This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Self-Help
- Admin and Licensing
- Access Points
- ICX Switches
- Edge
- RUCKUS One
- RUCKUS AI
- Cloudpath
- RWG
- SZ / vSZ
- Unleashed
- IoT
- RND
- Apps and SPoT
- SCI
- Best Practices
- ZD
- RUCKUS Self-Help
- Admin and Licensing
- Access Points
- ICX Switches
- Edge
- RUCKUS One
- RUCKUS AI
- Cloudpath
- RWG
- SZ / vSZ
- Unleashed
- IoT
- RND
- Apps and SPoT
- SCI
- Best Practices
- ZD
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Technologies
- RUCKUS Self-Help
- Admin and Licensing
- Access Points
- ICX Switches
- Edge
- RUCKUS One
- RUCKUS AI
- Cloudpath
- RWG
- SZ / vSZ
- Unleashed
- IoT
- RND
- Apps and SPoT
- SCI
- Best Practices
- ZD
- RUCKUS Self-Help
- Admin and Licensing
- Access Points
- ICX Switches
- Edge
- RUCKUS One
- RUCKUS AI
- Cloudpath
- RWG
- SZ / vSZ
- Unleashed
- IoT
- RND
- Apps and SPoT
- SCI
- Best Practices
- ZD
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- Community Services
- To Be Moved
- Re: Microsoft Surface, just not compatible with Ru...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Microsoft Surface, just not compatible with Ruckus?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 12:17 PM
Seeing this at three different locations - customers show up with an MS Surface device and they simply cannot log in. No interesting logs in the ZD, I'll see one log of "too many authentication failures" and then even hours or days later ZERO logs for the client. And on the client side, this incredibly unhelpful error:
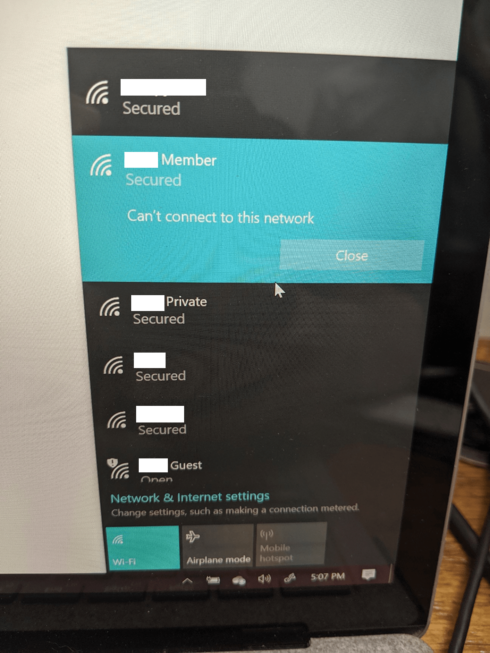
All the networks shown there are served from the same APs.
We even see this on clients running Unleashed setups.
How is there not a KB article about this?

All the networks shown there are served from the same APs.
We even see this on clients running Unleashed setups.
How is there not a KB article about this?
20 REPLIES 20
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 01:21 PM
I did our companies initial analysis via Wireshark (because the rejection happens on the client's end, without attempting to authenticate to the network, hence no logs), and found that the devices were essentially saying we support R but only part of it. so I simply removed roaming from the sites with affected clients and asked for Local IT to remediate by Rolling drivers back. I spoke to one of them a few minutes ago, and he said " uninstall the wireless NIC, delete the driver when it prompts me to, then reboot. Works after that."
I do not recall putting R back on the SSID's his SP's are on, so his guidance may or may not be flawed.
I do not recall putting R back on the SSID's his SP's are on, so his guidance may or may not be flawed.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 01:37 PM
OK, this is very helpful. Going to try the config changes. I'm about 90% sure the onsite tech already removed the device and re-added. We don't like touching client devices too much, so we didn't have the option to sniff with wireshark, but glad you did!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 01:44 PM
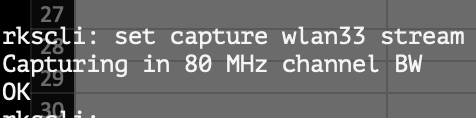
You can grab Wireshark directly from the AP.
- Log in to the AP
- run command 'get wlanlist'
- id your WLAN number (in my case it's wlan33)
- run command 'set capture wlan33 stream' remember, your WLAN may be different. using a copy of Wireshark, or favorite equivalent
- open interfaces, remote interfaces, hit the plus or 'add'
- type in the IP of the target AP, the port is 2002 (globe)
- a list of new interfaces will appear, select wlan33 and leave out everything else for the moment.
- Hit start.
- Profit!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 01:54 PM
Wow. OK, I didn't even know there was a CLI available on the individual APs. So yeah. 🙂
A few quick questions if you'll indulge me:
A few quick questions if you'll indulge me:
- you noted that there were no logs of the Surface because it had given up attempting to auth to an "incompatible" network - just confirming in this case the sniffing at the AP would NOT give me the info I need, correct?
- in the above example, the "set capture ..." command is telling the AP to open a socket (which defaults to 2002) and it's dumping a tcpdump-like stream to whatever connects to that socket?
- this is a good argument for a testing WLAN that's turned on for just this sort of troubleshooting I suppose
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2019 02:13 PM
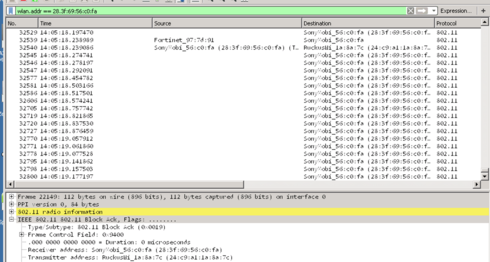
you noted that there were no logs of the Surface because it had given up attempting to auth to an "incompatible" network - just confirming in this case the sniffing at the AP would NOT give me the info I need, correct?
Incorrect. in the following screencap, you can see the Wlan.addr filter used to specify the mac address of an android mule used primarily to test cloud path onboarding. The SONY is not connected to this R610 in any way, instead, it's attached to my personally owned R500.
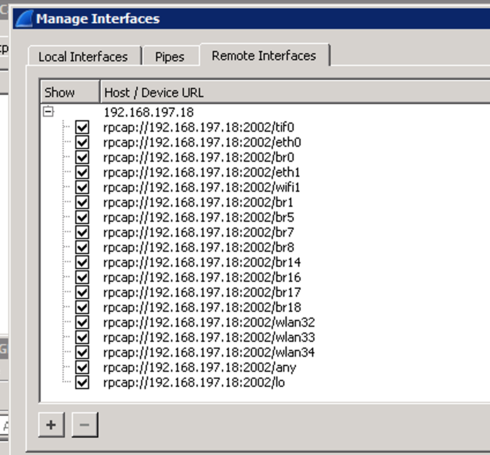
in the above example, the "set capture ..." command is telling the AP to open a socket (which defaults to 2002) and it's dumping a tcpdump-like stream to whatever connects to that socket?
yes, Here is a screencap of my Mule AP's remote interfaces after running the set capture command.
this is a good argument for a testing WLAN that's turned on for just this sort of troubleshooting I suppose
Yes, everyone makes mistakes, even M$oft. And when it does happen, it's always a doozie.
Depending on your load, PI might be a touch lightweight for any REAL diagnostic. In my experience (PI3 B +) Drive write times leave too much to be desired, and as such make poor IPERF servers. as for tcpdump, my setup only seems to be only able to do about 25-30mb/s before losing packets. That said, there is a new PI4 out with PoE. as soon as the USB-C stuff is fixed on the boards, I plan to restart my Pi projects with that platform (4gb for the win!)
Good luck with Aruba!
Incorrect. in the following screencap, you can see the Wlan.addr filter used to specify the mac address of an android mule used primarily to test cloud path onboarding. The SONY is not connected to this R610 in any way, instead, it's attached to my personally owned R500.

in the above example, the "set capture ..." command is telling the AP to open a socket (which defaults to 2002) and it's dumping a tcpdump-like stream to whatever connects to that socket?
yes, Here is a screencap of my Mule AP's remote interfaces after running the set capture command.

this is a good argument for a testing WLAN that's turned on for just this sort of troubleshooting I suppose
Yes, everyone makes mistakes, even M$oft. And when it does happen, it's always a doozie.
Depending on your load, PI might be a touch lightweight for any REAL diagnostic. In my experience (PI3 B +) Drive write times leave too much to be desired, and as such make poor IPERF servers. as for tcpdump, my setup only seems to be only able to do about 25-30mb/s before losing packets. That said, there is a new PI4 out with PoE. as soon as the USB-C stuff is fixed on the boards, I plan to restart my Pi projects with that platform (4gb for the win!)
Good luck with Aruba!