- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- RUCKUS Self-Help
- How to limit admin login based on User Group using...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to limit admin login based on User Group using Microsoft LDAP on Sz/vSZ(e.g. Guestpass Access)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2023 07:56 PM - edited 11-14-2023 05:29 PM
This article explains how to limit admin login based on User Group using Microsoft LDAP on Sz/vSZ, in this example we will cover Guestpass Access.
SUMMARY:
Customer wants to use Microsoft LDAP to allow admin login only for Guestpass generation based on User Group using Microsoft LDAP on Sz/vSZ.
Validation has been done 6.1.1.X firmware version.
We will cover below setting from Microsoft AD Perspective.
User Group Mapping
How to find DN pattern
from SZ/vSZ perspective
Administrator
Group
AAA
Search filter
Microsoft AD User Group setting.
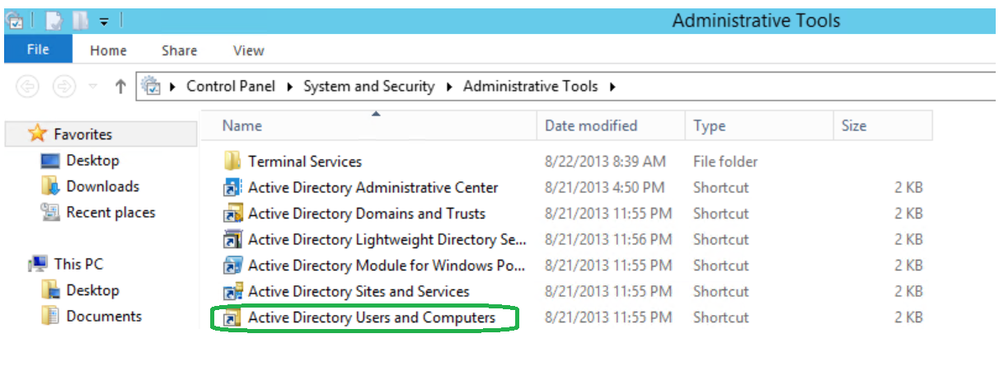
From Microsoft AD open Administrative Tools>>>Active Directory Users and Computer.
User Group Mapping
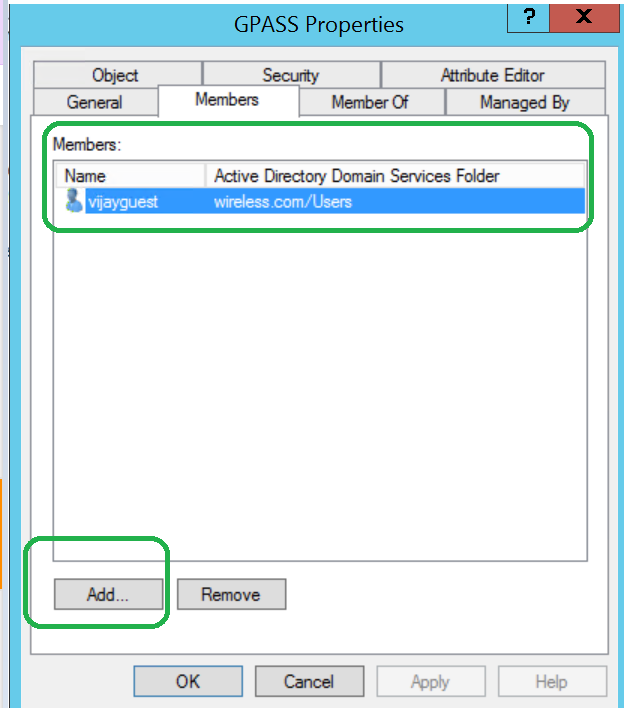
In Active Directory Users and Computer select the group which needs to allowed for Guestpass generation and Map Members to it with the Add button.
e.g.
GPASS is the Group as below.
vijayguest is the member mapped to it.
How to find right DN pattern (Group and User)
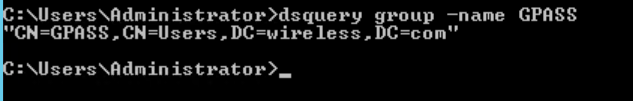
Open command Prompt and run below command one by one.
("dsquery group -name <groupname>")
("dsquery group -name <username>")
<groupname> is variable "GPASS" as in below example
<username> is variable "Administrator" as in below example
This DN pattern will be used in the AAA server setting for Search filter and Administrator Domain.
Administrator
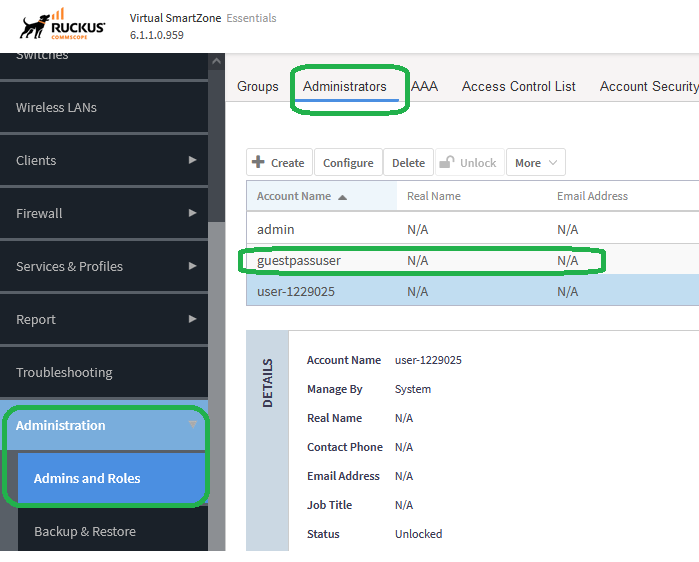
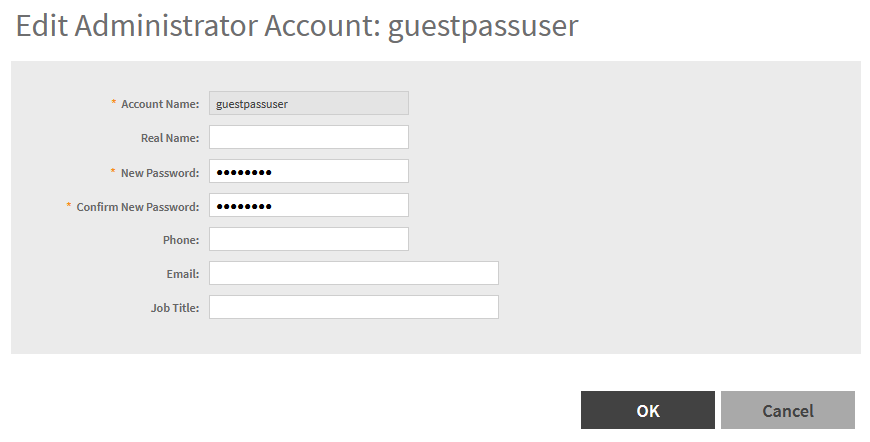
Create an administrator user on SZ/vSZ GUI>>>Administration>>>Admin and Roles>>>Administrator
(guestpassuser for example, this is a dummy user).
Groups
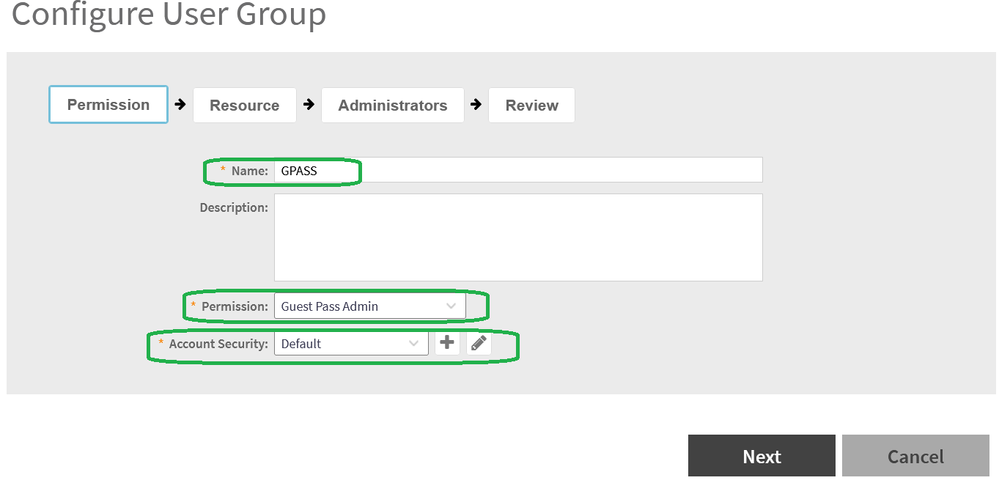
Create an Group on SZ/vSZ GUI>>>Administration>>>Admin and Roles>>>Groups
With below settingas example.
Permission
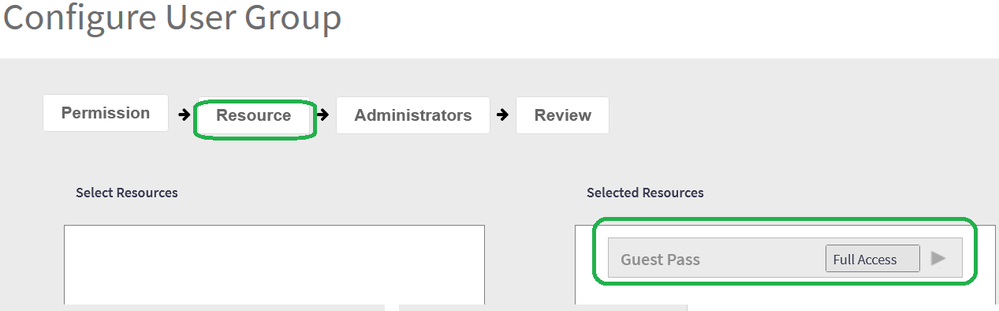
Resources
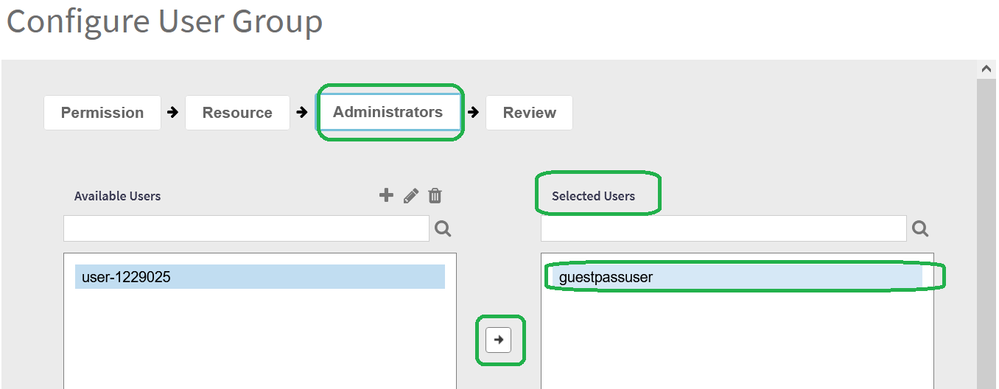
Administrator
Move user to the right with the arrow to map to the group.
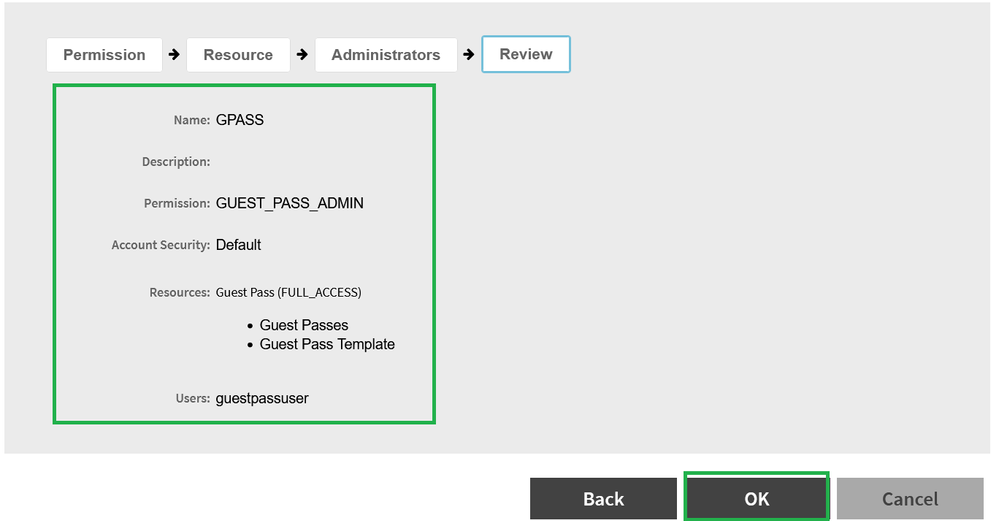
Review
Review the setting and click OK.
AAA
Create an AAA LDAP server on SZ/vSZ GUI>>>Administration>>>Admin and Roles>>>AAA
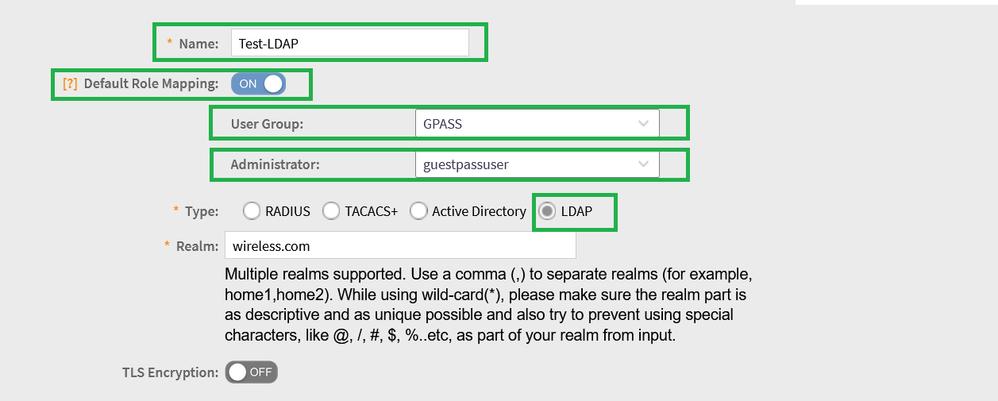
Turn on Default Role Mapping
Select User Groupcreated as above(GPASS)
Select Administrator created as above(guestpassuser)
Select LDAP from the checkbox
Fill Realm as AD domain (wireless.com for example)
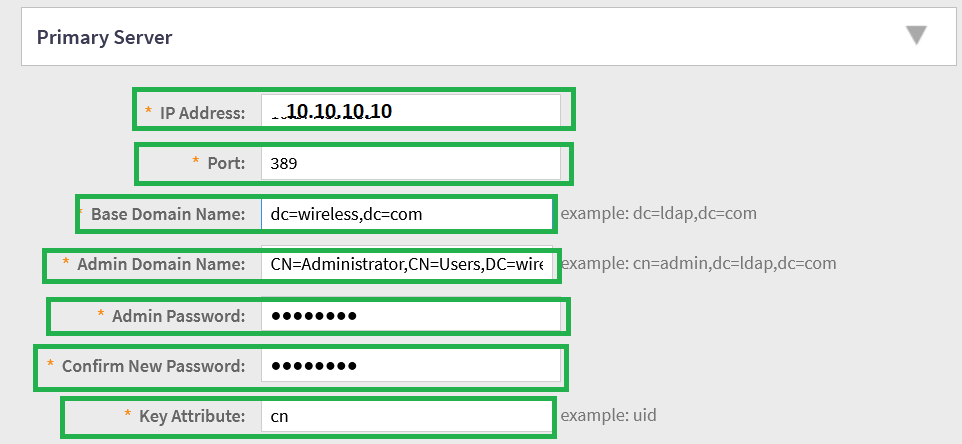
IP address of Server and Port number (389 for LDAP)
Base Doamin(exact domain) and Admin Domain based on ds query for Administrator.
Type LDAP Administrator password and Confirm password.
Fill Key Attribute: "cn"
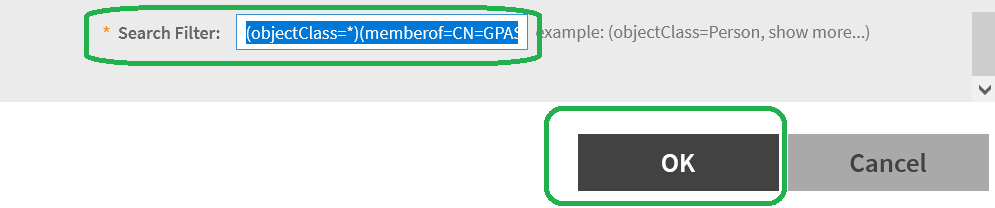
Search filter
Search Filter in the below format and Click OK to Save.(based on the dsquesy results, max character limit in the box is 64)
(objectClass=*)(memberof=CN=GPASS,CN=Users,DC=wireless,DC=com)
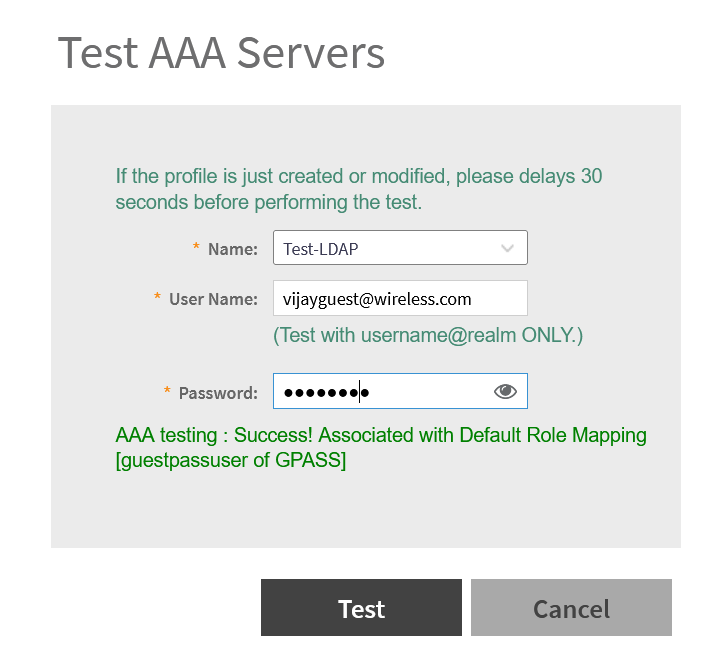
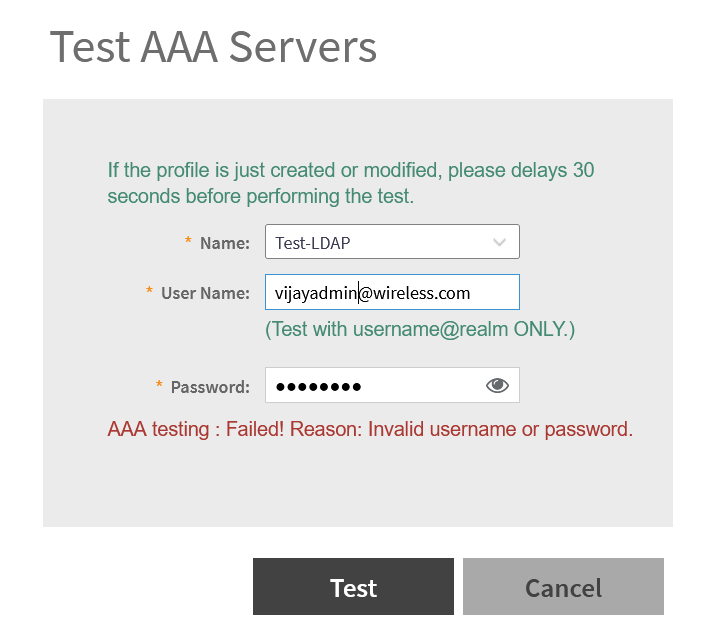
Test AAA Server
AD User part of GPASS group will pass authentication.
AD User not a member of GPASS group will fail to authenticate.
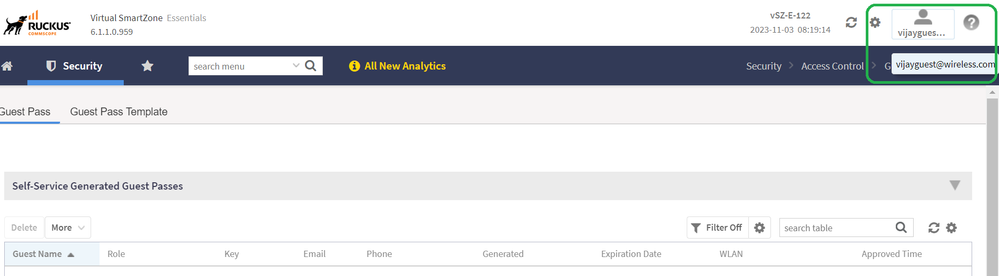
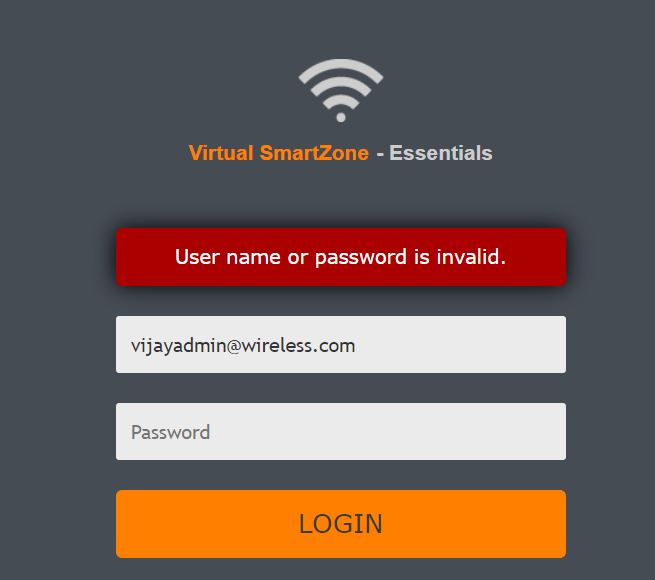
Once tested verify login from the admin page as well.
LDAP User group authentication will succeed (GPASS in this example).
Authentication will fail for non LDAP Group User (GPASS in this example).
Staff Technical Support Engineer
CCNA RnS | CCNA Wireless | CWNA | RASZA | Meraki CMNO | RACPA
- Labels:
-
RUCKUS Self-Help
-
SmartZone or vSZ
-
AAA
2 -
Access points
47 -
Analytics
3 -
AP Certificate error
1 -
AP Controller Connectivity
5 -
AP Management
8 -
AP migration
1 -
AP reporting
1 -
API
2 -
Authentication Server
1 -
Client Management
1 -
Cloud
20 -
Cloud ICX
1 -
Cloudpath
22 -
Deployment
2 -
Firmware Recommendation
1 -
Firmware Upgrade
5 -
Guest Access
2 -
ICX
70 -
ICX Switch Management
7 -
Installation
4 -
IoT
1 -
Licensing
1 -
Mobile Apps
3 -
Monitoring
1 -
Poe
2 -
RADIUS
2 -
Ruckus Cloud
1 -
RUCKUS Self-Help
204 -
Security
6 -
SmartZone or vSZ
63 -
Stacking
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
UMM
2 -
Unleashed
14 -
User Management
1 -
Venue Management
1 -
Wired Throughput
2 -
Wireless Throughput
1 -
WLAN Management
5 -
ZoneDirector
15
- « Previous
- Next »