- Community
- RUCKUS Technologies
- RUCKUS Lennar Support
- Community Services
- RTF
- RTF Community
- Australia and New Zealand – English
- Brazil – Português
- China – 简体中文
- France – Français
- Germany – Deutsch
- Hong Kong – 繁體中文
- India – English
- Indonesia – bahasa Indonesia
- Italy – Italiano
- Japan – 日本語
- Korea – 한국어
- Latin America – Español (Latinoamérica)
- Middle East & Africa – English
- Netherlands – Nederlands
- Nordics – English
- North America – English
- Poland – polski
- Russia – Русский
- Singapore, Malaysia, and Philippines – English
- Spain – Español
- Taiwan – 繁體中文
- Thailand – ไทย
- Turkey – Türkçe
- United Kingdom – English
- Vietnam – Tiếng Việt
- EOL Products
- RUCKUS Forums
- RUCKUS Technologies
- RUCKUS Self-Help
- Cloudpath Persistent XSS and CSRF Vulnerability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cloudpath Persistent XSS and CSRF Vulnerability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2023 10:11 AM - edited 10-16-2023 10:17 AM
Hello All,
This is an important security announcement for Cloudpath.
What is the issue?
A vulnerability in the web-based interface of the RUCKUS Cloudpath product could allow a remote, unauthenticated attacker to execute persistent XSS and CSRF attacks against an user of the admin management interface. A successful attack, combined with a certain admin activity, could allow the attacker to gain full admin privileges on the exploited system.
What action should I take?
Updating the software to its most recent version, as detailed below, will resolve the vulnerability. Since this is a high severity vulnerability, all customers are strongly encouraged to apply the update at the earliest opportunity.
What is the impact on RUCKUS products?
The following table describes the vulnerable products and software versions and the recommended actions.
Product | Vulnerable Release | Resolution | Release Date |
Cloudpath | Version 5.12 build 5538 or earlier
| Upgrade to Version 5.12 build 5550 or later
| Oct 13th, 2023 |
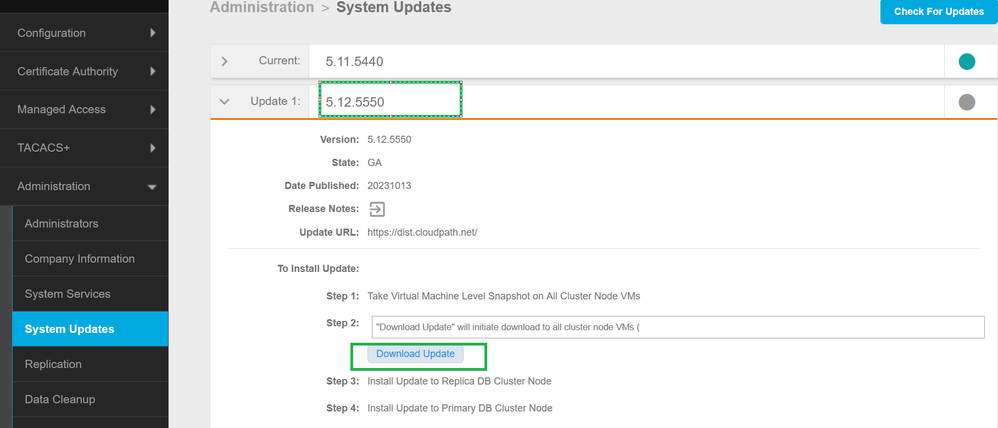
New version is available for download on all the on-premises Cloudpath, Hosted Cloudpath are already patched with the fix.
Administrator>>>System Updates>>>Download Update.
When will this RUCKUS Security Advisory be publicly posted?
RUCKUS will release the initial security advisory to customers on 10/16/2023, follow below link for the official Security Advisory.
https://support.ruckuswireless.com/security_bulletins/
Staff Technical Support Engineer
CCNA RnS | CCNA Wireless | CWNA | RASZA | Meraki CMNO | RACPA
- Labels:
-
Cloudpath
-
RUCKUS Self-Help
-
AAA
2 -
Access points
48 -
Analytics
3 -
AP Certificate error
1 -
AP Controller Connectivity
5 -
AP Management
8 -
AP migration
1 -
AP reporting
1 -
API
2 -
Authentication Server
2 -
Client Management
1 -
Cloud
20 -
Cloud ICX
1 -
Cloudpath
23 -
Cluster synchronization
1 -
Deployment
2 -
Firmware Recommendation
1 -
Firmware Upgrade
5 -
Guest Access
2 -
ICX
73 -
ICX Switch Management
7 -
Installation
5 -
IoT
1 -
Licensing
1 -
Mobile Apps
2 -
Monitoring
1 -
Poe
2 -
RADIUS
2 -
Ruckus Cloud
1 -
RUCKUS Self-Help
209 -
Security
6 -
SmartZone or vSZ
64 -
Stacking
1 -
SZ ICX Connectivity
1 -
Traffic Management-
1 -
UMM
3 -
Unleashed
15 -
User Management
1 -
Venue Management
1 -
Wired Throughput
2 -
Wireless Throughput
1 -
WLAN Management
5 -
ZoneDirector
15
- « Previous
- Next »