This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- RUCKUS Forums
- RUCKUS Technologies
- Cloudpath
- VLAN Pool AAA override
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VLAN Pool AAA override
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2019 04:25 PM
I have two certificate templates configured in CloudPath that have a filter ID assigned to them. One of them does what I want and one doesn't (one that works correctly was setup a while back, broken one I am working on now). What happens with the working one is my 802.1x SSID is configured for Dynamic VLAN (AAA Override) . On the controller I have a two user roles created that assign a VLAN pool to that role. Also on the controller under Proxy Authentication where the settings for cloud path are I have the two attributes map to the user role. The one I setup previously correctly assigns the VLAN pool and traffic policy. The new one does not, the client ends up getting a DHCP address from the native vlan. I have a feeling there is something I missed on the controller side but I can't find it.
1 REPLY 1
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 12:14 PM
I just was on a call with support and they had me put the vlans in a list in the CloudPath cert template like in the attached screenshot.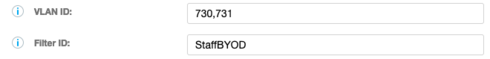
These are the two vlans that are in the pool assigned to the StaffBYOD user role. The Filter ID is what I use to map to the user role in SZ100. This user role has a traffic profile and vlan pool assigned to it and the traffic profile is being applied just not the vlan pool. After adding this in Cloudpath it looks to me like all devices are getting an IP from vlan 730. I have two other cert templates that use a different FilterID/User Role and they correctly apply the vlan pool without having to specify anything in Cloudpath for vlan ID. I asked why those worked and this one doesn't but didn't get an answer. I don't think the answer I got from support of adding the vlans in a list like this above is the answer. Any ideas?

These are the two vlans that are in the pool assigned to the StaffBYOD user role. The Filter ID is what I use to map to the user role in SZ100. This user role has a traffic profile and vlan pool assigned to it and the traffic profile is being applied just not the vlan pool. After adding this in Cloudpath it looks to me like all devices are getting an IP from vlan 730. I have two other cert templates that use a different FilterID/User Role and they correctly apply the vlan pool without having to specify anything in Cloudpath for vlan ID. I asked why those worked and this one doesn't but didn't get an answer. I don't think the answer I got from support of adding the vlans in a list like this above is the answer. Any ideas?

