This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- Cloudpath
- Re: CloudPath - manually generate & deploy device ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CloudPath - manually generate & deploy device certificate
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 03:15 AM
Hi,
Not sure if this is possible.
We have Ruckus vSZ with Cloudpath for on-boarding wireless devices. At the moment all BYOD users goes through the Cloudpath onboarding url >> enter their AD domain credentials which launches the NetworkWizardLoader-xxxx.exe and connects the user to the relevant SSID.
We have few non-domain/Intune managed devices shared by multiple users and would like to connect them to the wireless using the device based certificate. Is there a way on Cloudpath to generate\export the certificate manually which I can install it on the devices so that it connects automatically to the wireless ?
Or please advise of there is a better solution.
Any help on this would be much appreciated, thank you.
Not sure if this is possible.
We have Ruckus vSZ with Cloudpath for on-boarding wireless devices. At the moment all BYOD users goes through the Cloudpath onboarding url >> enter their AD domain credentials which launches the NetworkWizardLoader-xxxx.exe and connects the user to the relevant SSID.
We have few non-domain/Intune managed devices shared by multiple users and would like to connect them to the wireless using the device based certificate. Is there a way on Cloudpath to generate\export the certificate manually which I can install it on the devices so that it connects automatically to the wireless ?
Or please advise of there is a better solution.
Any help on this would be much appreciated, thank you.
14 REPLIES 14
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 08:04 AM
thank you, Is there a help guide or knowledge-base article somewhere I can follow ?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 08:27 AM
Here are a couple of screenshots to illustrate... If you need further assistance with this, please open a ticket with Ruckus Support.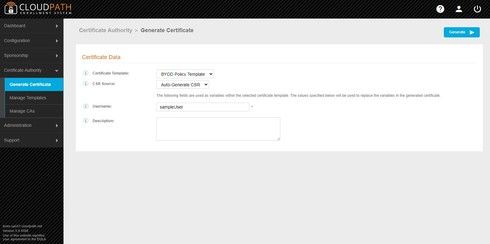
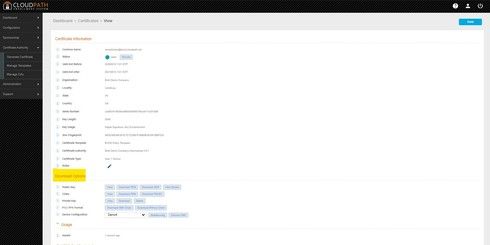


Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 08:44 AM
thank you Brett, If i generate a certificate based on the existing BYOD template we use here, use one of the AD account on Username field, can I apply the same certificate to multiple devices ?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 08:48 AM
Well, you'd use the same template but not the same cert you 'd generate a different cert for each entered username
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 09:08 AM
You could apply the same cert to different devices, but you would then not be able to uniquely distinguish them. It is not required that you use an AD account user for the Username field. That just establishes the username as part of the certificate's common name. When challenging users in a workflow using an AD authentication server, that is merely authorizing the user to be issued a cert... and that is the extent of AD's role. Subsequent connections are authenticated with the cert, and not AD at all. (in EAP-TLS use case, anyway...)

