This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- ZD
- Re: How to integrate between Ruckus and Palo Alto
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to integrate between Ruckus and Palo Alto
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2014 09:23 AM
Hi everyone,
I have some problem about how to integrate between Ruckus and Palo Alto.
The Palo Alto need the Ruckus syslog message which contain the IP and username for creating the policy but I tried to set Ruckus to send the syslog to Palo Alto but in the syslog messages are contain username and MAC address.
Do you have any idea how to set the Ruckus to send IP and username in syslog message of if you have any way for integration, please advice me.
I have some problem about how to integrate between Ruckus and Palo Alto.
The Palo Alto need the Ruckus syslog message which contain the IP and username for creating the policy but I tried to set Ruckus to send the syslog to Palo Alto but in the syslog messages are contain username and MAC address.
Do you have any idea how to set the Ruckus to send IP and username in syslog message of if you have any way for integration, please advice me.
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2014 08:24 PM
Helo, I forwarded the syslog from ZD to PA's Management IP (the syslog listener was enabled), but where to configure the syslog event filter?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2014 05:30 PM
I don think the ZD recognize the radius authenticated user's IP.
ZD only recognize the MAC address and Username, the Username is tie to the MAC address even in the event logs, cli command "show current-active-client" doesn't tell you any information about the IP address.
While the radius authentication is happening, in that context, there is no IP recognition involve between client, ZD and radius server.
So, my point is, if ZD itself can't recognize the authenticated user's IP and provided insufficient information, how can the PanOS recognize it?
Please correct/advise me if i'm wrong. Feel free to email me too, nick_khor@hotmail.com.
Thanks.
ZD only recognize the MAC address and Username, the Username is tie to the MAC address even in the event logs, cli command "show current-active-client" doesn't tell you any information about the IP address.
While the radius authentication is happening, in that context, there is no IP recognition involve between client, ZD and radius server.
So, my point is, if ZD itself can't recognize the authenticated user's IP and provided insufficient information, how can the PanOS recognize it?
Please correct/advise me if i'm wrong. Feel free to email me too, nick_khor@hotmail.com.
Thanks.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2015 08:11 AM
Hey Nick,
Actually after 9.8 if you enabled on the "Debug Logs" the Client Association option, the ZD start to log the client association with some messages with the client login information and IP even if it uses Radius or Captive Portal.
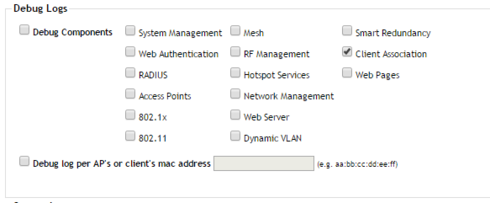
Don't forget to enable syslog forwarding on ZD to the PA's MGMT IP or User-ID agent IP.
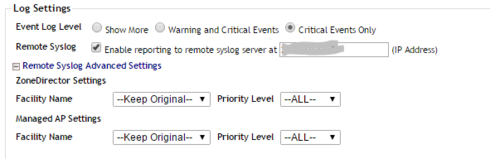
I don't recall the exactly message, but I discovered it using an external syslog (on linux) receiving the messages. Do a grep filtering for "sta_name" or "operation=add"
At PA you need to enabled the MGMT interface to receive the message and then create a syslog filter on "Device" -> "User Identification" -> tab "User Mapping" click on the little engine on the right corner, and then the tab syslog filters (hidden right?)
There you can create a regex filter to recognize those messages.
Here we created a filter like this:
Type: Regex Identifier
Event Regex: operation=(update|add){1}
Username Regex: sta_name(?:=.*\\|=)([0-9]+); (our users login are just numbers)
Address Regex: sta_ip=(10\.[0-9]+\.[0-9]+\.[0-9]+);
And you need to add a Server Monitoring on PA's as well for the ZD, just right bellow on the User Mapping tab.
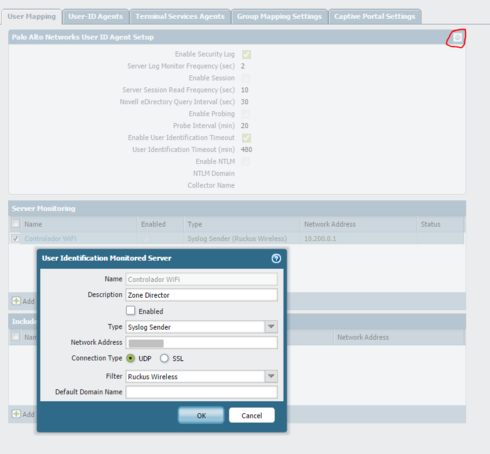
It worked for us configuring on PA but we want it better.
As I said, after we tested that, we were sure that PA was identifying the user authentication.. we implemented an external PA User-ID agent to receive the message from the Zone Director and configured the same filter on it, with that our PA's mgmt interface don't need to be listen to all those syslog message and just get the information the PA need already filtered by the agent.
Cheers.
ps: Sorry for the delay, I was on vacation!
Actually after 9.8 if you enabled on the "Debug Logs" the Client Association option, the ZD start to log the client association with some messages with the client login information and IP even if it uses Radius or Captive Portal.

Don't forget to enable syslog forwarding on ZD to the PA's MGMT IP or User-ID agent IP.

I don't recall the exactly message, but I discovered it using an external syslog (on linux) receiving the messages. Do a grep filtering for "sta_name" or "operation=add"
At PA you need to enabled the MGMT interface to receive the message and then create a syslog filter on "Device" -> "User Identification" -> tab "User Mapping" click on the little engine on the right corner, and then the tab syslog filters (hidden right?)
There you can create a regex filter to recognize those messages.
Here we created a filter like this:
Type: Regex Identifier
Event Regex: operation=(update|add){1}
Username Regex: sta_name(?:=.*\\|=)([0-9]+); (our users login are just numbers)
Address Regex: sta_ip=(10\.[0-9]+\.[0-9]+\.[0-9]+);
And you need to add a Server Monitoring on PA's as well for the ZD, just right bellow on the User Mapping tab.

It worked for us configuring on PA but we want it better.
As I said, after we tested that, we were sure that PA was identifying the user authentication.. we implemented an external PA User-ID agent to receive the message from the Zone Director and configured the same filter on it, with that our PA's mgmt interface don't need to be listen to all those syslog message and just get the information the PA need already filtered by the agent.
Cheers.
ps: Sorry for the delay, I was on vacation!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2015 05:31 PM
Helo Odilo,
Thanks for that tips. Late is better than never ;)
I found this out from the syslog
"Jan 14 08:43:47 stamgr: stamgr_send_log_v4():operation=add;seq=3;sta_ip=192.168.XX.XX;sta_mac=a0:88:69:XX:XX:XX;zd/ap=6c:aa:b3:XX:XX:XX/84:18:3a:XX:XX:XX;sta_ostype=Windows 7/Vista;sta_name=host/LP-XXX.Domain.local;stamgr_handle_remote_ipc "
operation=add;
sta_ip=192.168.XX.XXX;
sta_name=host/LP-XXX.Domain.local;
---
That was a Computer Authentication log, the user authentication log was not appear in the syslog, i will need some times to check it out.
Btw, thanks for your guide!
Thanks for that tips. Late is better than never ;)
I found this out from the syslog
"Jan 14 08:43:47 stamgr: stamgr_send_log_v4():operation=add;seq=3;sta_ip=192.168.XX.XX;sta_mac=a0:88:69:XX:XX:XX;zd/ap=6c:aa:b3:XX:XX:XX/84:18:3a:XX:XX:XX;sta_ostype=Windows 7/Vista;sta_name=host/LP-XXX.Domain.local;stamgr_handle_remote_ipc "
operation=add;
sta_ip=192.168.XX.XXX;
sta_name=host/LP-XXX.Domain.local;
---
That was a Computer Authentication log, the user authentication log was not appear in the syslog, i will need some times to check it out.
Btw, thanks for your guide!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2015 07:20 AM
Good!
We did some filter on radius as well, to permit only user + pass authentication, so we don't have our domain machines authenticating there. That way we can "assure" (ok maybe 99.99% of the time) that the user authenticating is the real user not just a machine that could be used by other one.
No problem, glad I can help :)
Good luck!
Cheers.
We did some filter on radius as well, to permit only user + pass authentication, so we don't have our domain machines authenticating there. That way we can "assure" (ok maybe 99.99% of the time) that the user authenticating is the real user not just a machine that could be used by other one.
No problem, glad I can help :)
Good luck!
Cheers.
Labels
-
DHCP
1 -
IP lease
1 -
license snmp
1 -
Proposed Solution
1 -
Ruckus
1 -
server
1 -
VLAN
1 -
wap
1 -
zone director
1 -
ZoneDirector
1

