running on our AD server. The same for our wired network.
You need to configure all of your agents on the PA FW as well.
If you wanna simply forward the syslog from ZD to PA, you need to enable "User-ID Syslog Listener-SSL,User-ID,User-ID Syslog Listener-UDP" on the management interface of your PAN FW. And then forward your syslog to the Management interface (IP) on PA.
Cheers.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2015 08:00 AM
Hi
Thanks for this, i've been looking at this, and going to upgrade the firmware on the box to 9.8.2.0.15 either tonight or over the weekend, and i'll attempt to do this to see how it works.
I'll be trying the Syslog fowarding from the ZD to the PA in the first instance, and see where we go from there... I'll give you an update next week!
Thanks for this, i've been looking at this, and going to upgrade the firmware on the box to 9.8.2.0.15 either tonight or over the weekend, and i'll attempt to do this to see how it works.
I'll be trying the Syslog fowarding from the ZD to the PA in the first instance, and see where we go from there... I'll give you an update next week!
Labels
-
DHCP
1 -
IP lease
1 -
license snmp
1 -
Proposed Solution
1 -
Ruckus
1 -
server
1 -
VLAN
1 -
wap
1 -
zone director
1 -
ZoneDirector
1

