- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- Unleashed
- Two SSIDs to 2 different VLANs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Two SSIDs to 2 different VLANs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 01:28 PM
Hi guys,
This is my requirement:
-Corporate users to use corporate SSID to connect to internet
-Guests to use "guest" ssid to directly access the internet
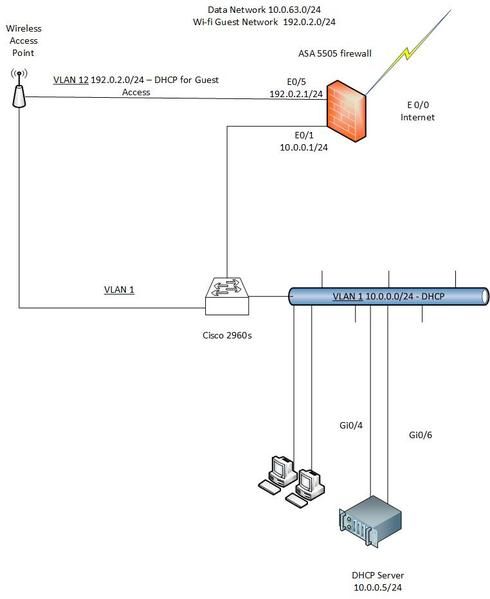
The setup (image attached):
-Ruckus unleashed r510 has a cable attached to an internal POE switch and another cable attached to a 5505 firewall (base license)
-The switch port where the AP connects is configured as access in VLAN1
-Internal network has DHCP enabled. This part seems to be working (internal users can obtain an IP from DHCP server and connect to the internet)
-asa has dmz interface in vlan 12 -this is where the AP connects for the guest network
-ASA firewall has dhcp server and pool configured, but when guest clients connect, they do not receive an IP
-NAT and ACLs from the dmz network to the internet already applied on the asa
Observations:
-Checking the mac addresses learned on the asa on the DMZ port reveals mac addresses from VLAN 1 (The asa has its inside interface on vlan 1). This is what surprises me, since the asa dmz port is assigned to vlan 12!!
I am requesting some help in finding out the minimum number of changes I need to make to ensure that the guests can safely access the internet.
Please help
-
200.12.10.5.234
1 -
AP Certificate error
1 -
AP Management
5 -
AP reporting
1 -
authentication fails
1 -
captive portal
1 -
Certificate
1 -
Client Management
1 -
DPSK
1 -
Guest Access
1 -
Guest Pass
1 -
Installation
1 -
IP Multicast
1 -
l2acl
1 -
LACP
1 -
laptop hp probook 430 g8
1 -
Mesh
1 -
Monitoring
1 -
Op
1 -
pfSense
1 -
R310
2 -
R550
1 -
R650
1 -
Security
1 -
Solution Proposed
3 -
SSID
1 -
temporarily blocked
1 -
Unleashed
6 -
User Management
1 -
Web UI
1 -
Wired Throughput
1 -
Wireless Throughput
2 -
WLAN
1 -
WLAN Management
1 -
WPA3
1 -
WPA3-Enterprise
1
- « Previous
- Next »

